Halo PSA - idemeum integrations
Integrate idemeum with HaloPSA to create tickets for elevation requests, requests JIT accounts, and more.
— Nik Pot

Integration options
There are several integrations that we support with HaloPSA today:
- Create tickets for elevation requests
- Request JIT accounts from tickets
- Disable JIT accounts from HaloPSA
Create tickets for elevation requests
Overview
- Create HaloPSA ticket when elevation is requested
- Close HaloPSA ticket when the request is approved / denied
- Approve or deny elevation requests right from the HaloPSA by clicking on generated link
- Automatically map customer names in idemeum to customer names in HaloPSA
- Manually map customer names in idemeum to customer names in HaloPSA
Configure HaloPSA agent
In this step we will create an API-only agent to use with HaloPSA application.
- Navigate to
Configuration→Teams and agents→Agentsand add a new agent by clickingNewbutton
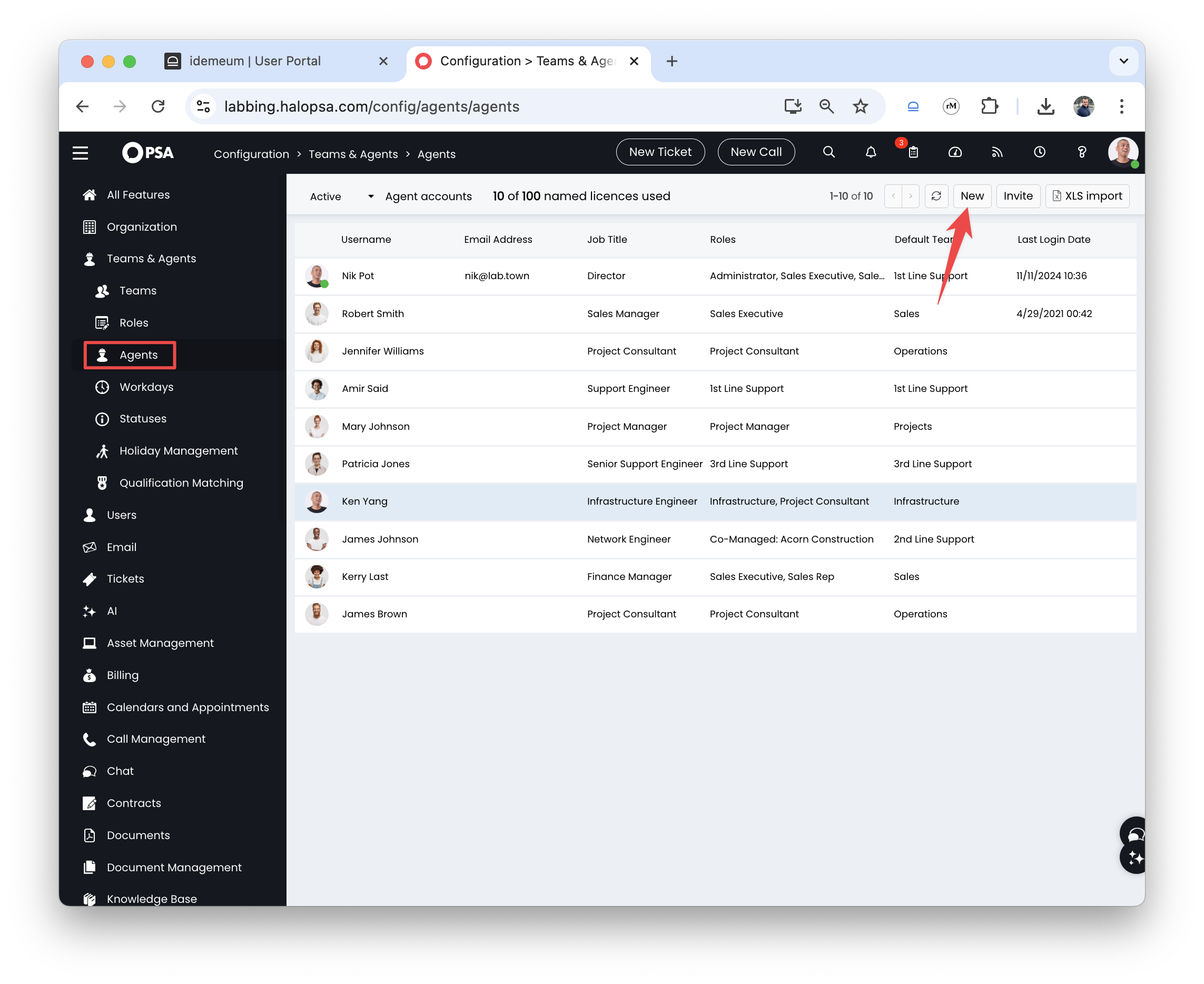
- Provide the agent username
- Make sure you check the box for
Is an API-only Agent
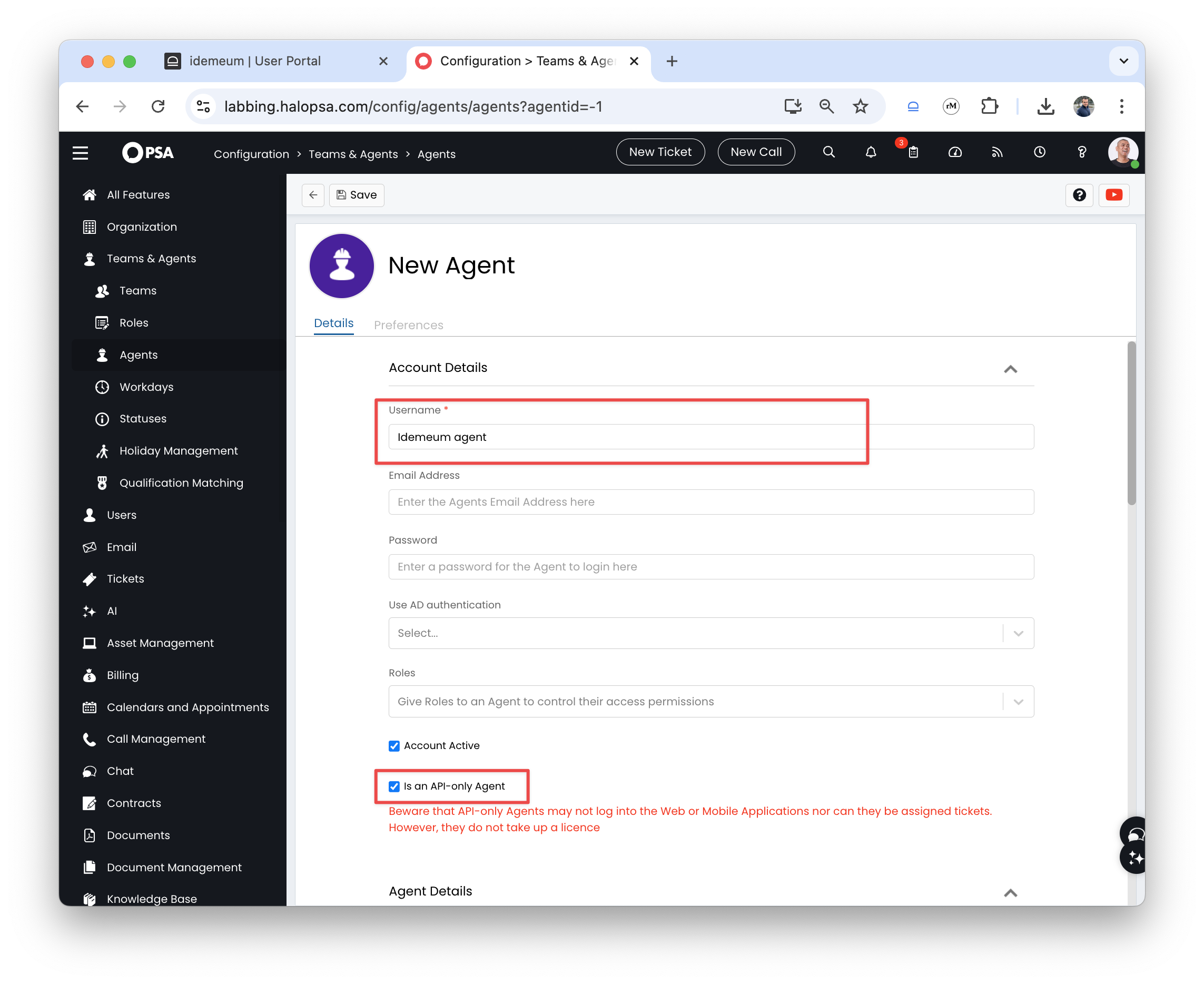
- Assign agent to the
Default teamof your choice and add the working hours Savethe configuration
Now we will need to configure the proper permissions:
