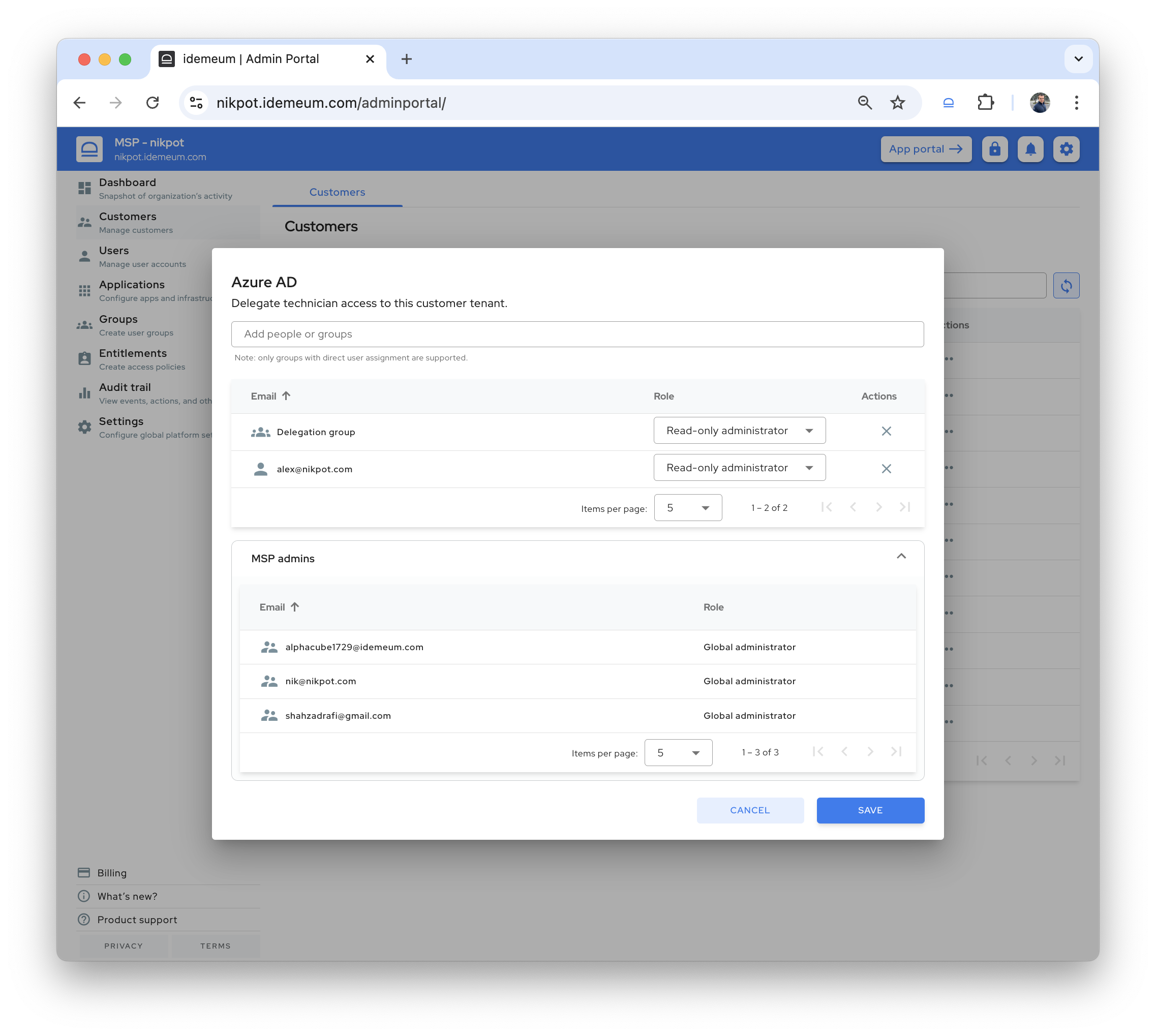
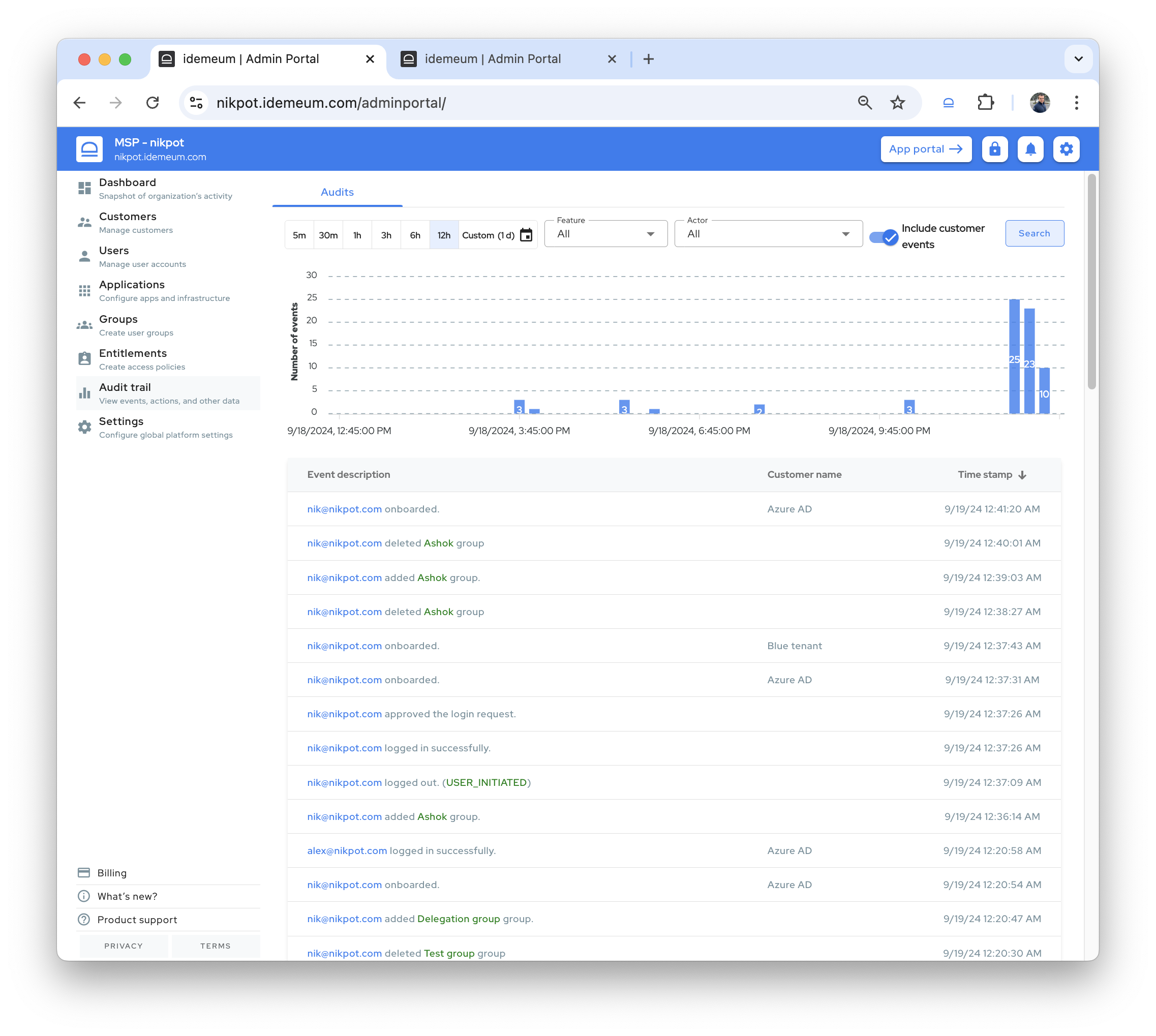
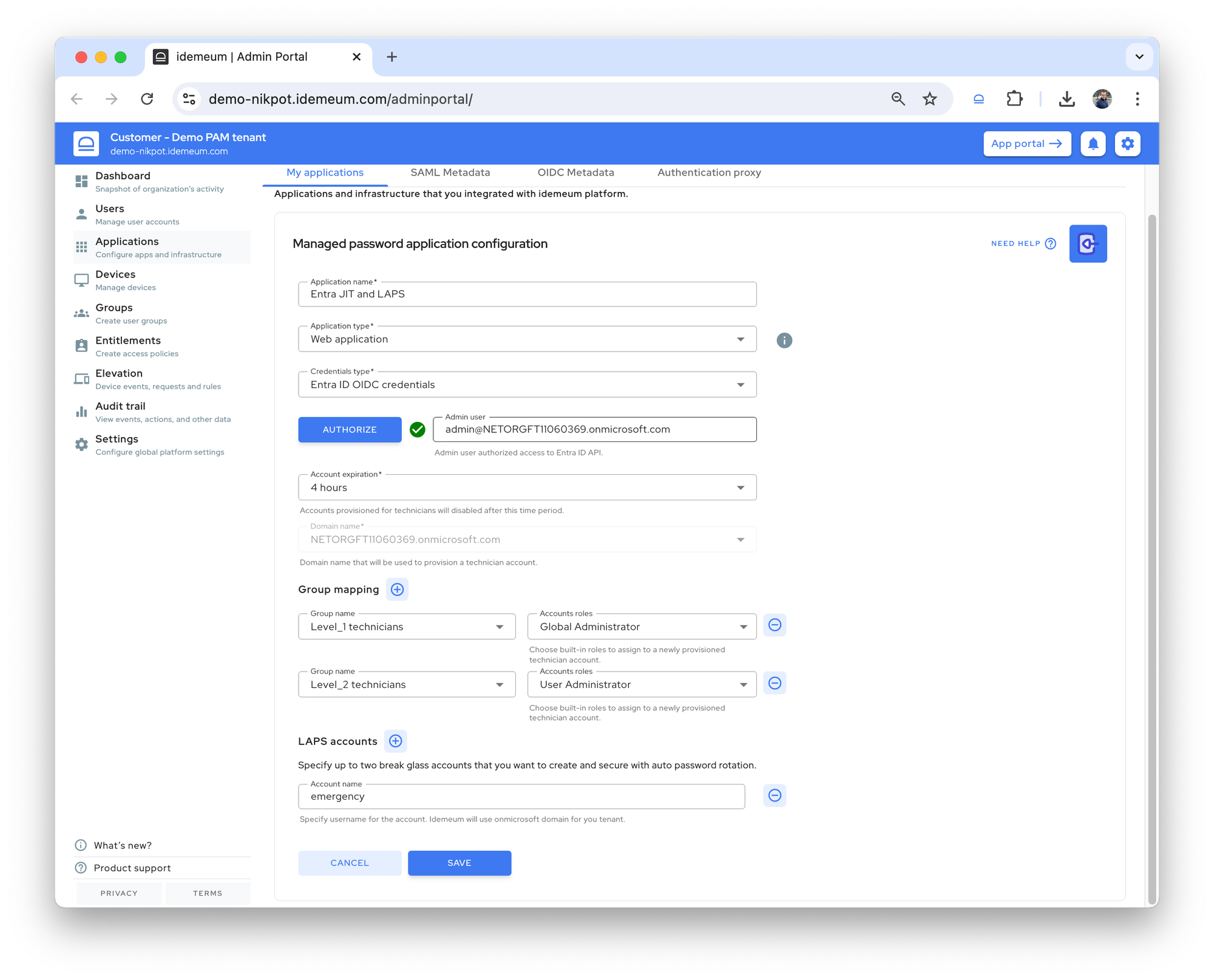
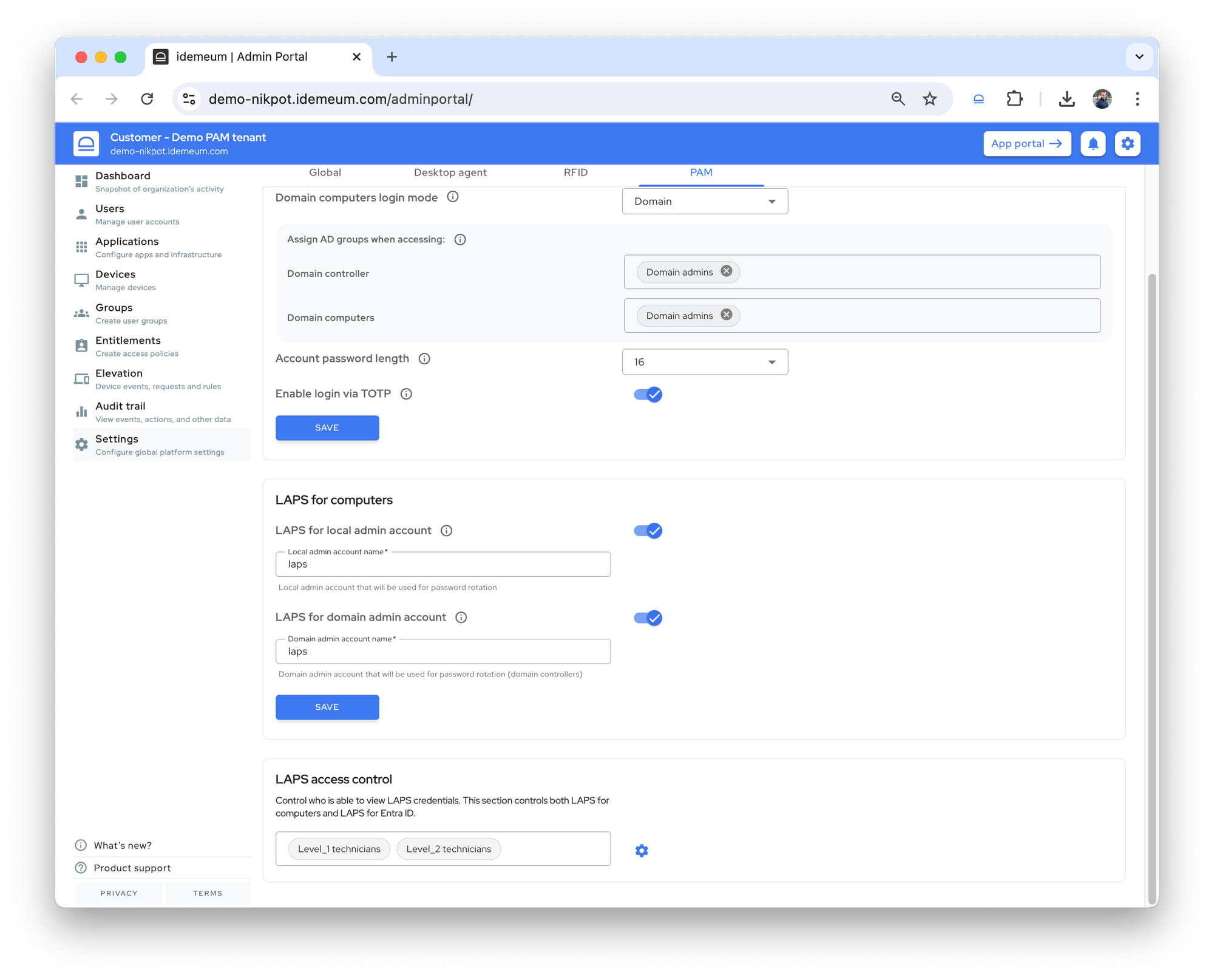
We have been busy working hard on our new product, and have not shared updates for some time. Wanted to update you on what is coming and what improvements we have made recently.
