Duo Security - idemeum agent integration
— Nik Pot

JIT computer access
When Duo Security agent is installed on a Windows workstation, it disables all credential providers except the native Windows password credential provider. However, there is a way to enable excluded credential providers via the registry.
When idemeum agent is installed, it automatically makes the necessary changes to the registry so that both products can work together. No changes required on your side.
Behind the scenes we modify following registry key HKEY_LOCAL_MACHINE\SOFTWARE\Duo Security\DuoCredProv, and create the new Multi-String Value key, name the key ProvidersWhitelist and assign the following value {417C7858-EE65-42AD-9F11-5BA27FB1FF64}.
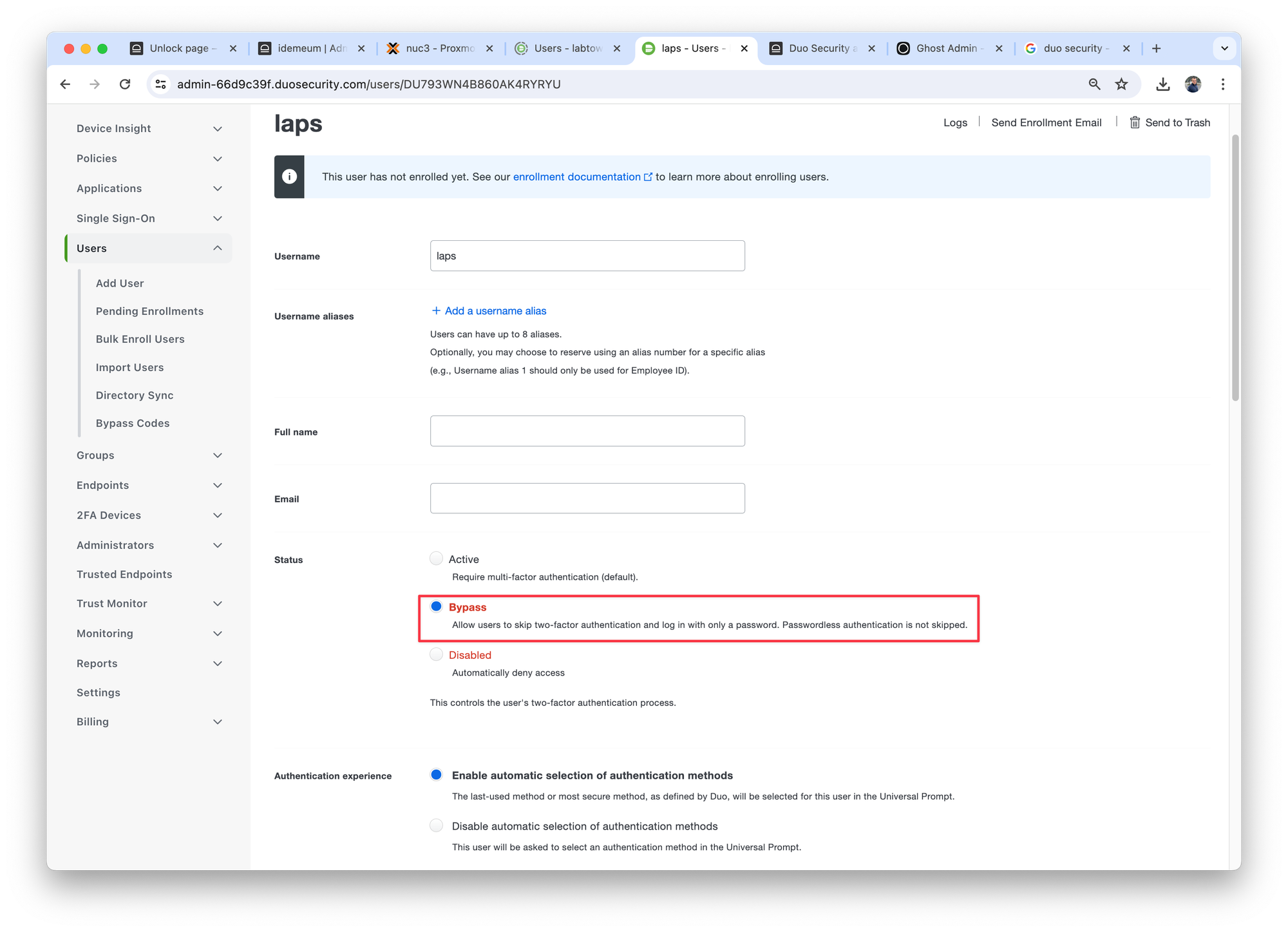
LAPS accounts
Idemeum creates LAPS local admin and domain admin accounts on Windows workstations. In order to use LAPS accounts you need to make sure they are not using DUO 2FA. To make sure 2FA is bypassed for LAPS accounts:
- Navigate to Duo dashboard
- Create the user with the same account that is configured in idemeum for LAPS
- Enable bypass for this account