- Click
Editto configure the agent - Navigate to
Departments and teamstab - If you are using teams, make sure the team you have chosen has the following permissions:
- Can be assigned to
- Can see unassigned tickets for this Team
- Can see Tickets assigned to other Agents in this Team
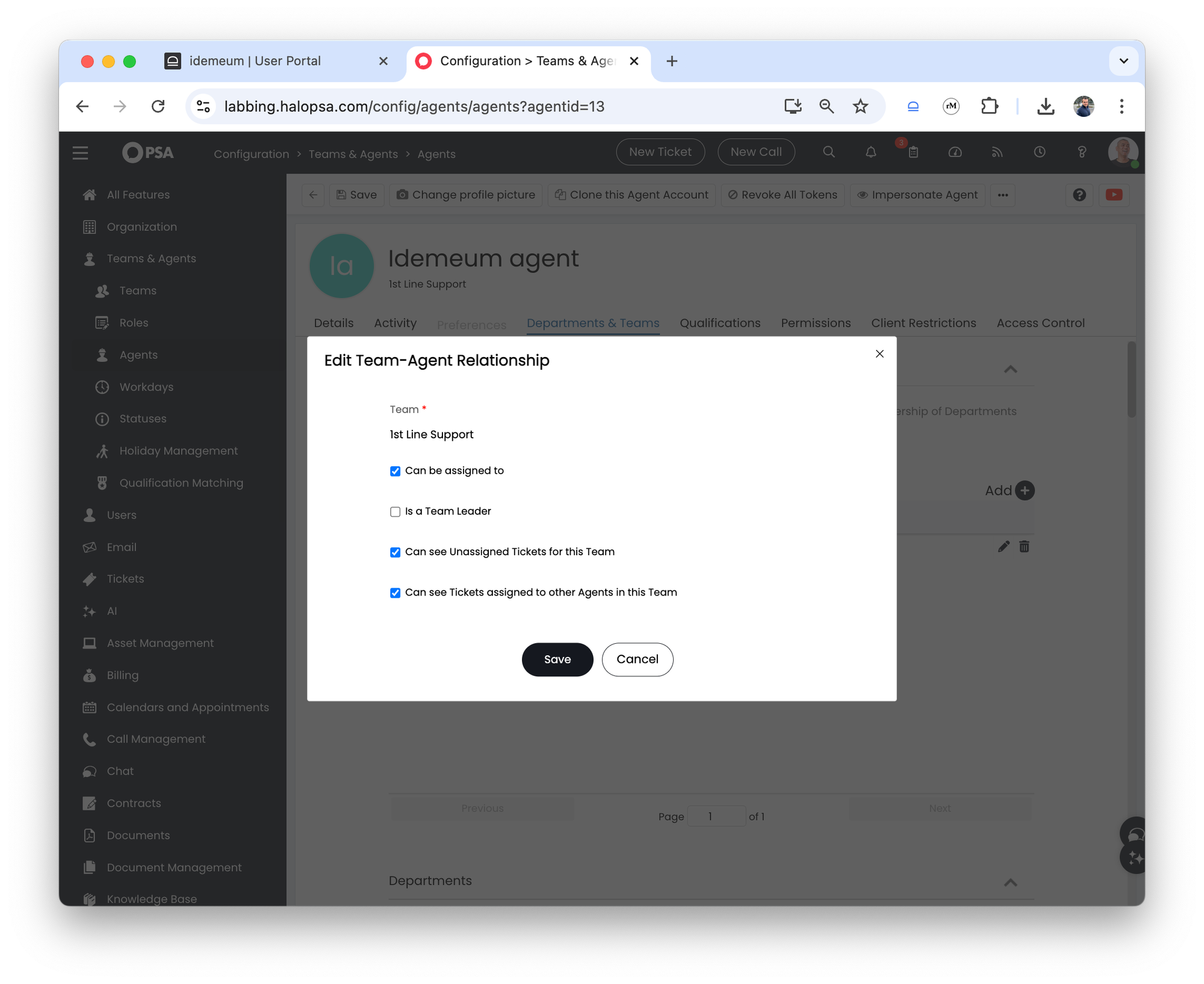
- If you are using departments, make sure the permission
Modify allis added - Now click on
Permissionstab and do the following:- For
Feature accesschoose the following:- Tickets Access Level to Read and Modify
- Clients Access Level to Read Only
- Users Access Level to Read Only
- Assets Access Level to Read Only
- For
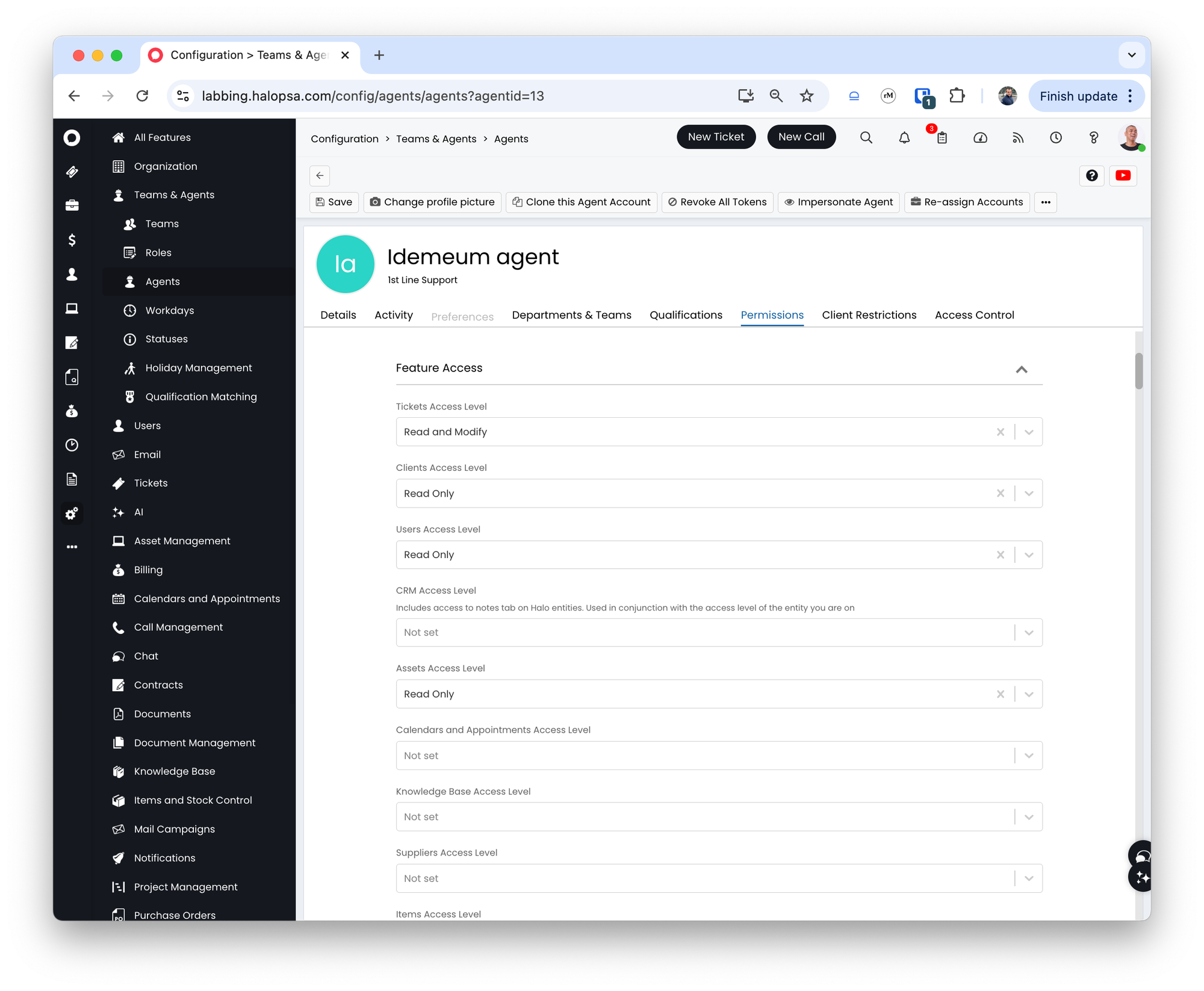
- For
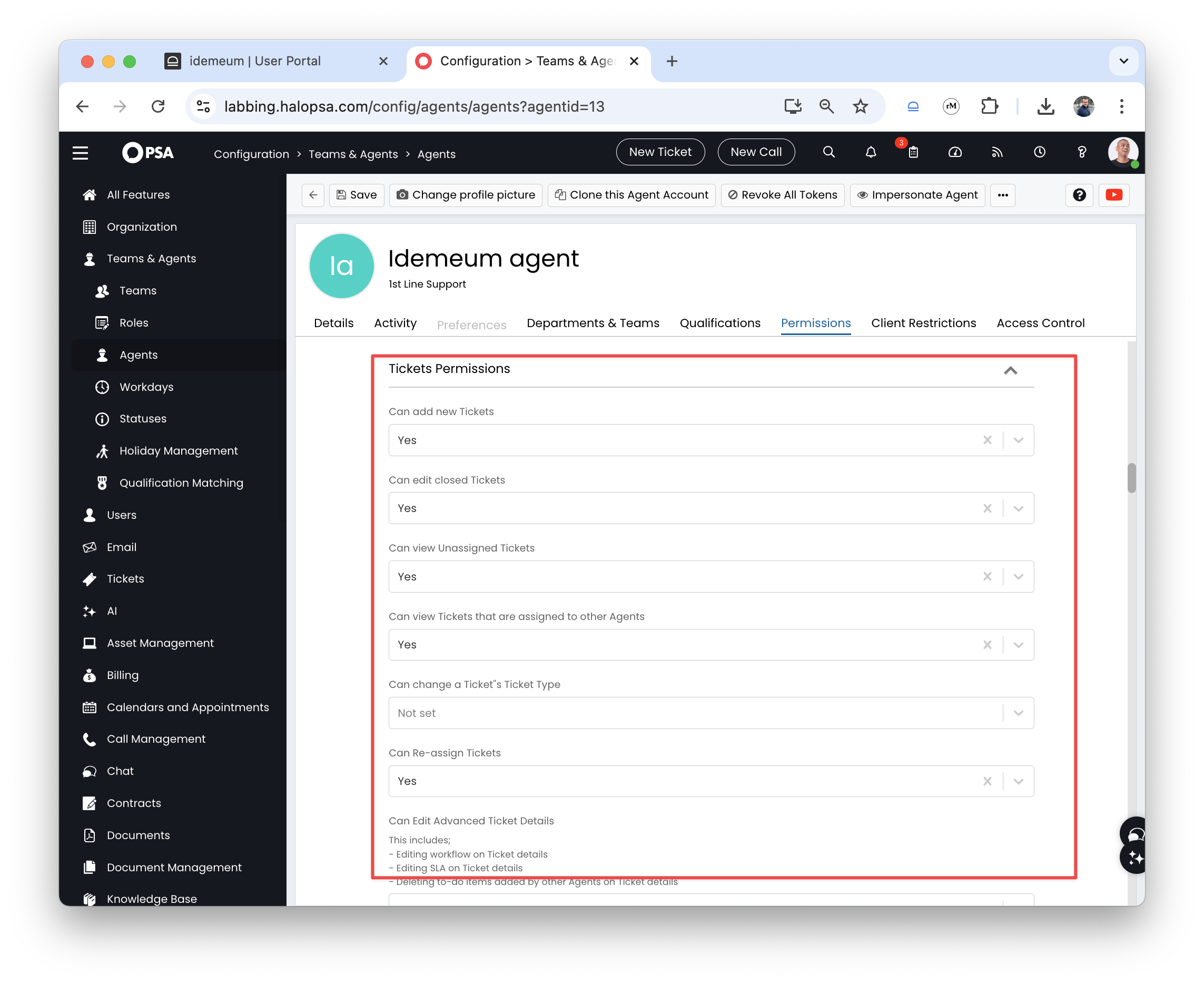
Ticket permissionchoose the following:- Can add new Tickets
- Can edit closed Tickets
- Can view Unassigned Tickets
- Can view Tickets that are assigned to other Agents
- Can Re-assign Tickets
- Can Edit Tickets Which Are Not Assigned To Them
- Can always update Ticket Statuses and re-assign Tickets outside of actions
- For
Asset type restrictionschoose the following:- Allow use of all Asset Types
- Save the agent configuration
Configure HaloPSA application