Windows allowlisting - coming shortly!
We have been working hard on our Windows kernel driver to control what applications can run on Windows workstations, and block execution of untrusted files and ransomware. Our goal - make allowlisting simple, yet effective.
We have packed a ton of features:
- Rule engine to control what apps can run
- Implicit trust for Windows SO binaries and critical files to not interrupt updates and critical OS functions
- Automatic block of Microsoft binaries that can we weaponized (i.e. integration with LOLBAS project)
- Controlling child process execution
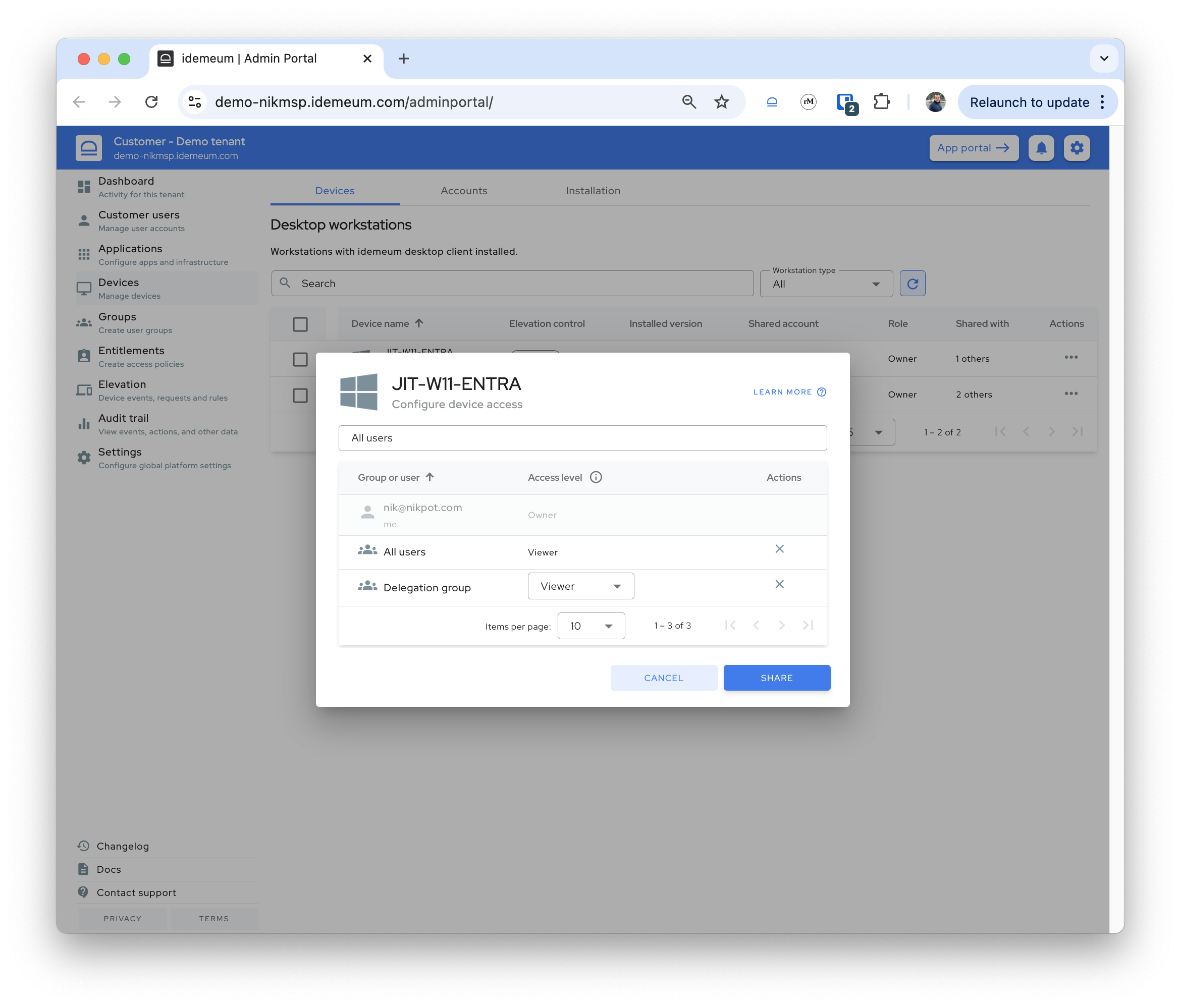
