Allowlisting events
Events represent all executions and elevations triggered across your workstations.
Overview
- Events are captured on workstations when applications get executed (allowlisting) or elevated (elevation control)
- For execution, idemeum agent tracks
msiandexefiles - There are no duplicate events, and each event is uniquely represented by a combination of a
file nameandparent process. If several events for a file name / parent combination get pushed to the cloud, only the latest event is shown with the updated timestamp. - Allowlisting execution events are uploaded to idemeum cloud every 5 minutes
- Elevations events are uploaded to cloud in real time
Event structure
To access events navigate to your organization / customer admin portal and access Events section.
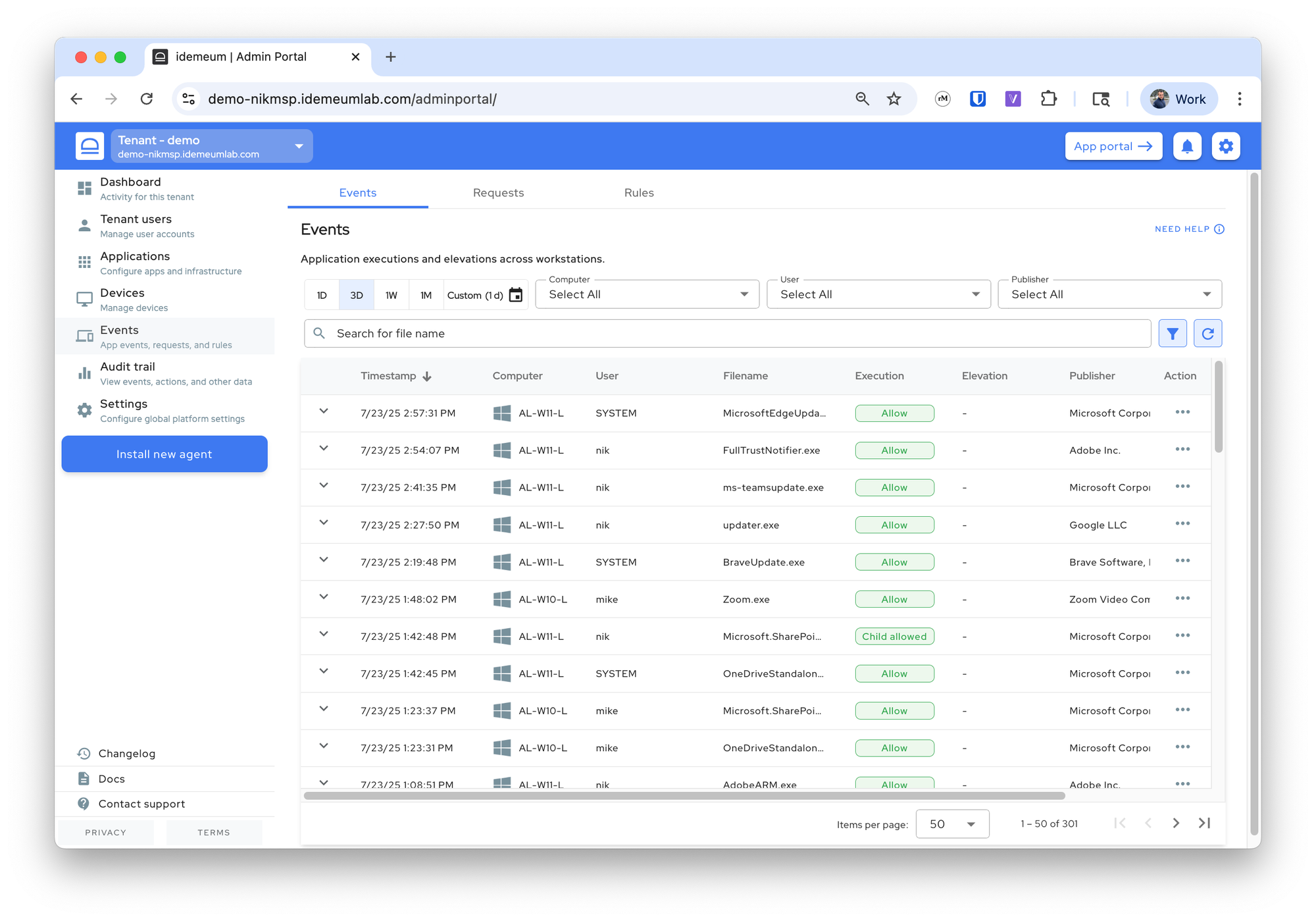
Timestamp- date and time for when the execution or elevation happenedComputer- workstation that generated the eventUser- user that was logged into the computer when event was generatedFilename- file name of the executableExecution- tag that shows whether