The way HaloPSA allows other systems to make calls into their system is by creating an application.
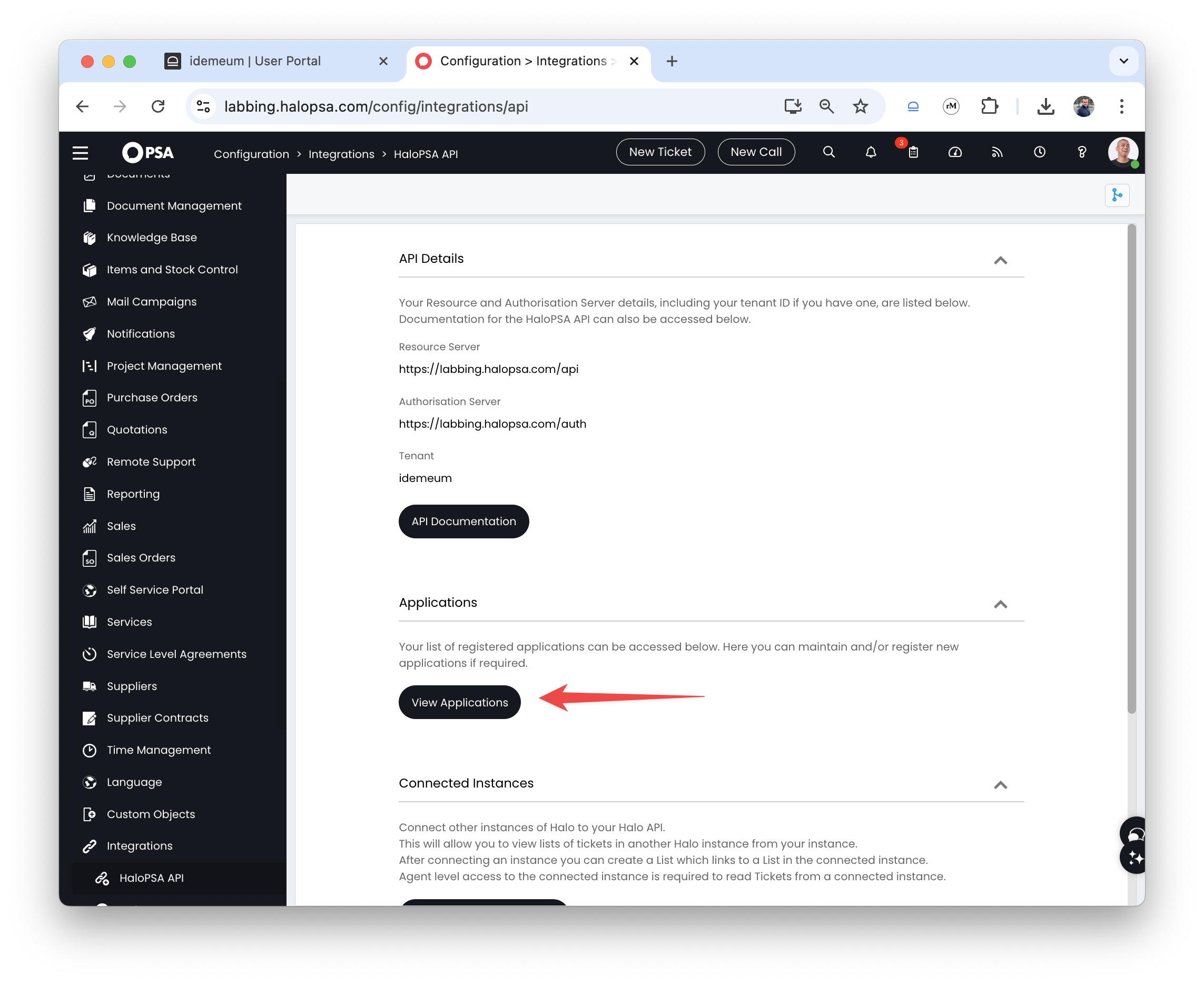
- Navigate to HaloPSA admin portal
- Access
Configurations→Integrations→HaloPSA APIand clickView applications
- Now click
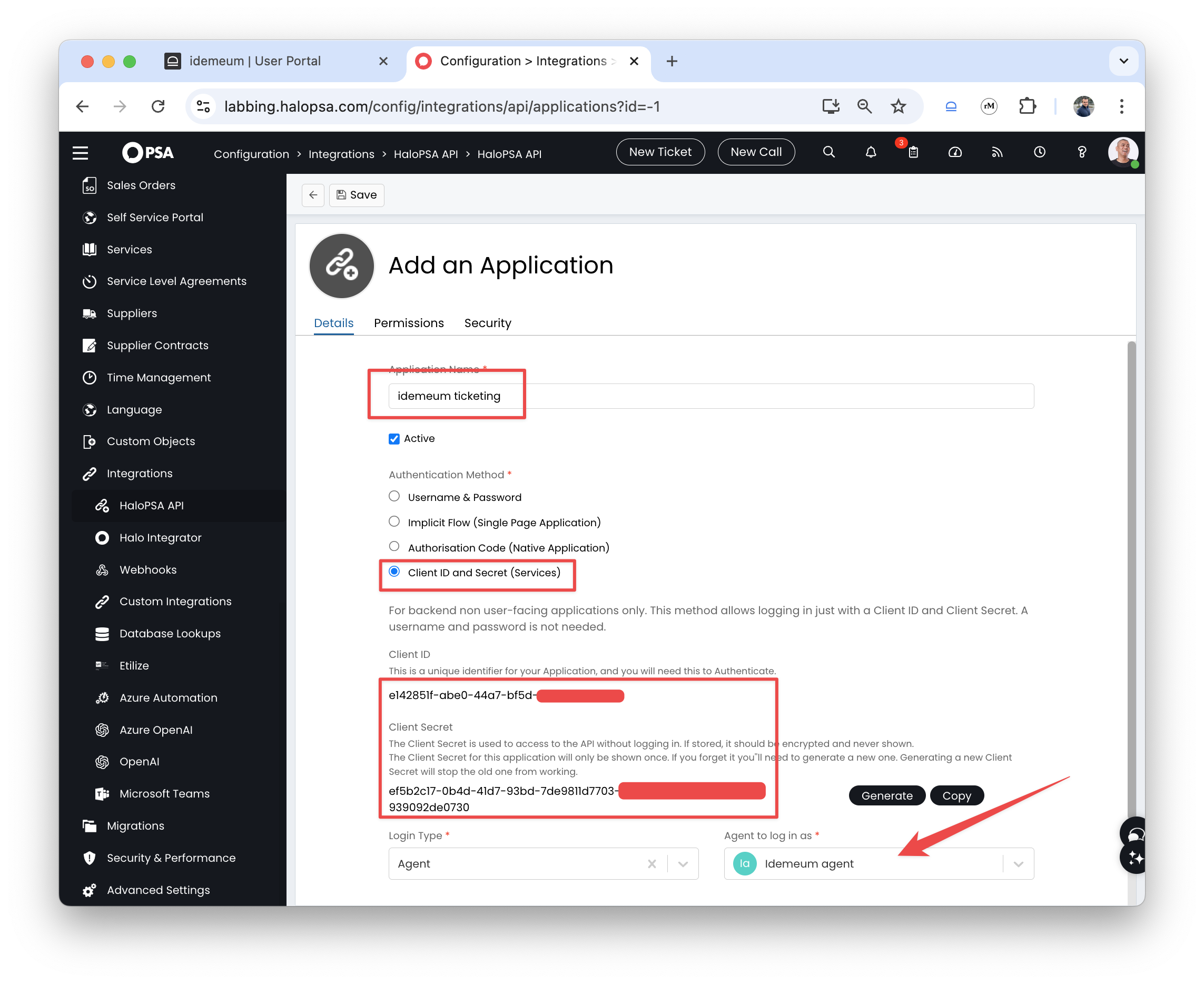
Newto create a new application - Provide application name
- Choose
Client ID and Secretfor Authentication method. Save theClient IDandClient Secretas you will need this information for idemeum configuration. - For the agent drop down choose the agent that we created in the previous step
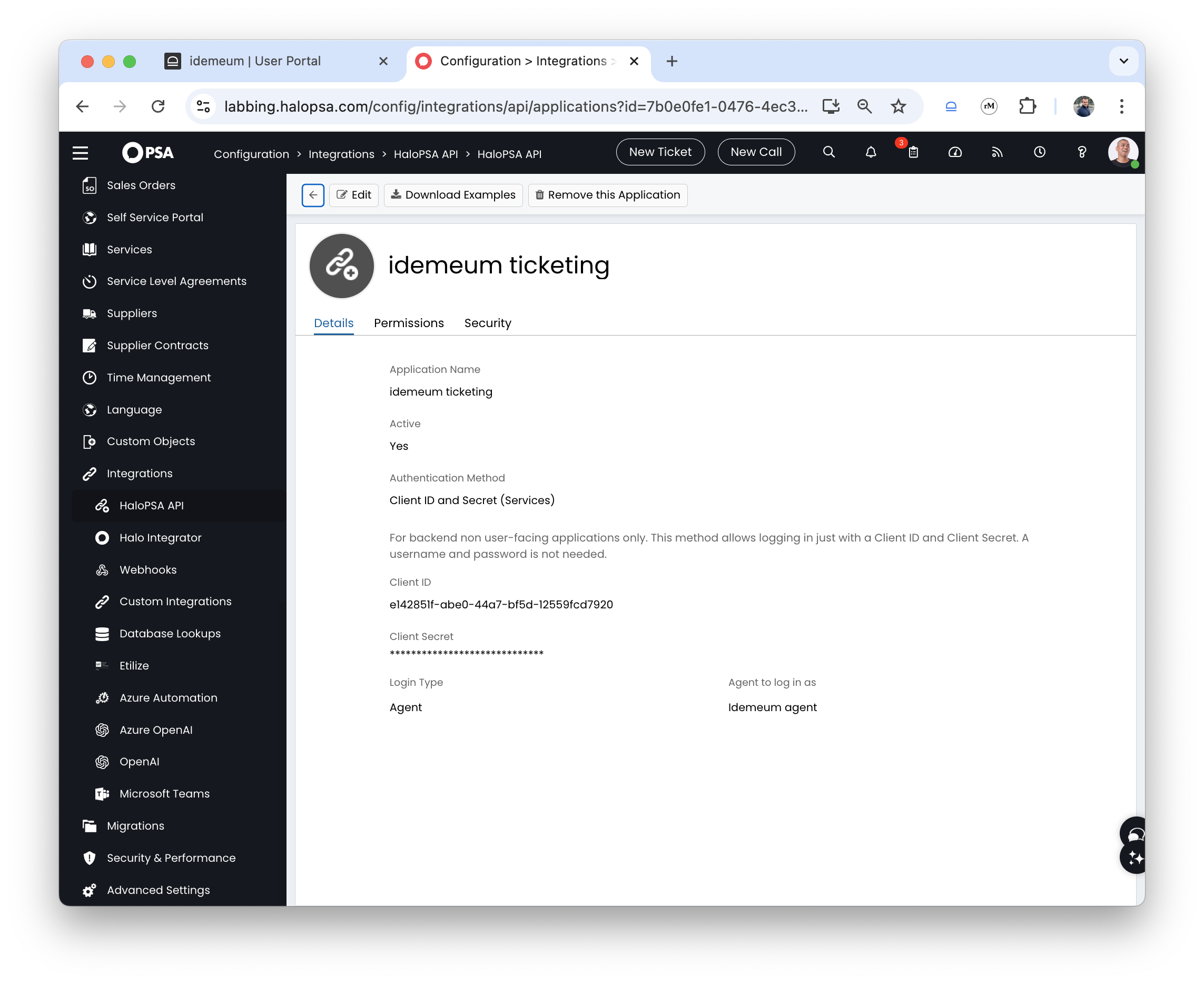
- Click on the
Permissionstab and add the following permissions:- read:tickets
- edit:tickets
- read:customers
- read:assets
Savethe configuration
Configure idemeum connector
- Access your MSP tenant admin portal
- Navigate to
Settings→Integrations - Click
Add integrationand then chooseOutbound integration
- Choose
Halo PSAfrom the connector dropdown - Now enter the URL of your HaloPSA instance and provide the
Client IDandClient secretthat we created in the previous step
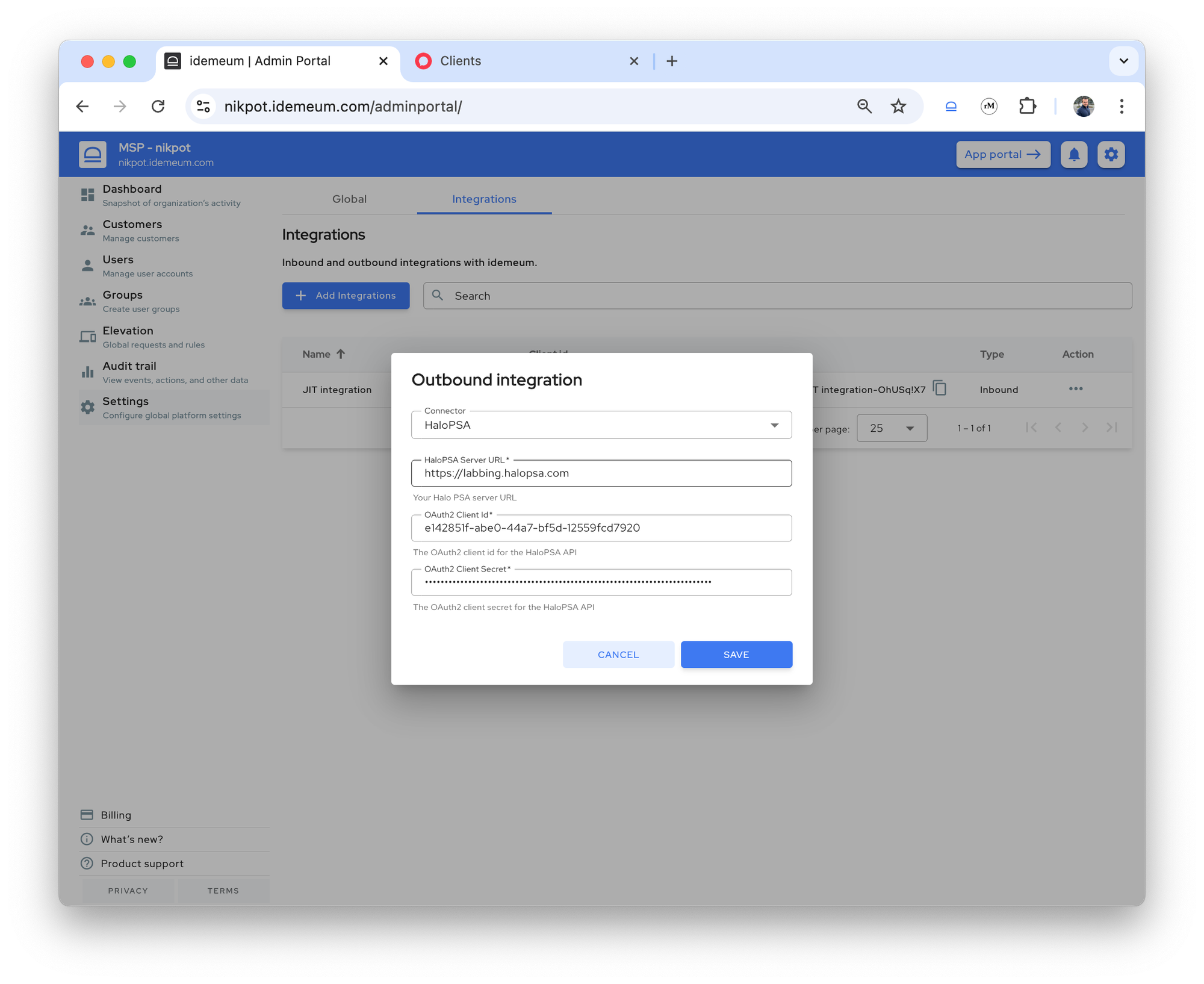
Savethe configuration
Customers mapping
Once the integration with HaloPSA is added, you will see the new PSA column in the Customers section.
