How to think about allowlisting rules
In this case we are showing the end to end cycle of the rule where both allowlisting and EPM are enabled. You can enable EPM or allowlisting or both.
What is the application?
The first part of the rule is to catch or match the application you are trying to control. Before allowing something, we need to know what we are allowing. You can match the target application using
file attributes (hash, name. path, etc.), publisher thumbprint (the hash of the certificate that is used to sign the executable, or certificate elements (when application is signed you can use certificate elements of the signing certificate to match the app).Allow execution?
With allowlisting the default policy is to
default deny everything. if you want to allow an application you need to allow execution, otherwise the application will not launch.Control what app is doing?
With application fencing you can control child process execution or application interactions (i.e. notepad can not launch command prompt). You can allow all child processes if you trust the application, or define the custom set of processes that application can launch.
Allow elevation?
If an application requires admin privileges, and you maintain standard rights for all users, you can allow the application to automatically elevate.
Rule best practices
These are some of the best practices related to rule management:- Give rules descriptive names so that you know what the rule is doing
- The best rules are the ones that leverage
certificate elements. For instance you create a rule that allows everything that is signed by certificate belonging toZoom Inc. - If you do not want to use certificate elements, use
certificate thumbprint. This is second best. Allowing the whole organization might be too broad, but allowing a certain publisher certificate is a good balance. When the application is updated, rule will still work. But if the organization renews the certificate, you will need to update the rules. - If the application is not signed and you can not use certificates, then use
file attributes. Bear in mind thathashbased rules are the worst, because if the application is updated, the hash will change, and the rule will no longer work. For applications that launch from protected paths, you can leverage thepathrules, for instance for Windows apps that launch from protected directory.
Allowlisting rules examples
Slack allowlisting rule
We match Slack application using the publisher certificate, allow application execution along with all child processes, and allow the application to automatically elevate as admin.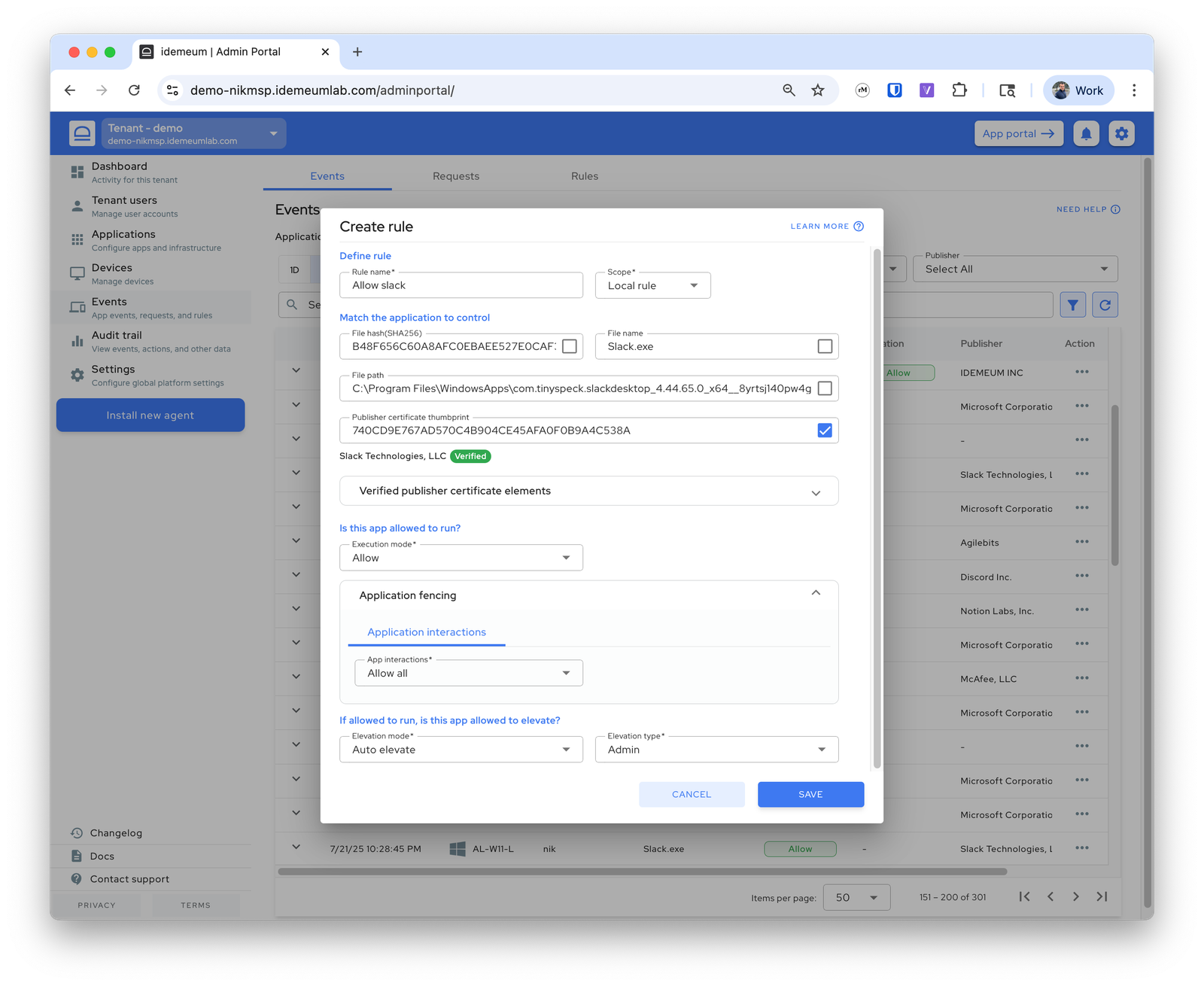
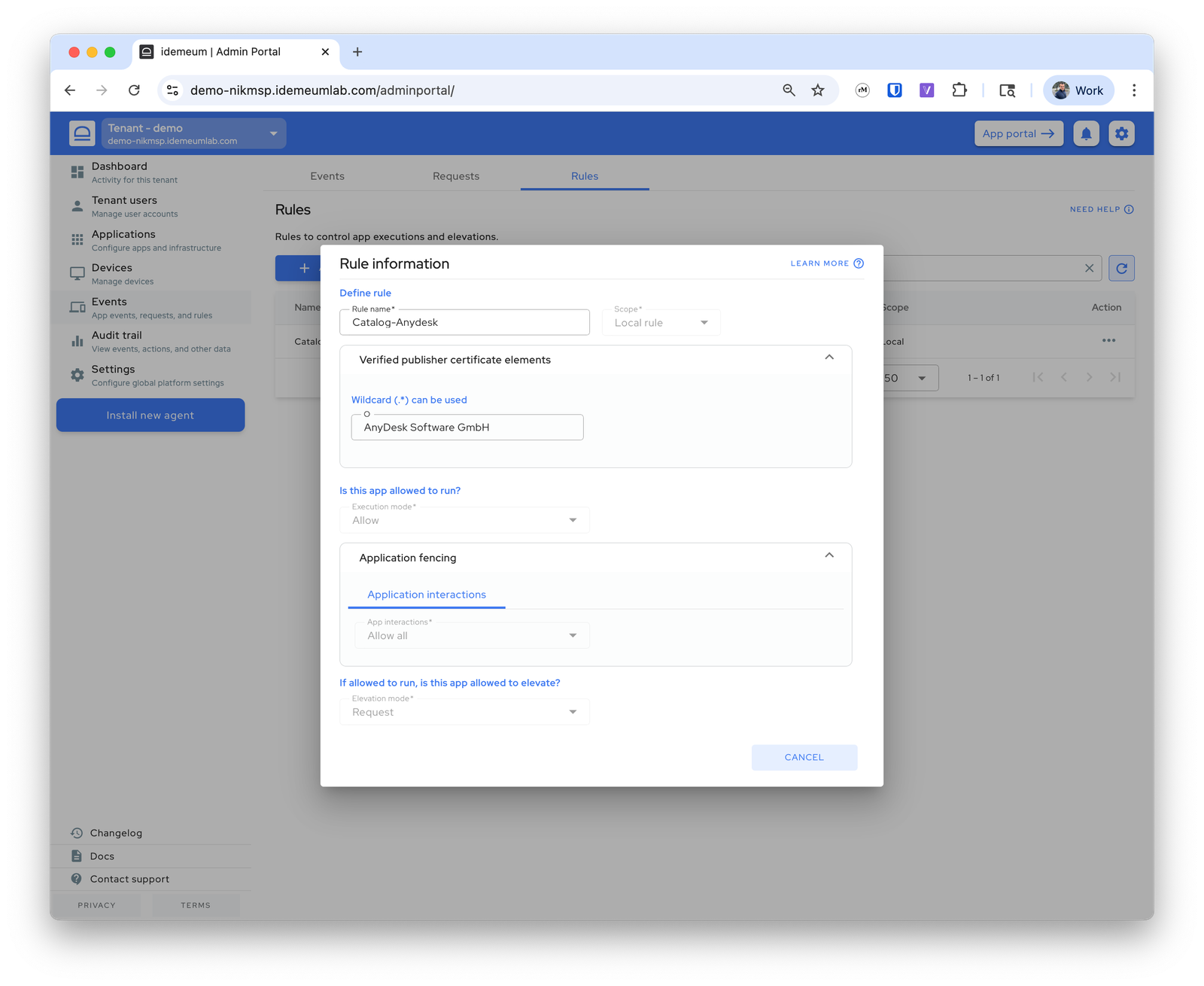
Anydesk allowlisting rule
This is a catalog rule managed by idemeum. It matches the application that is legitimately signed byAnyDesk Software GmbH, we allow execution, and offer users the option to request elevation.