the application was allowed to execute or not. When in audit mode, the tag will beAuditas there are no rules enforcement. If you hover over the tag, you will see the rule that is matching the execution based on which the decision is made.Elevation- tag that shows whether the application was allowed to elevate or not. For standard non-admin executions this tag is not shown.Publisher- organization that signed the executable. If you expand the event, you will be able to see whether the publisher is verified by operating system or not.Parent- parent process that was responsible for launching the executableActions- actions that you can take on the event, including rule creation
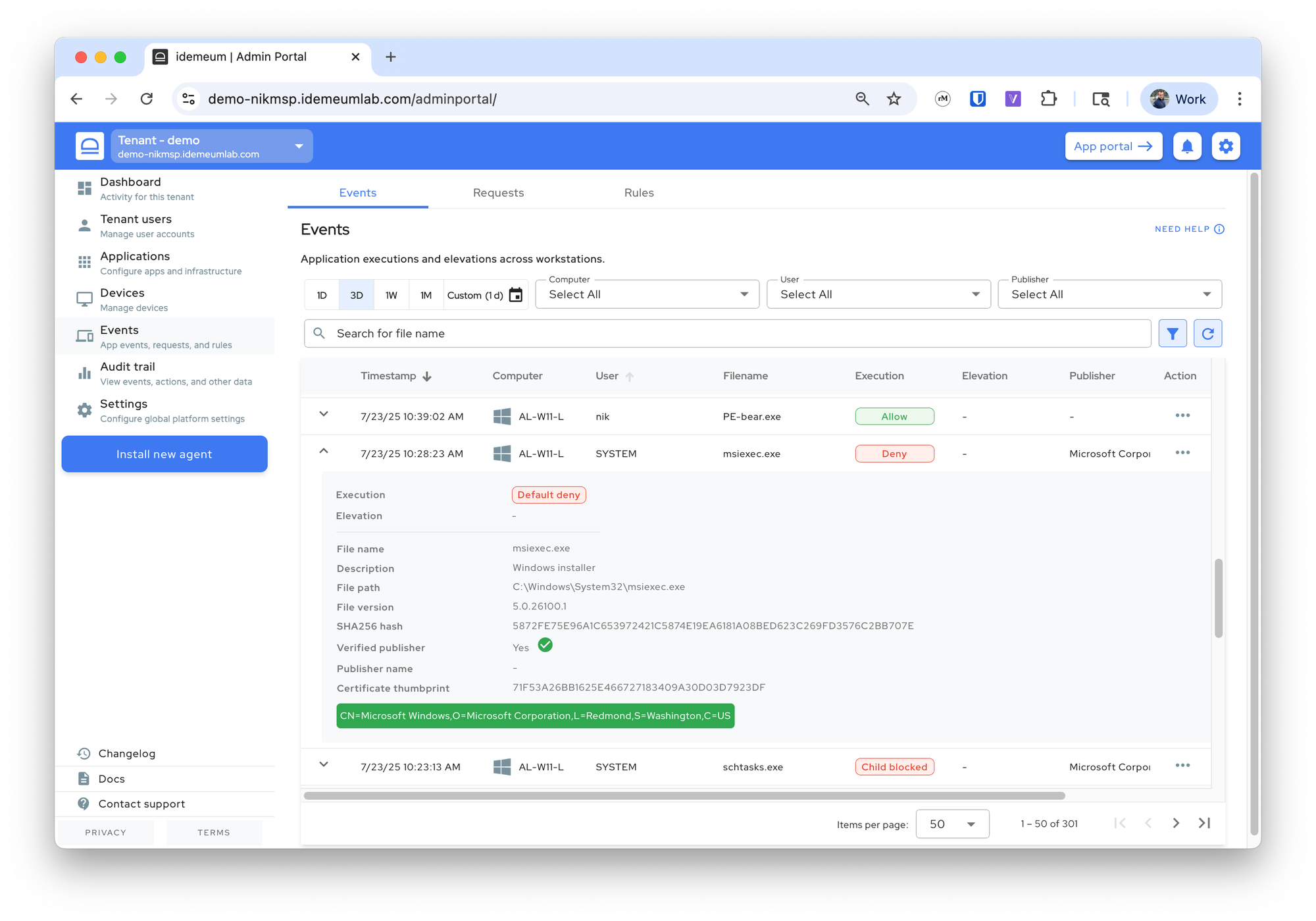
If you click on the event, you will be presented with the detailed information, including hashes, verified publisher, path, and more. At the bottom of the event section you will find the publisher certificate elements (i.e details of the organization that signed the executable). The green checkmark indicates that the publisher is verified by operating system.