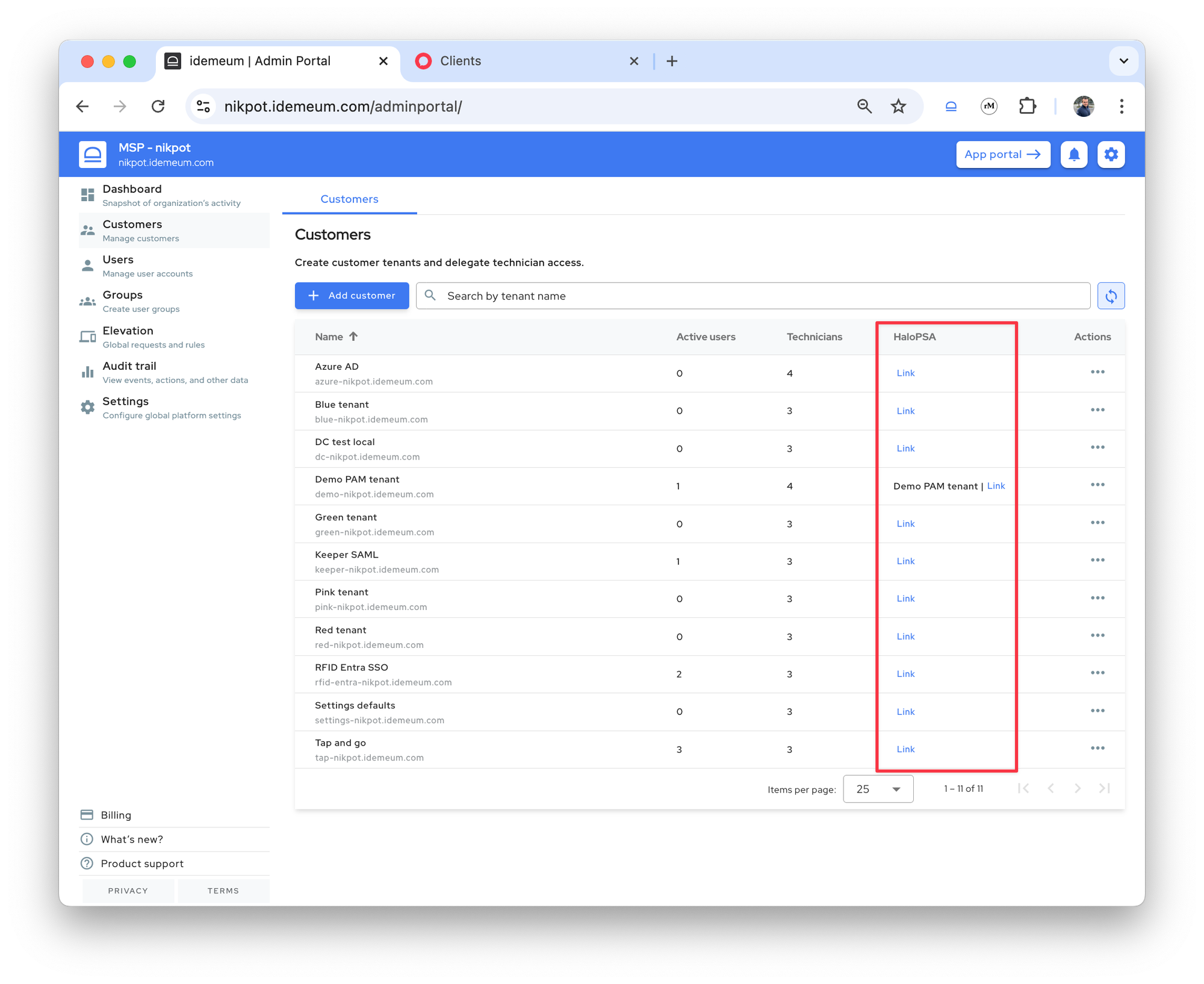
Automatic mapping
As a first step idemeum will try to automatically map the customers in idemeum to customers in HaloPSA. Here is how we will try to do that:
- Use the
Display Nameof the customer in idemeum to search for a customer in HaloPSA - If no match was found using the
Display Name, then we would use theNameof the customer in idemeum to search for a customer in HaloPSA - If no match was found using the
Name, then the admin will have to manually link the customers
For example, in the image below, one of my customers was automatically mapped, however, others still show the Link button to manually map the customer in HaloPSA.

Manual mapping
The admin can manually link a customer from idemeum with one in HaloPSA by providing the name of the customer from HaloPSA.
- Navigate to idemeum admin portal and access
Customerssection - Search for the customer name
- Click on the
Linkbutton
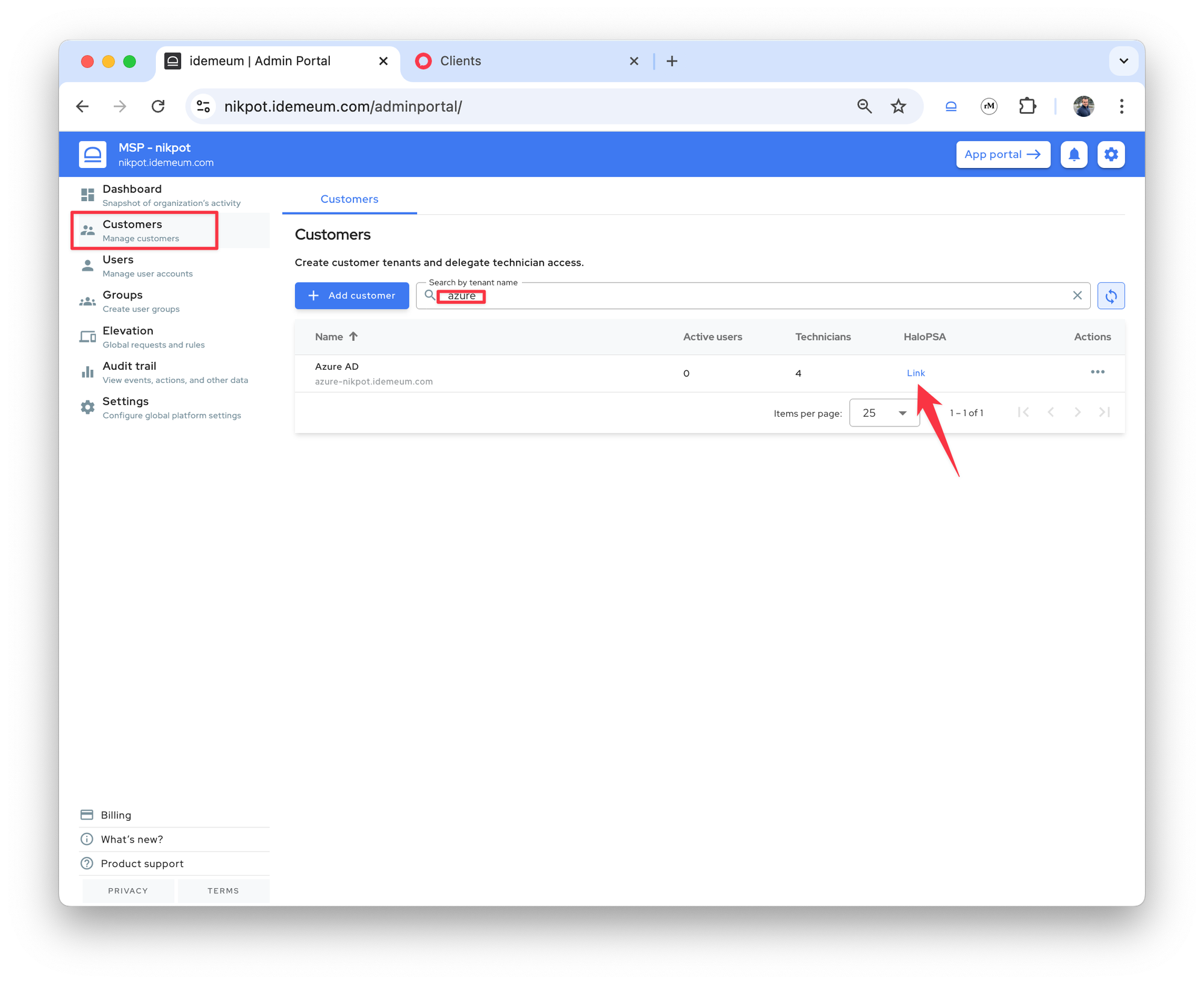
- Enter the HaloPSA customer name to map this idemeum customer to
- Once found we will display the customer name from HaloPSA in the PSA column.
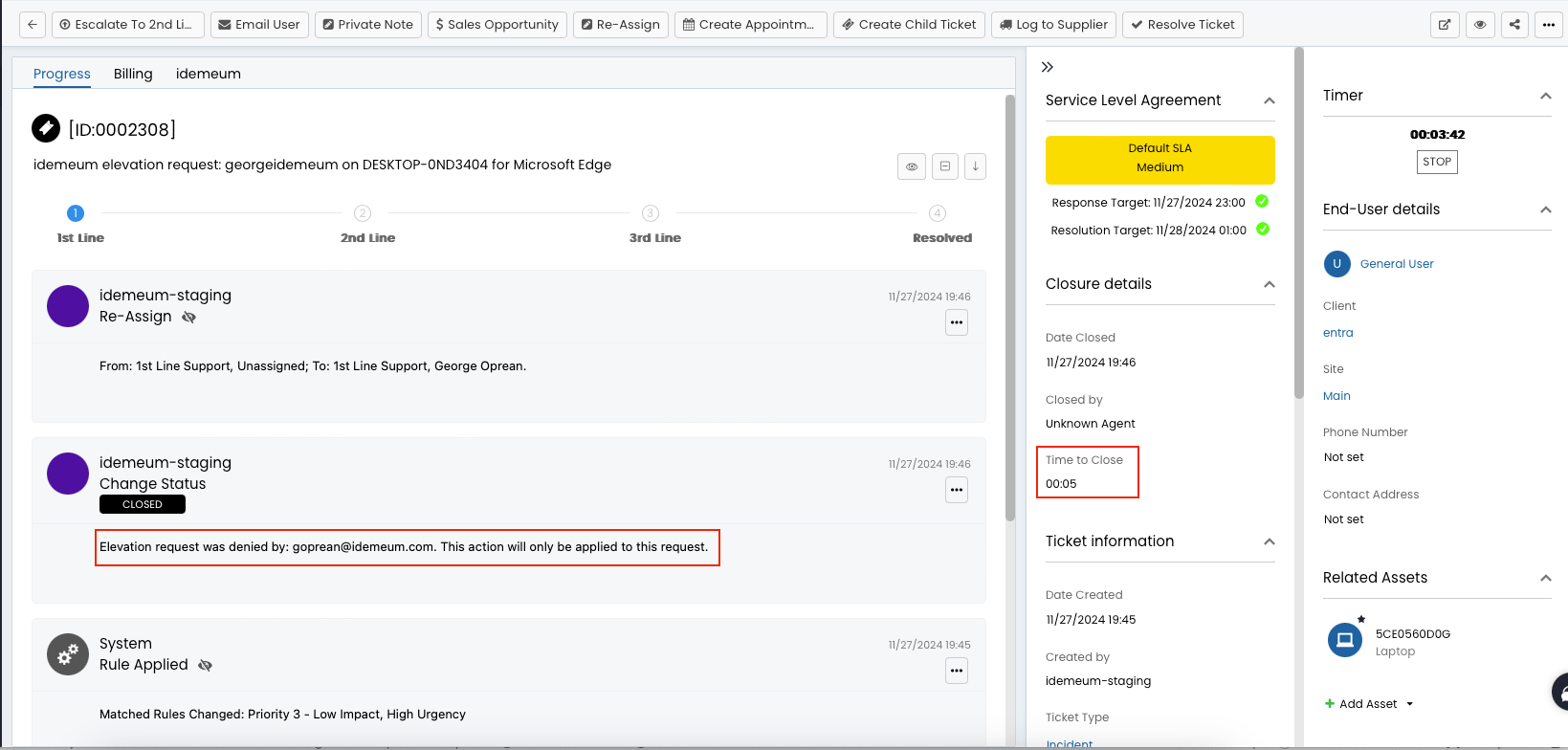
Ticket creation
Here is how idemeum will create the tickets in HaloPSA:
- Idemeum will create a ticket of type
Incident - We will use these default values for the ticket:
category- Business Applicationsurgency- Mediumimpact- Single User Affected
- In the ticket there will be information about the user that requested access to which application from which device.