- Fully integrated elevation control
- Pre-configured catalog rules to allowlist applications with a click of a button
- Microsoft App Store control
- and more...
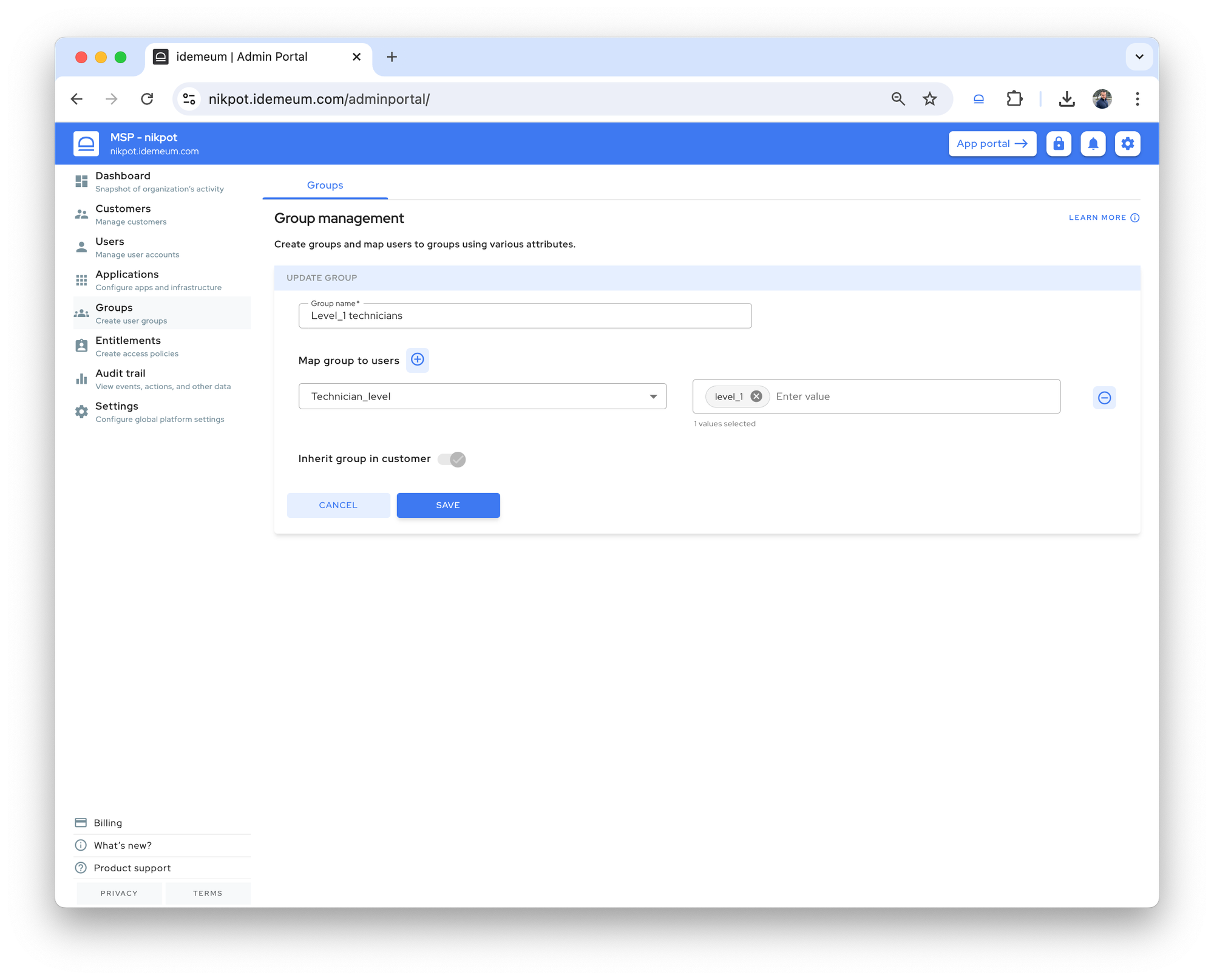
Real-time settings
We have enhanced our tenant settings to be real time. Now if you change something for the customer tenant (i.e. change JIT login mode, update elevation message, etc.), we push notification to all affected devices and the changes are applied immediately. If for whatever reason the notification is missed, the desktop agent will pull the updated settings during the next 6 hour sync interval as a fallback.