Understanding events
Let's review the major cases of events that you will encounter in idemeum. Here we assume both Allowlisting and Elevation are enabled for the customer / organization.
Execution without elevation
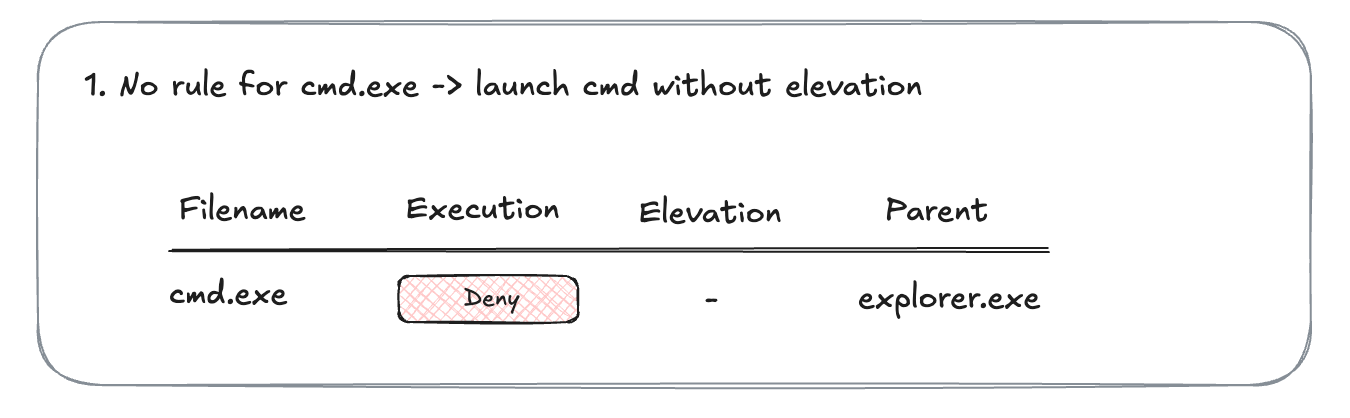
- Let's say there is no rule for
cmd.exe. You launchcmd.exe, and it gets blocked. There is one execution event generated.