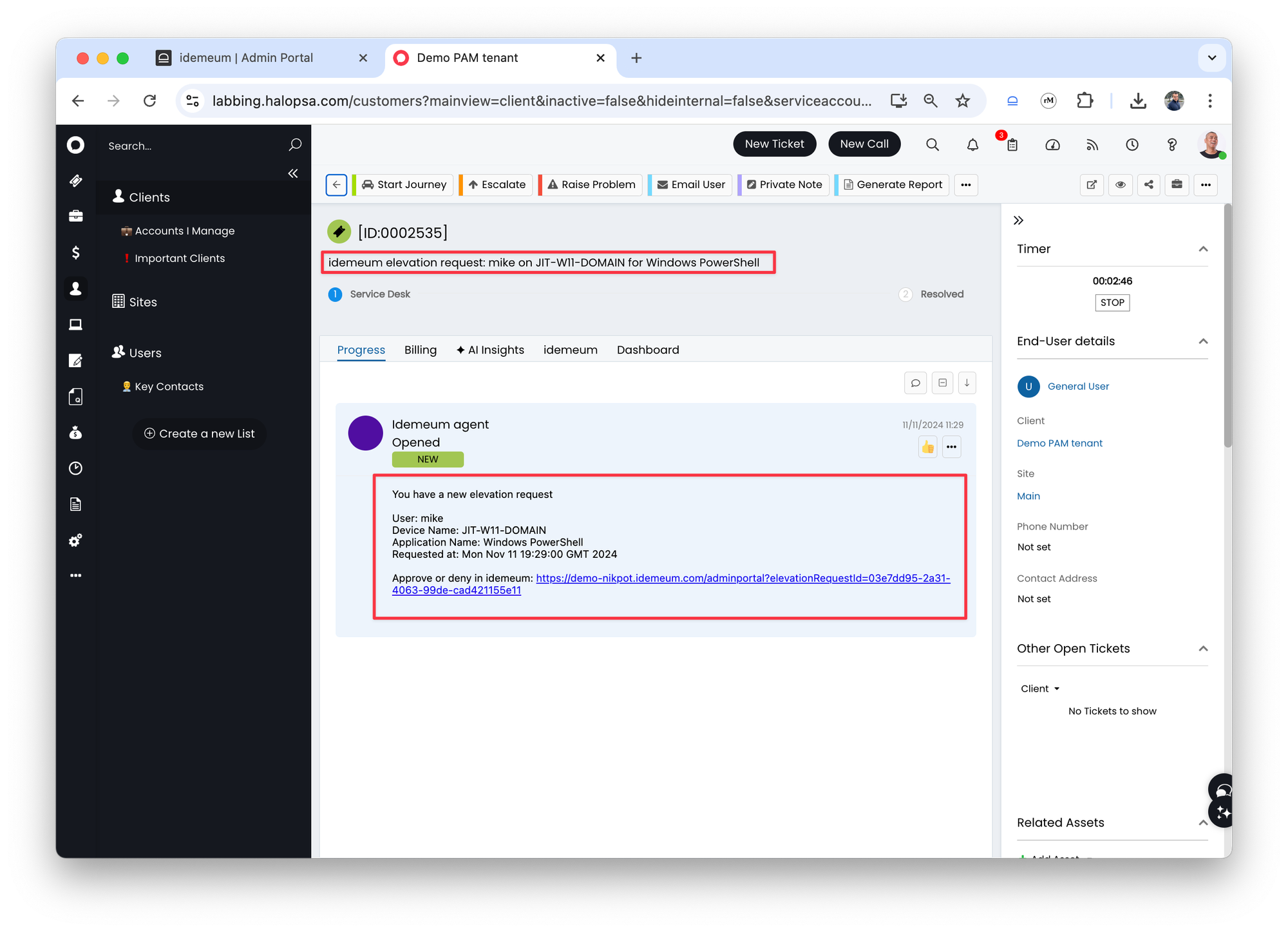
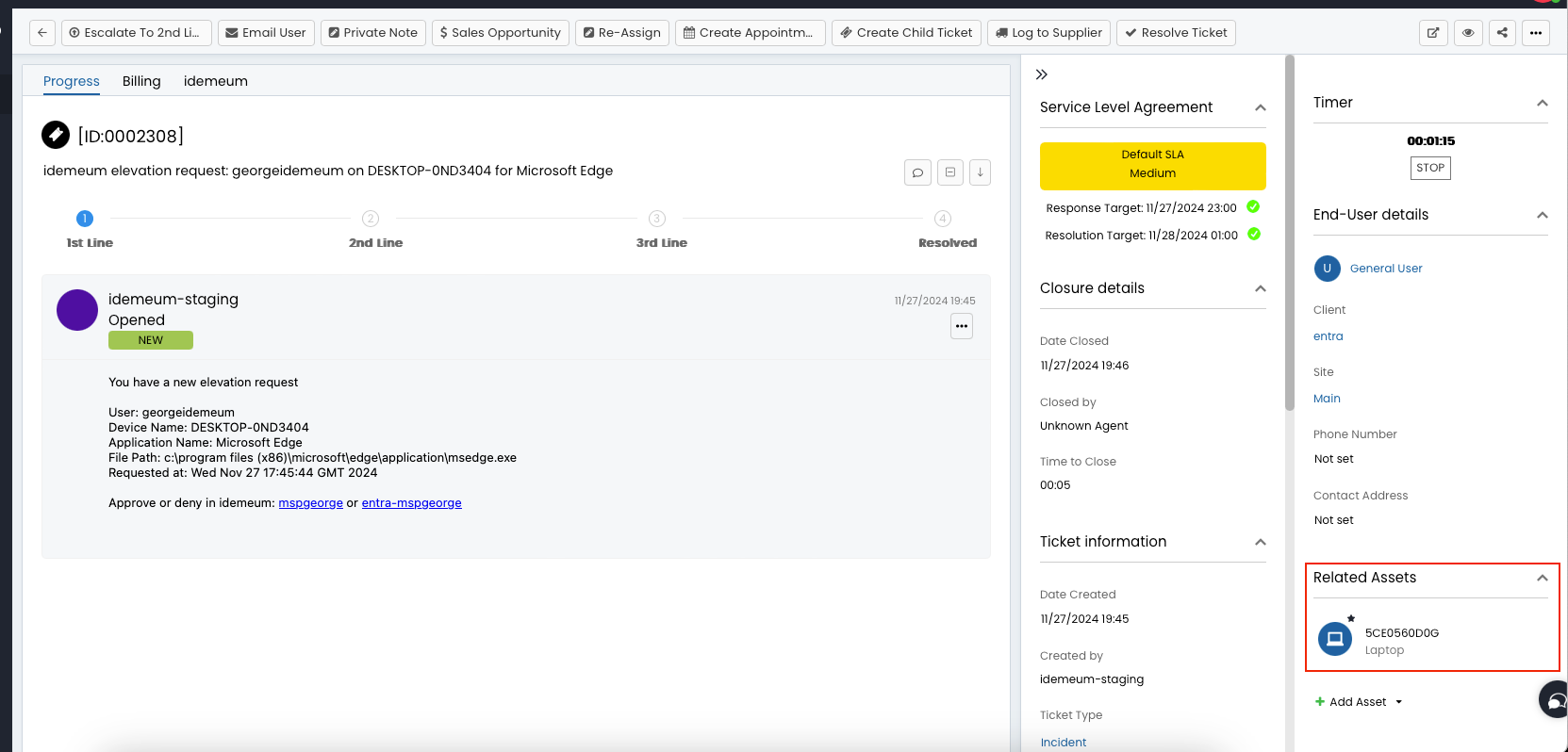
- idemeum knows from which desktop name the elevation was initiated from so will lookup that name in your assets list. If found then we will associate that asset with the HaloPSA ticket.
- There is also a link to navigate to idemeum portal and respond to the request
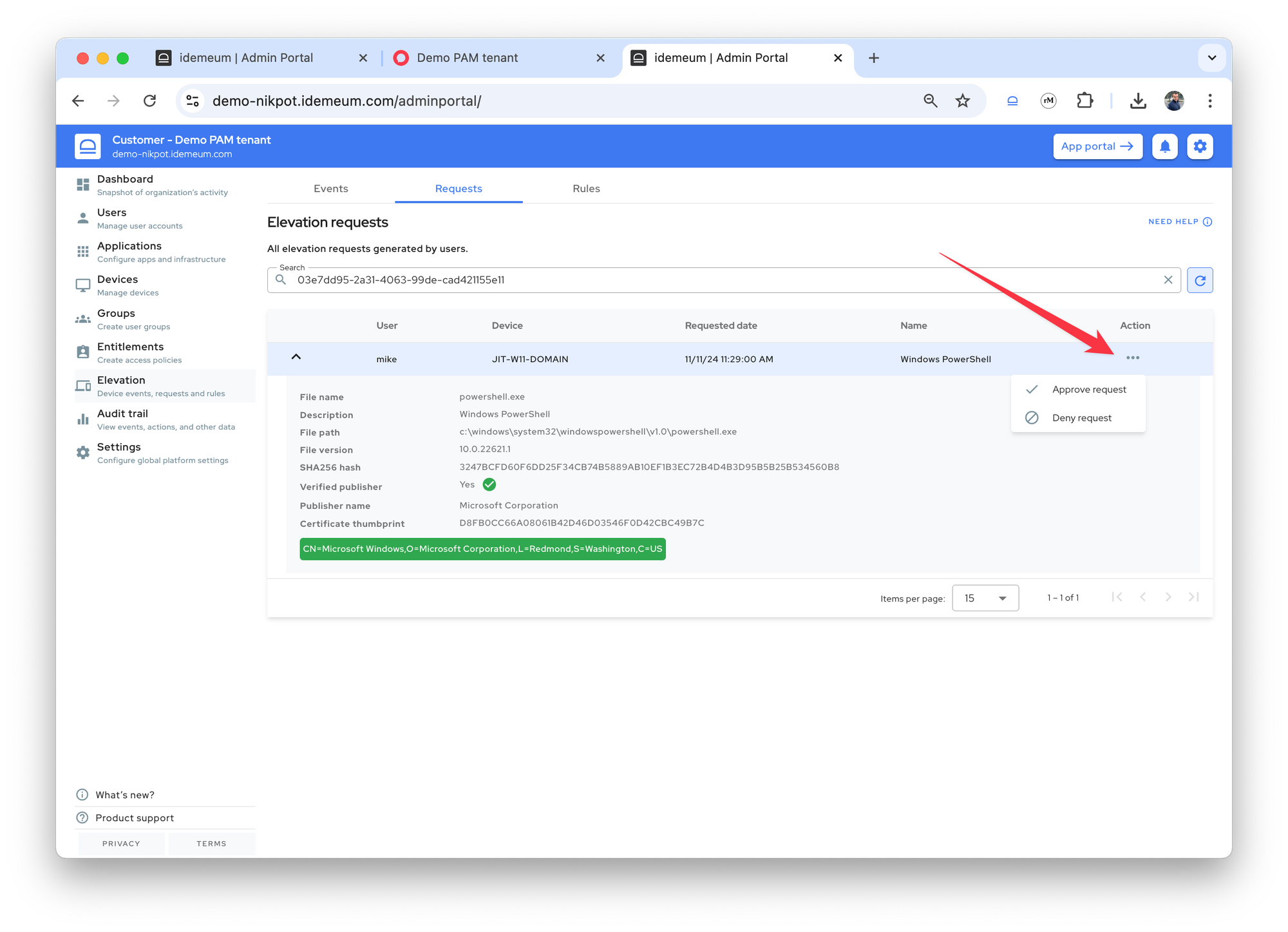
- Once the ticket is approved or denied the HaloPSA ticket will be updated with the status
Closed. If we can find an agent in HaloPSA with the email address of the idemeum user that approved/denied the elevation request then we will assign that agent to the ticket.
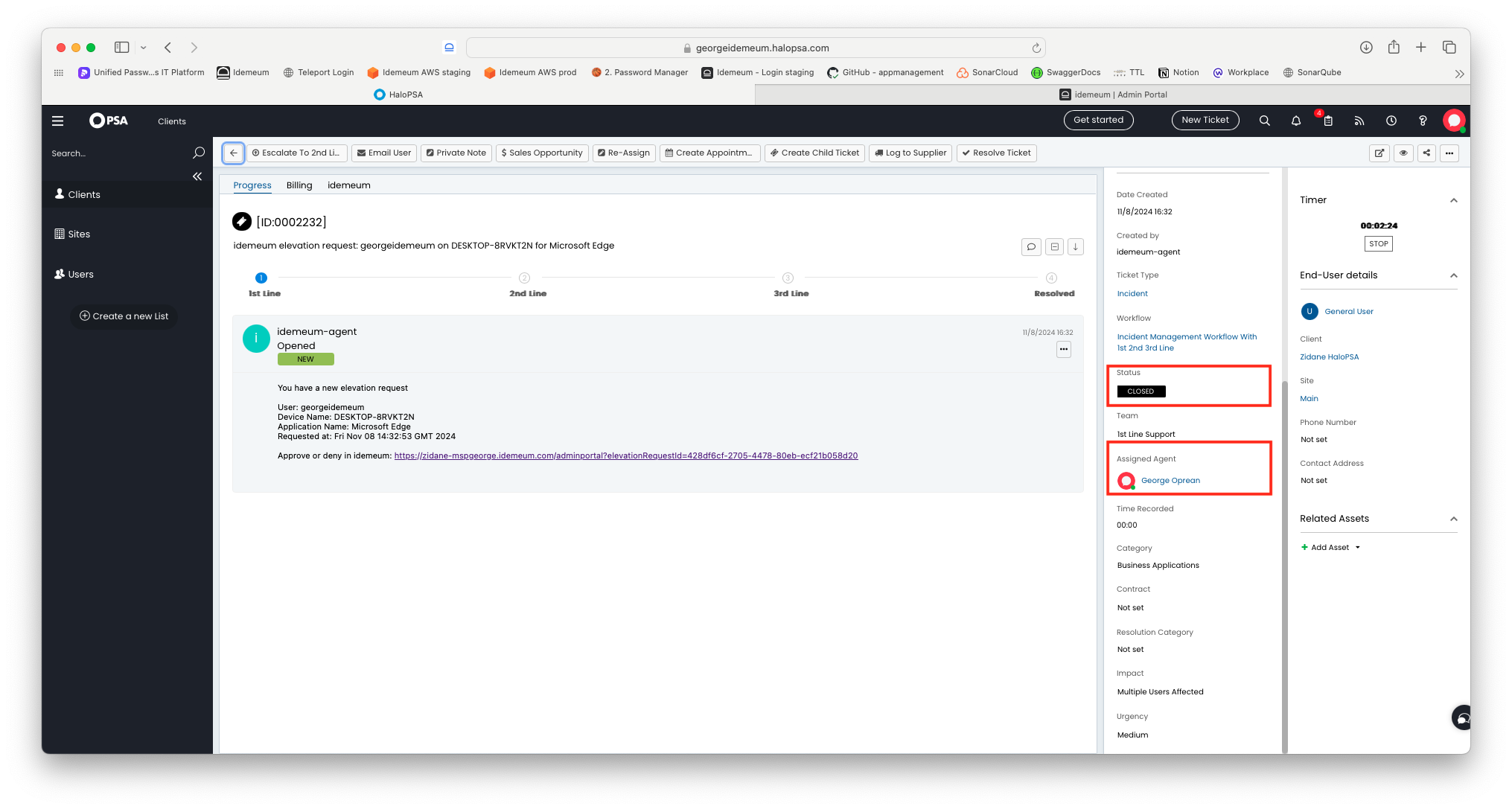
- When a ticket is closed we will add some information on how the ticket was closed in the closure notes: who closed it, was the elevation approved or not, for this user or at a tenant level, etc.