Enhancements and fixes
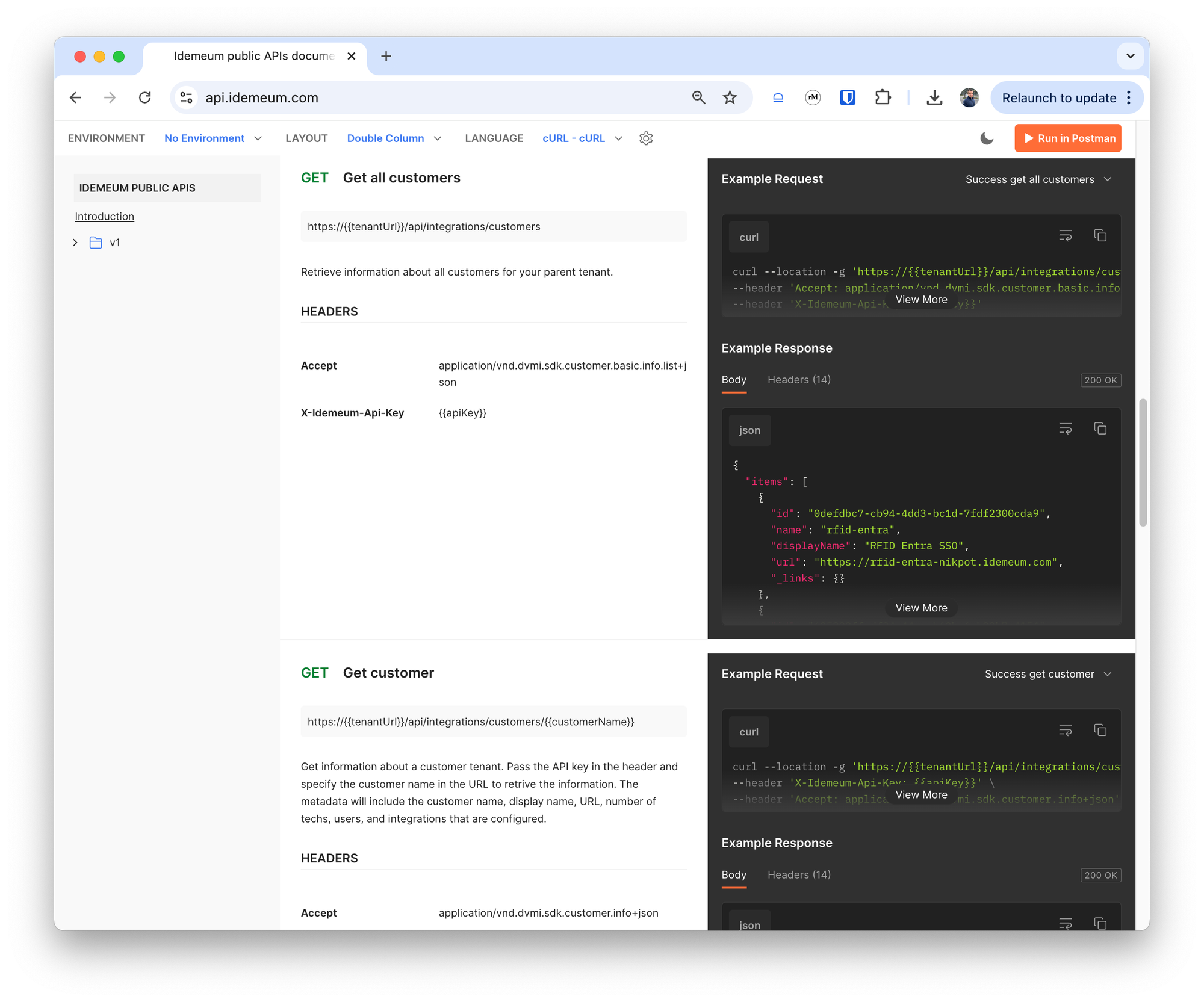
- Updated our APIs to return parametrized installation command in addition to returning the whole command as a string.