Catalog rules
Idemeum comes pre-configured with allowlisting and elevation rules for most common applications. We constantly update applications to make sure the rules are current and do not create any disruptions. With a click of a button you can allow most used applications in your environment. Learn more about catalog rules.Create allowlisting rule
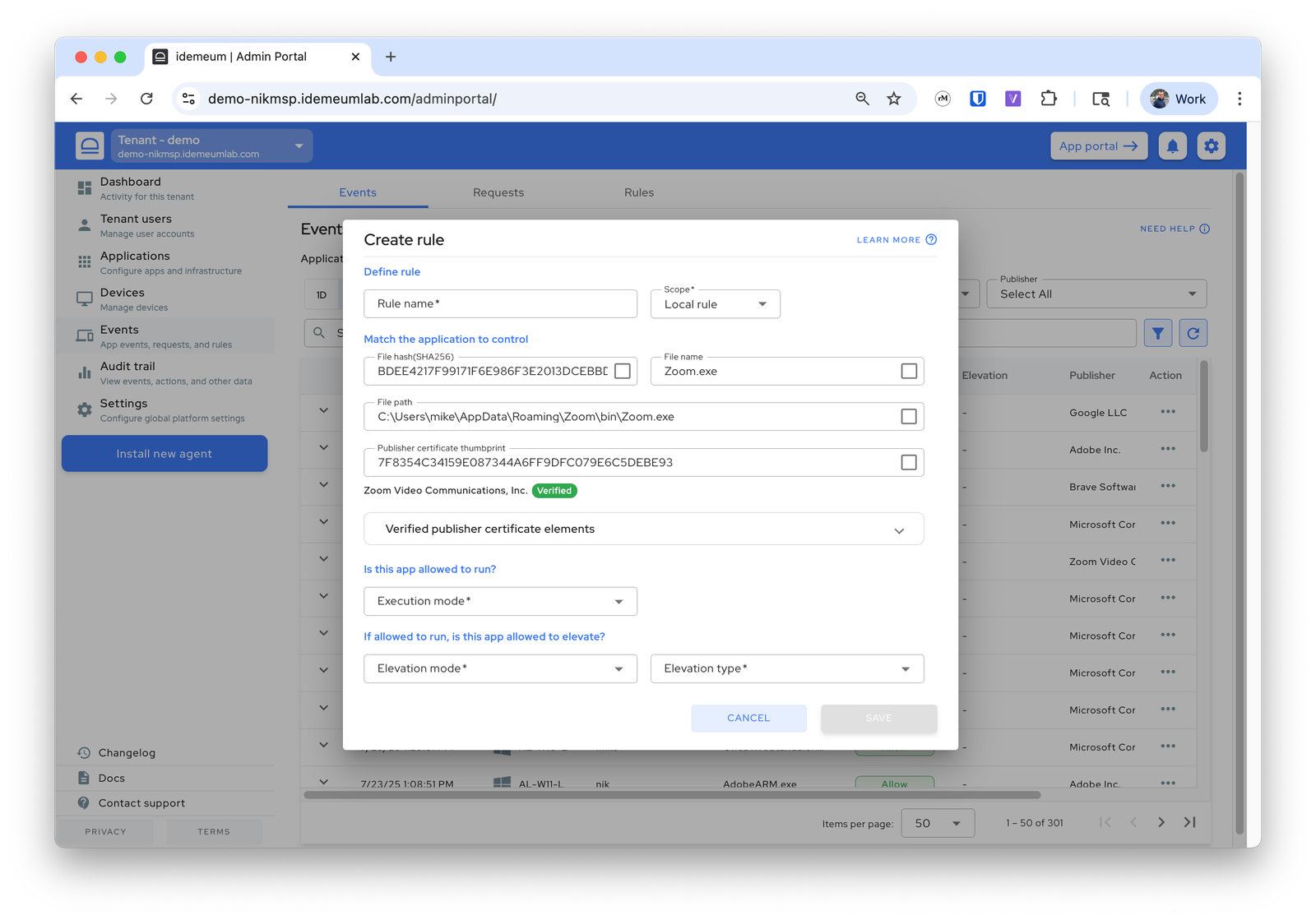
If you want to create your own custom rules or allow applications that are not listed in idemeum catalog, you can simply do that from the event. Launch the application you want to allowlist (or trigger elevated launch), the event will be generated and sent to the cloud. Now you can create rule from the event.- Navigate to the admin portal of your idemeum tenant
- Access
Eventssection - Search for the application / event that you want to create a rule for
- Click on
...and choose to create a rule - All metadata for the event will be pre-populated and you can choose how you would like to match the application and what execution policy to apply.
- Save the rule
Regular expressions
Idemeum rule engine supports regular expressions when matching the applications using various attributes. We support regex forfile name, file path, and certificate elements. We use case-insensitive match.
- Match the exact file name for the edge browser
- Match any filename that contains
video
- Match the path that starts with
C:\Program Files\WindowsApps\and then containslinkedinin the path
- Use this in
Ofor certificate element to match anything that is signed by organization that containsMicrosoft