- We will also add a closure time of 5 mins. If you want to use other value rather than 5 mins contact idemeum support.
Request JIT accounts from tickets
Overview
MSP technicians can request Entra ID JIT accounts right from HaloPSA tickets. HaloPSA and idemeum integration leverages embedded iFrame sections.
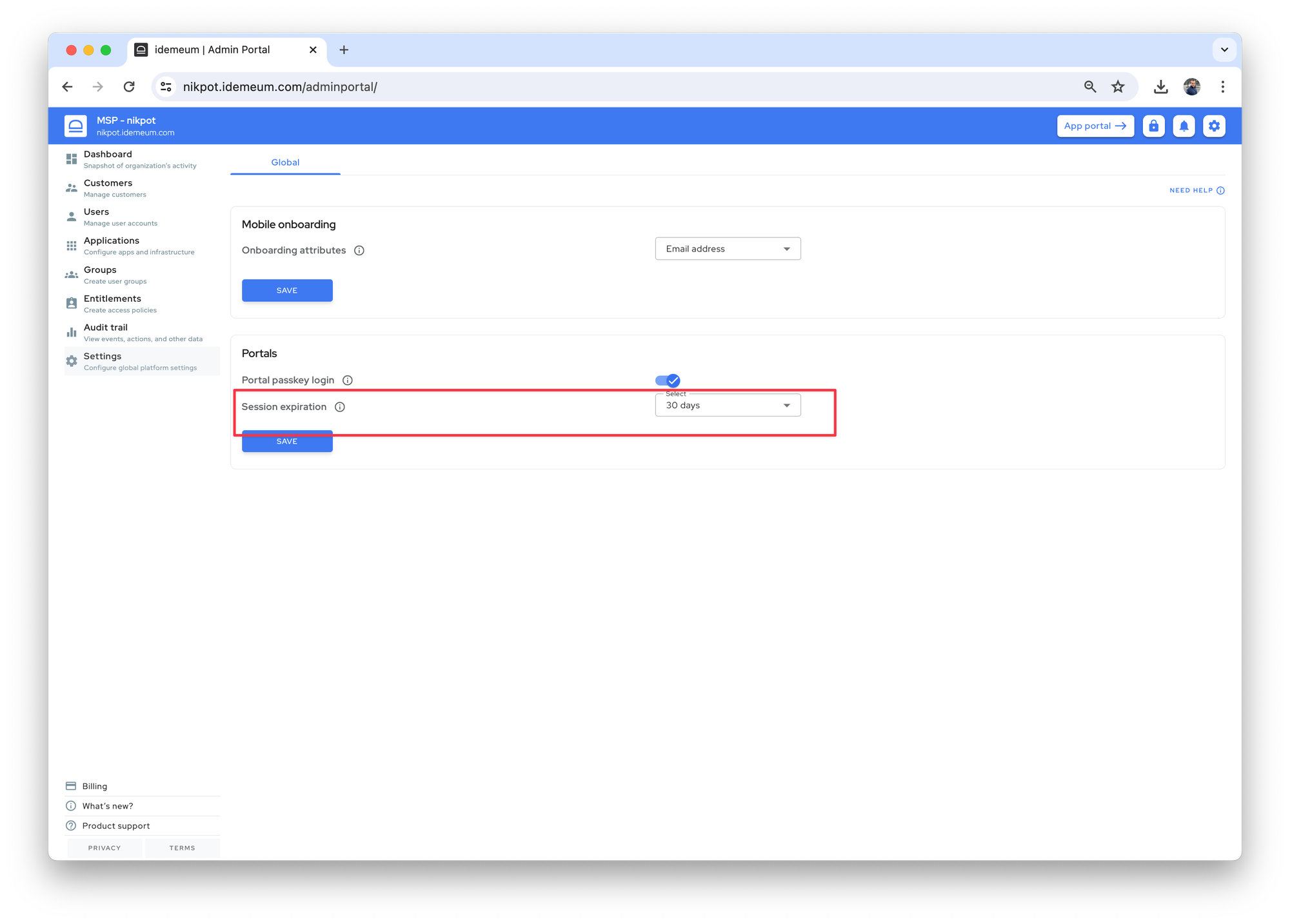
Configure session length
This step is optional, but will improve technician experience when accessing just-in-time accounts. By default the idemeum session length is set to 8 hours, meaning you have to re-authenticate with mobile every 8 hours. You can extend this session to 30 days so that you can seamlessly access JIT accounts for any customer tenant right from HaloPSA and you will stay authenticated for 30 days.
- Navigate to your MSP tenant admin portal
- Access
Settings→Globaland then define theSession expirationduration
Configure HaloPSA
Overview
In HaloPSA you can create a Custom tab that will point to your idemeum tenant. When managing PSA ticket you can click on that tab and get immediate access to your idemeum portal.
You have 2 options for navigation:
- Navigate to parent MSP idemeum tenant - you can simply specify the URL for your MSP tenant, i.e.
<msp name>.idemeum.com. In this case technicians will access custom tab, MSP idemeum tenant will be loaded, then technician will search for customer tenant, access it, and will request JIT account. - Navigate directly to idemeum customer tenant - you can leverage HaloPSA variables to navigate directly to customer idemeum tenant.
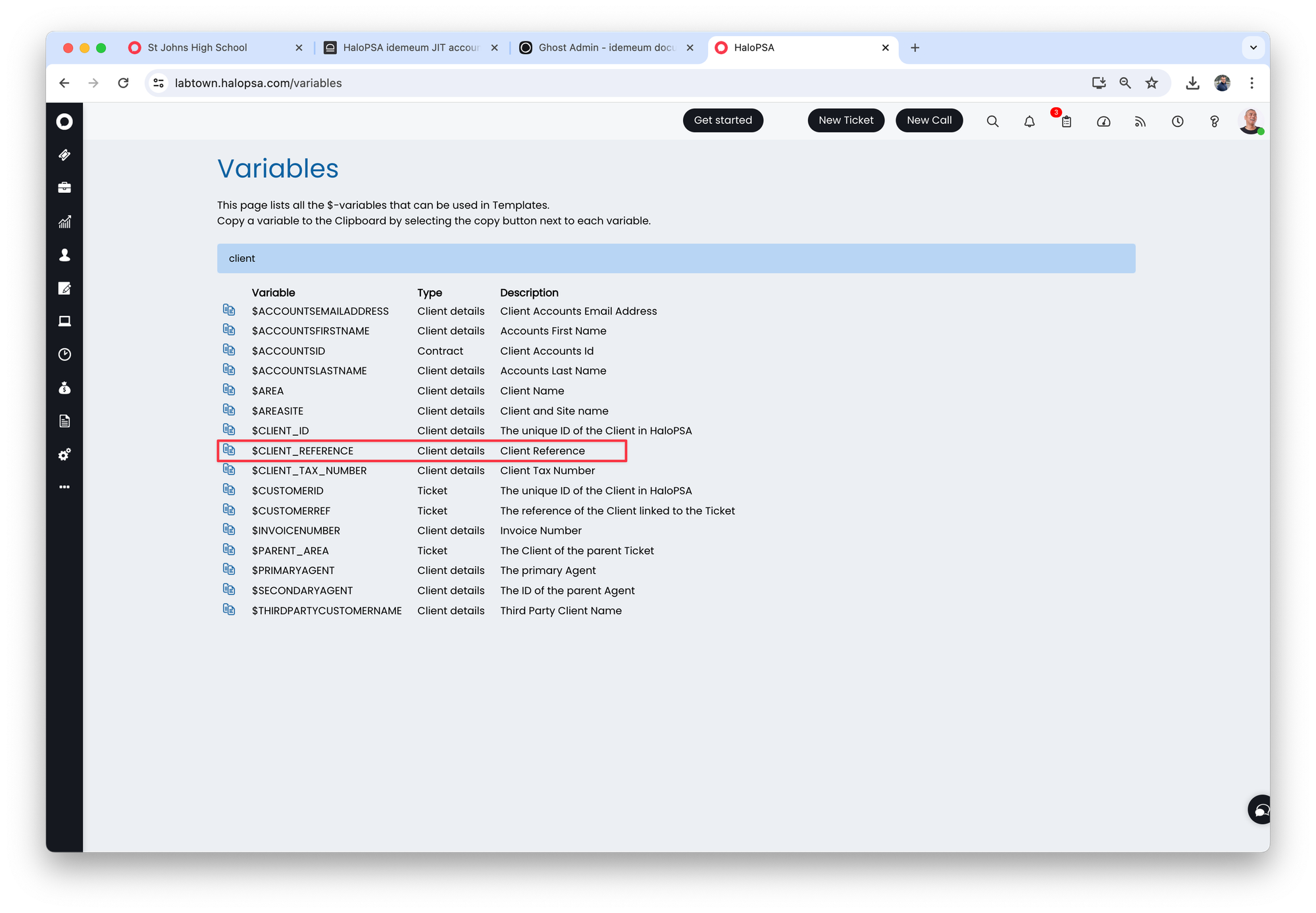
Set up HaloPSA variables
We will set up the integration to directly navigate to idemeum customer tenant from PSA ticket.
- Say we have an idemeum tenant with the display name
Demo PAM tenantand the URLdemo-nikpot.idemeum.com.- We can route based on
Demo PAM tenantwith the following URLhttps://<tenant name>.idemeum.com?customerDisplayName=<value> - Or we can router based on
demoURL with the followinghttps://<tenant name>.idemeum.com?customerName=<value> - In this guide we will use display name
- We can route based on
- In HaloPSA we will use default variable
Client referenceand assign the valueDemo PAM tenantto this variable
- We populate this variable with
Demo PAM tenantvalue in the customer section by simply editing a customer in HaloPSA
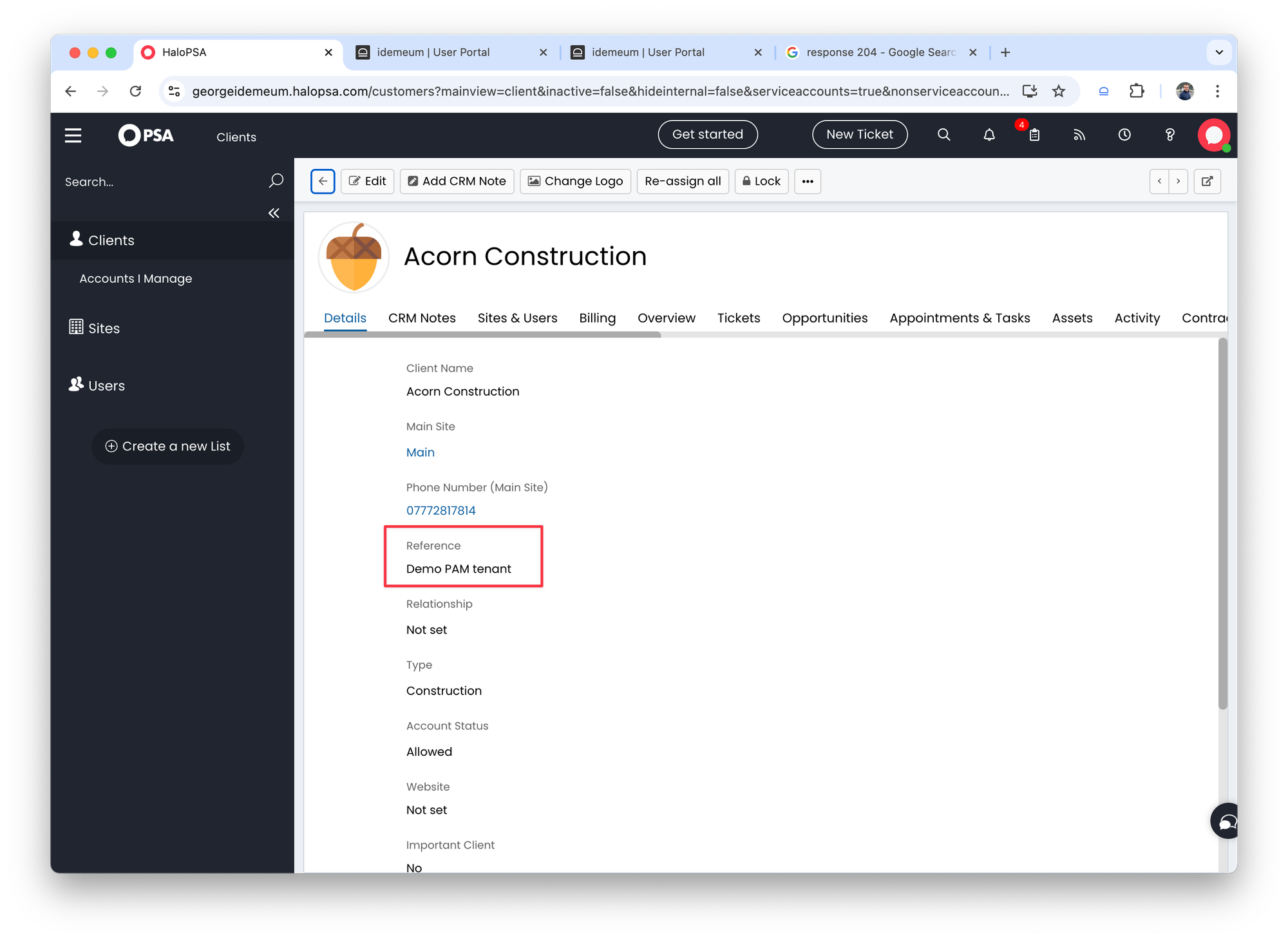
- We can tag all our customers in the same way in HaloPSA so they are mapped to a customer tenant in idemeum with the display name that is used.