- Fixed the issue of bulk elevation mode change in the UI.
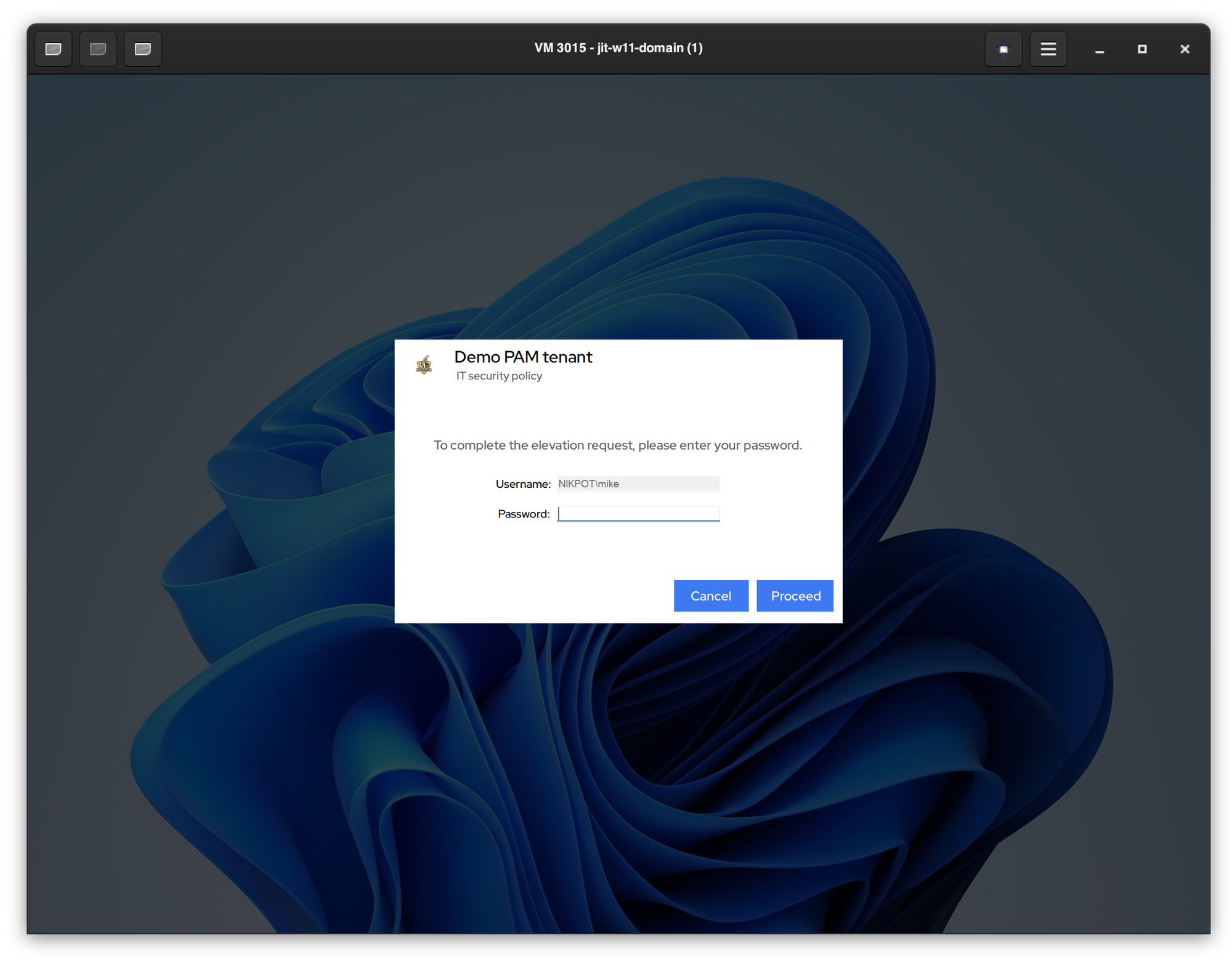
- Enhanced Windows JIT login by avoiding automatic user switch on lock. No longer messing up with VPNs or user desktop settings.