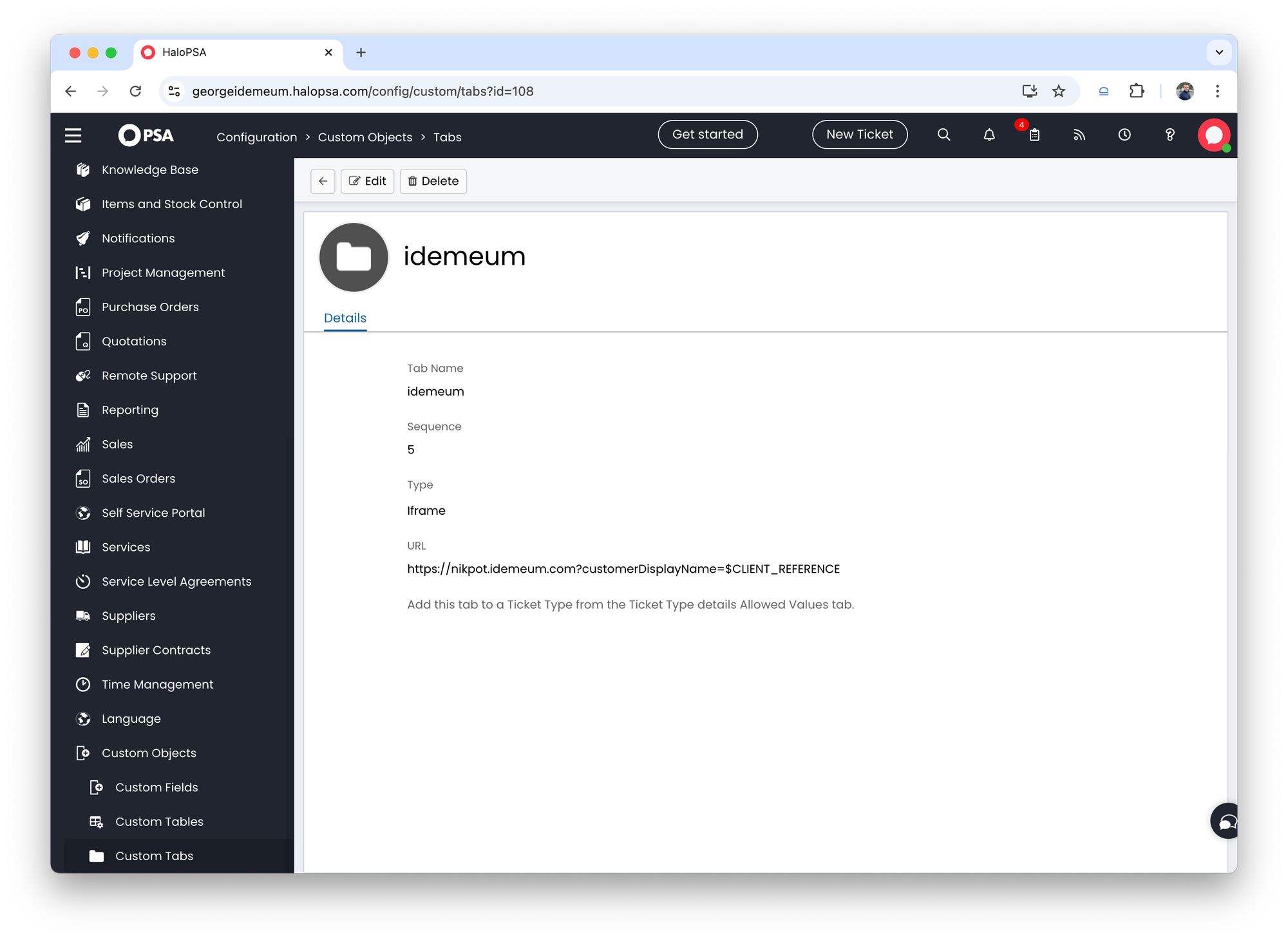
Set up custom tab
- Navigate to
Configuration→Custom objects→Custom tabsin HaloPSA - Create a custom tab like in the image below. As you can see for URL we are using the URL of MSP idemeum tenant, and we are passing a parameter from the variable
$CLIENT_REFERENCE. You can specify the variable that you have chosen for integration.
Test integration
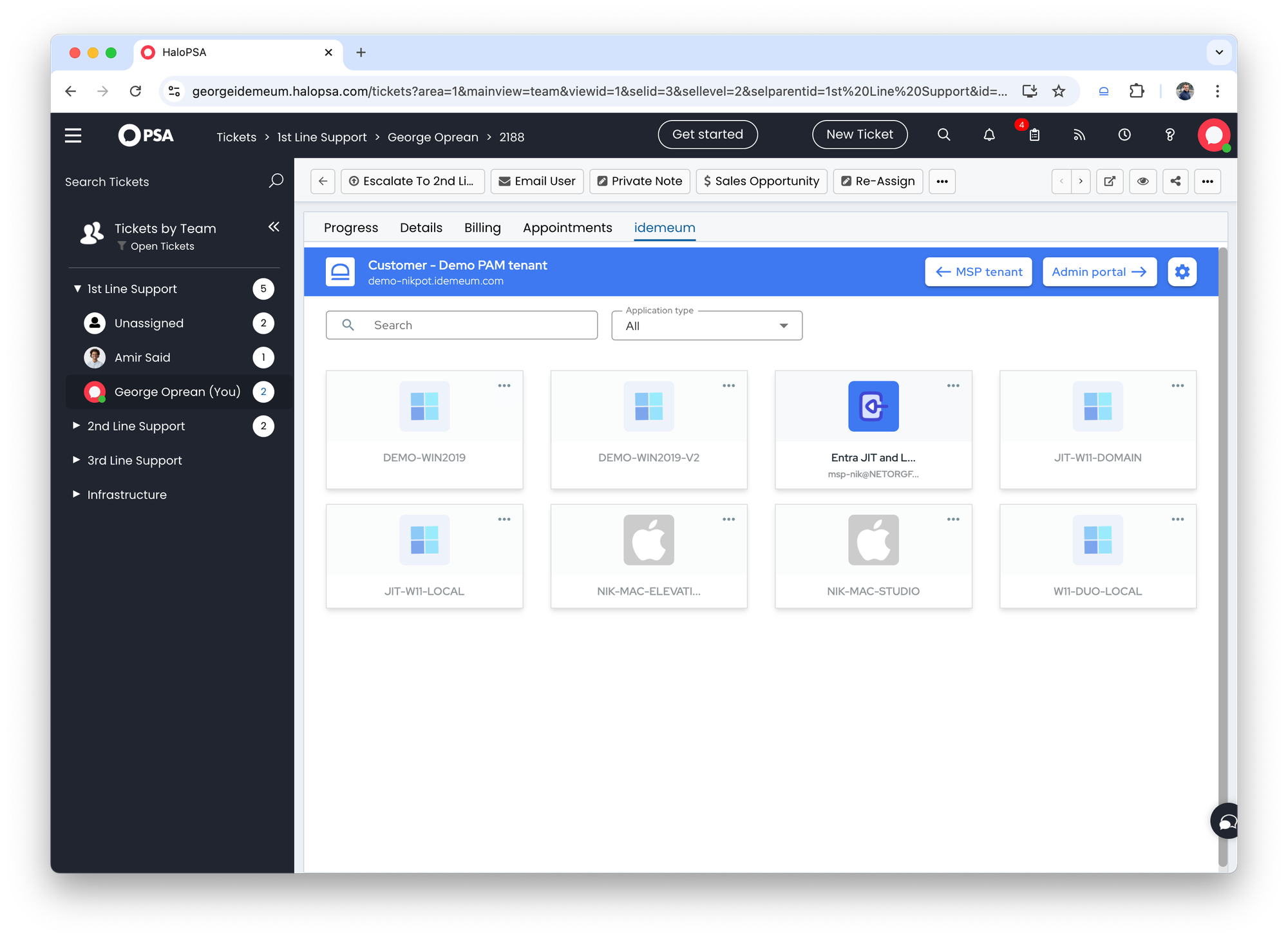
- Open any ticket in Halo PSA
- Click on
idemeumtab - You will be presented with the idemeum user portal for that customer. You can see all workstation and Entra apps to request JIT accounts and view credentials
Disable JIT accounts from HaloPSA
Overview
Technicians can request Entra ID JIT accounts right from HaloPSA with our existing iFrame integration.
However, requested JIT accounts will be disabled after a certain period of time, by default it is 4 hours. If you want to immediately disable these requested JIT accounts, you can leverage idemeum APIs.
Obtain API key
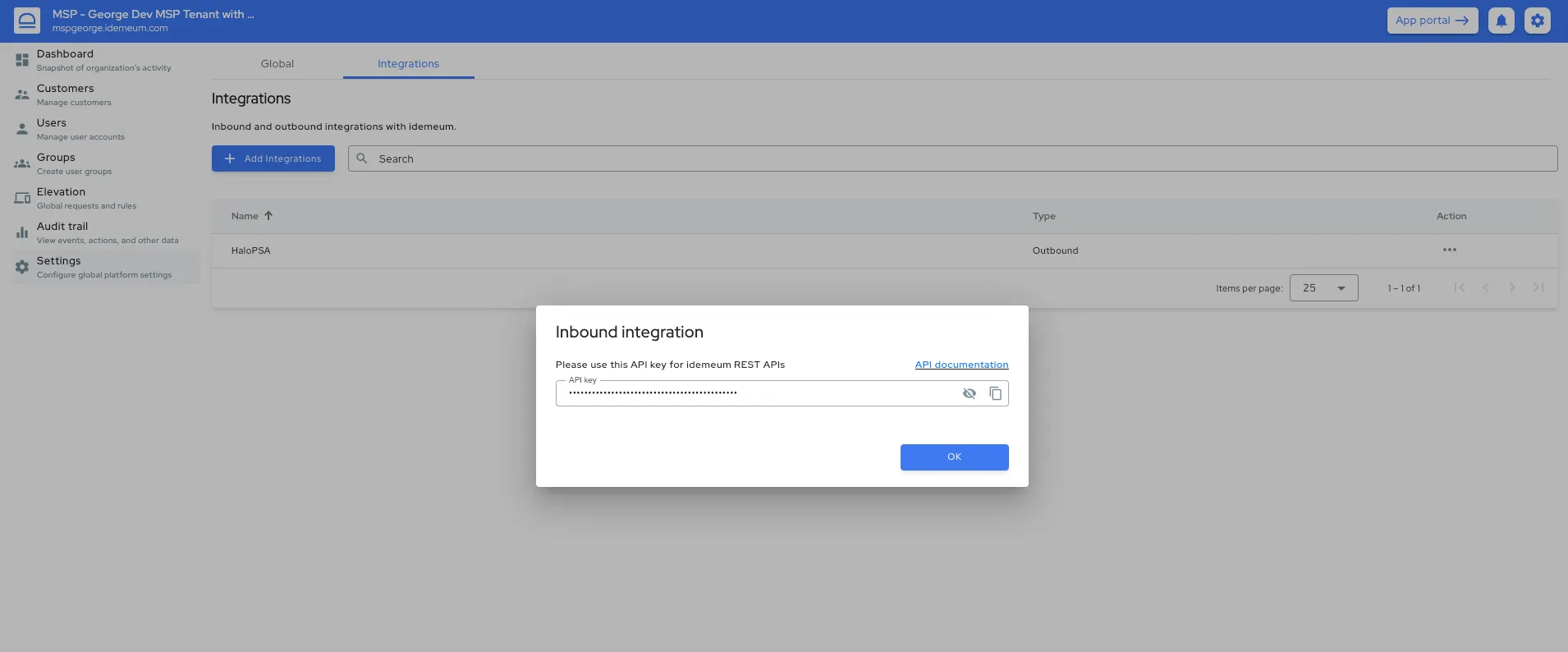
- Access your MSP portal admin dashboard
- Navigate to
Settings→Integrations→Inbound integrationand create a new integration - Provide an integration name
- The API key will be displayed. Make sure you save it somewhere safe as we only display it once (you can always delete the client integration and recreated the client in case you lose the API key).
Configure HaloPSA
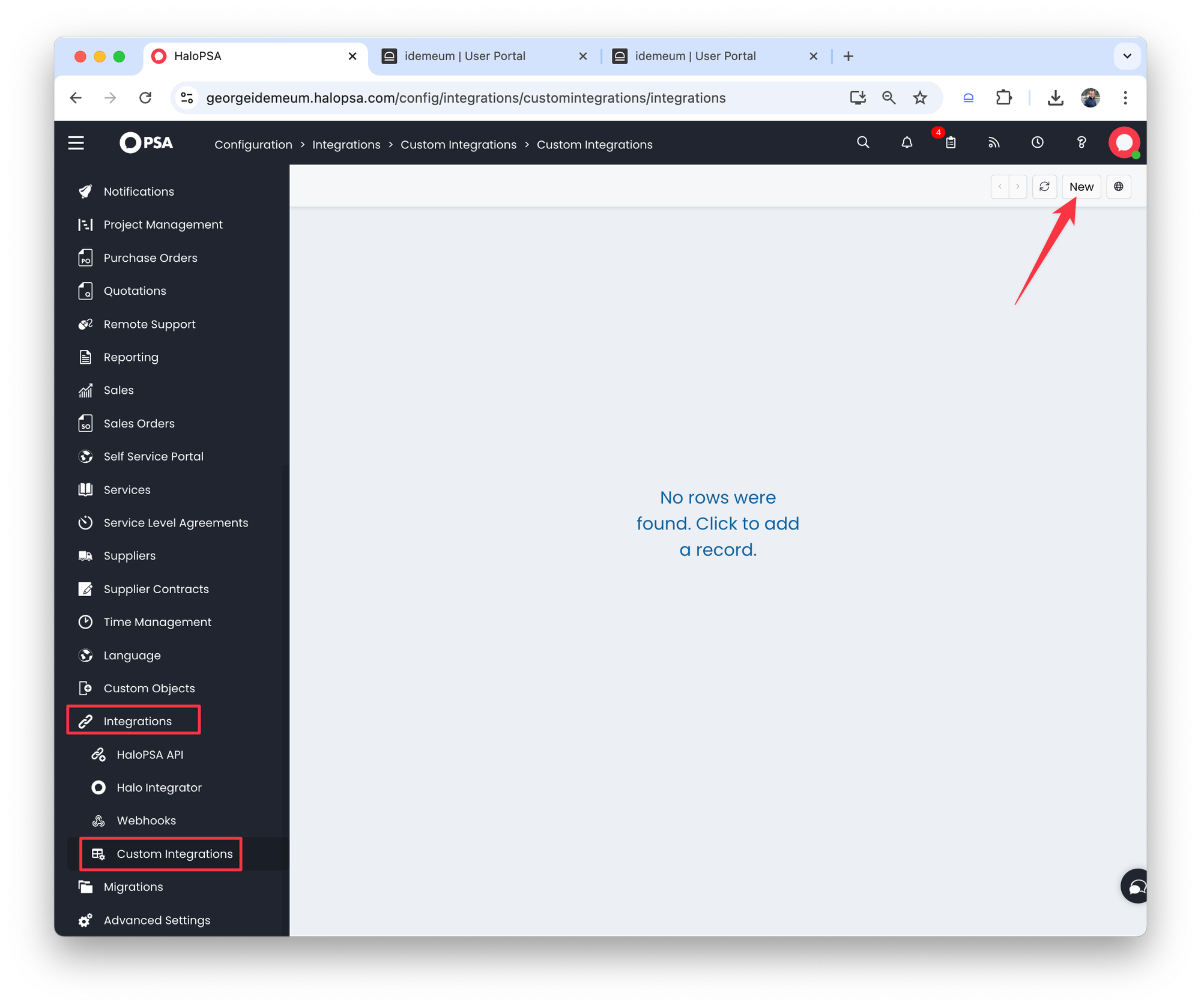
- In HaloPSA navigate to
Configuration→Integrations→Custom integrations - Click
New
- Create an integration and provide the following details:
- Base resource:
https://<yout_tenant>.idemeum.com/api/integrations - Authorization:
API key - Key:
X-Idemeum-Api-Key - Value:
<SDK_API_KEY that you obtained in the idemeum admin portal> - Add to:
Header
- Base resource:
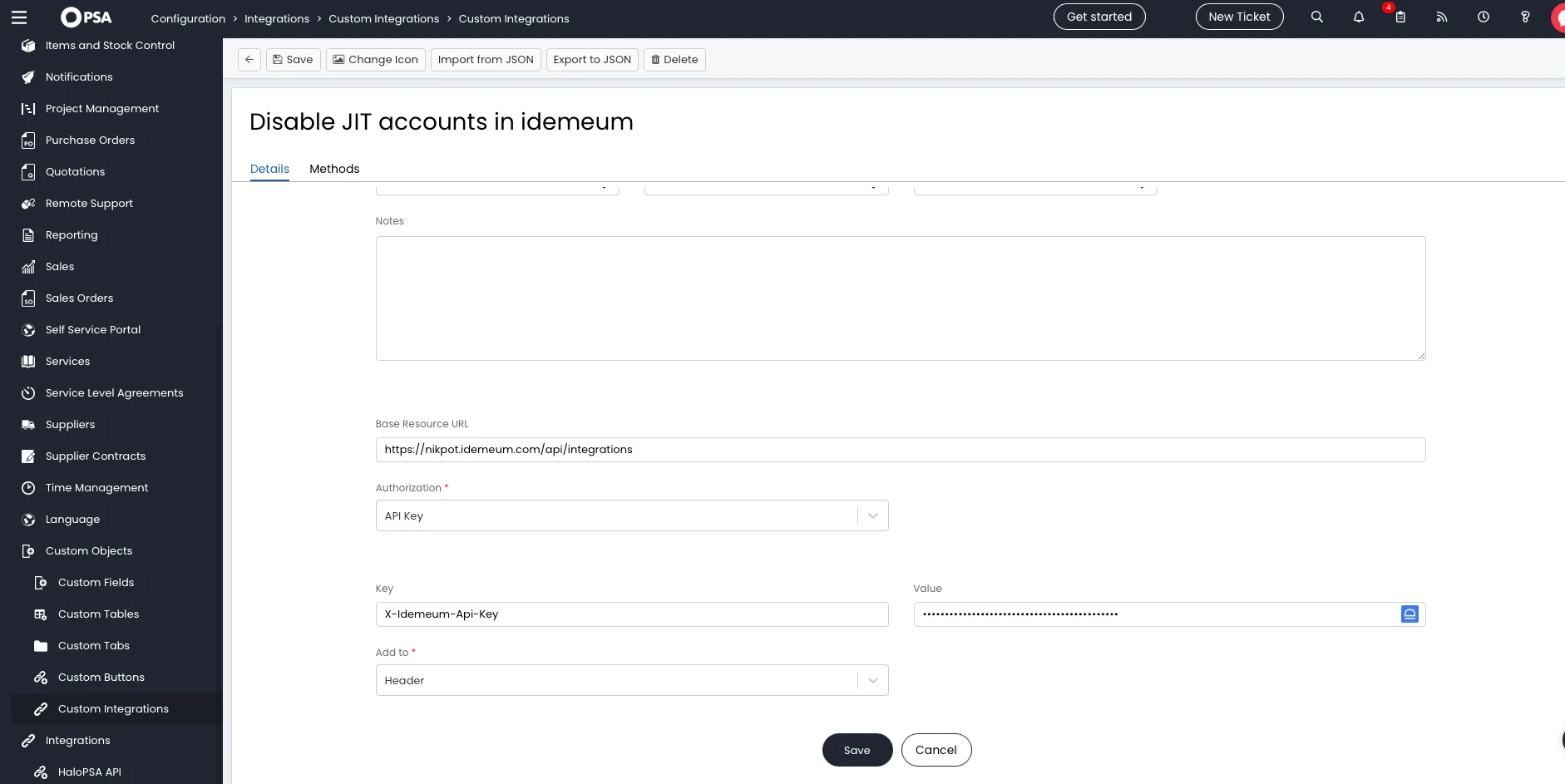
- Save the configuration
- Now in the same tab click on
Methodsto create an HTTP POST method - Configure the following:
- Provide method name
- HTTP method →
POST - Path →
/entrajitaccounts - Headers:
Content-Type: application/vnd.dvmi.entra.app.user.disable+json
- Body provided below
{
"customerDisplayName" : "<your_customer_display_name>",
"technicianEmailAddress" : "<user's email address>"
}As an example here is what we used:
{
"customerDisplayName" : "Demo PAM tenant",
"technicianEmailAddress" : "nik@nikpot.com"
}
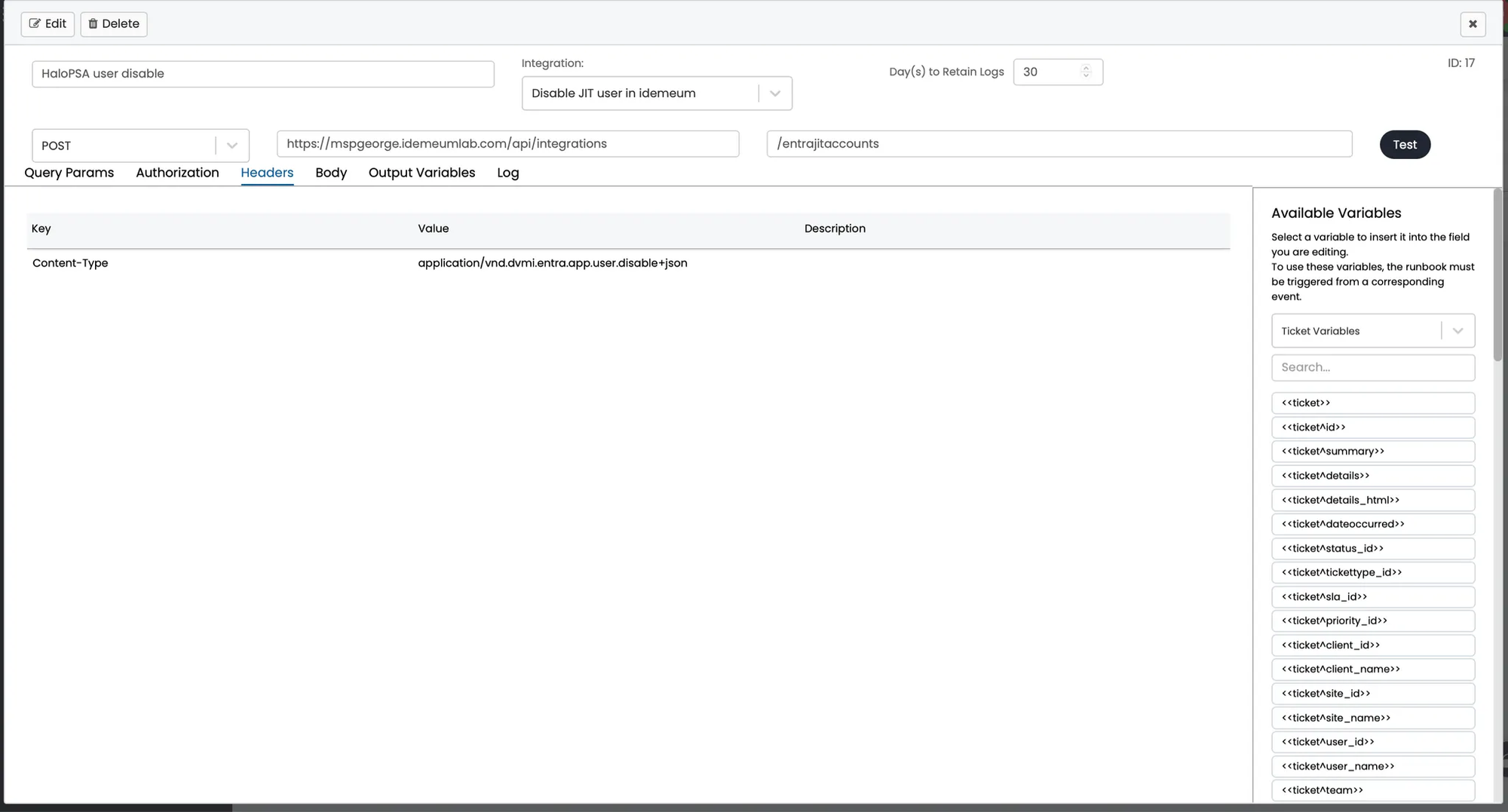
- Once you
Savethe configuration you can test the API call for this integration. You should see the success response. - Now you can navigate to
Integrations→Custom integrations→Integration runbooksand create a run-book to call idemeum API when the ticket is closed.