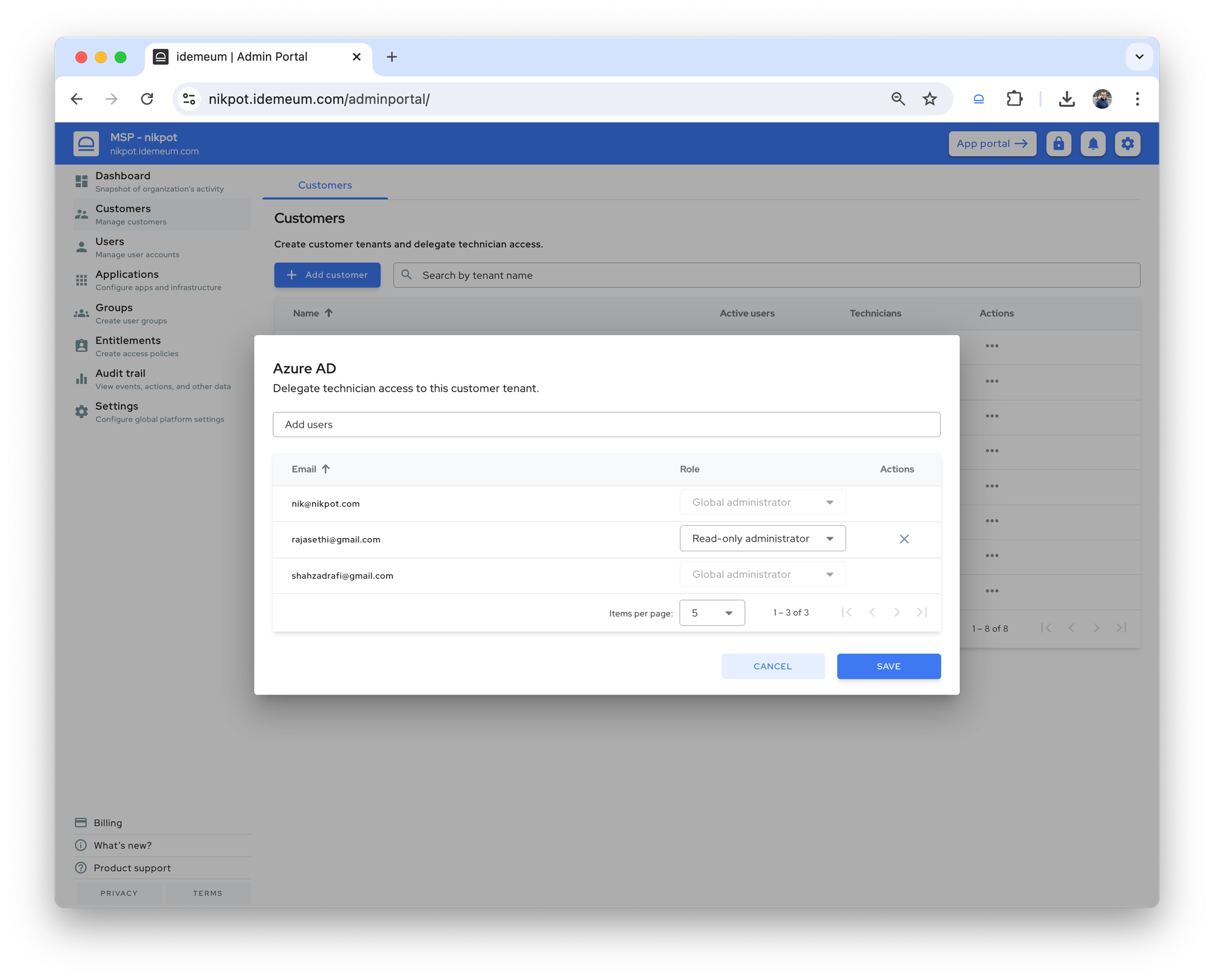
- Enhanced how we tag devices in the admin portal. Now when agent is installed with properly show servers, domain controllers, or workstations. We also properly reflect domain, local, or Entra-joined status.
- Made an enhancement to ensure the JIT account always belongs to
Administratorgroup. Even if membership is removed, idemeum will reassign it during next login. - Enhanced RFID tap-out flow to ensure card data is cleared, i.e., card hold data time elapses before disconnecting or signing out of the session.
- Enhanced JIT flow to avoid WMI query which at times takes longer to complete.
- Enhanced UAC capture flow to handle unverified events properly.
- Fixed offline transition when DNS does not resolve the idemeum domain.
- Improved log clean up.
- Google has discontinued support for the authorization flow in Internet Explorer, so changed to a Chromium-based browser instead of the default Internet Explorer for RFID SSO.
- Managing version.txt for RMM tools that cannot read from the registry.
- Optimized token fetch calls by leveraging the cached token in the
Update Settingsflow. - Ensuring metadata is synced to the cloud once a day, if not updated
- Domain JIT account login: do not fail if one or more DC is not reachable during account verification.