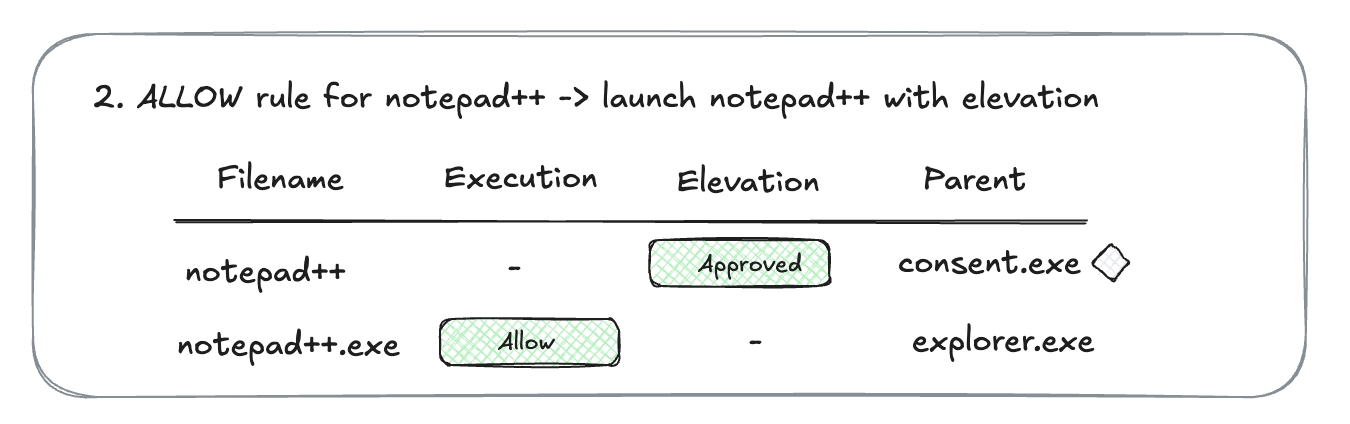
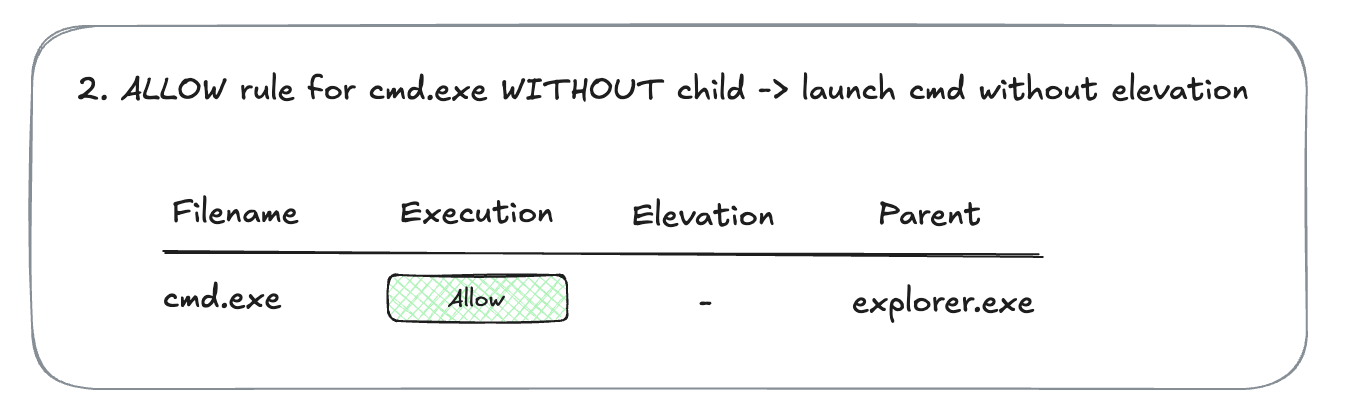
- Now you create a rule for
cmd.exeto allow execution, but not allowing child processes. You launchcmd.exe, and it is allowed.
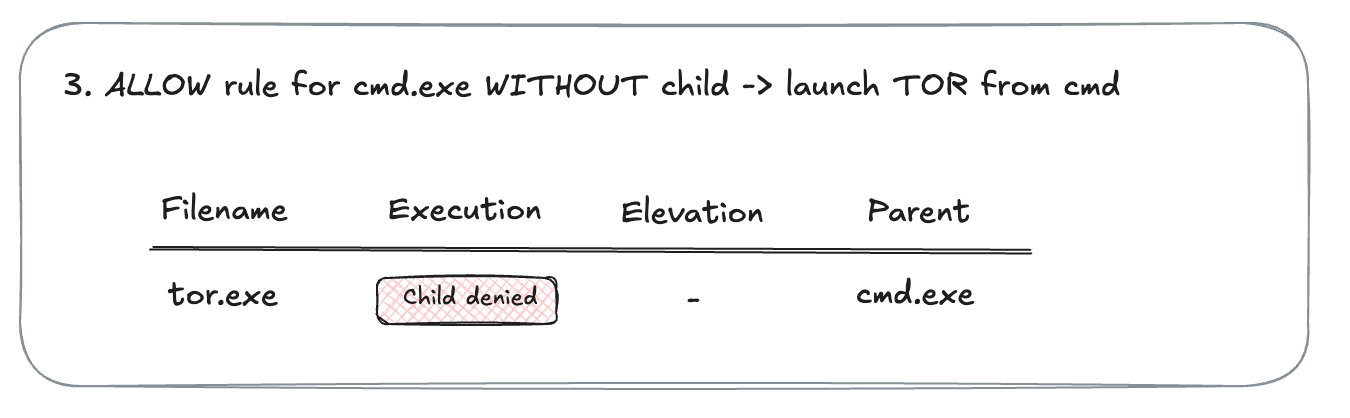
- Now you try to explore child process control. You have a rule for
cmd.exeto allow execution, but not allowing child processes. You launchtor.exefromcmd.exe. The TOR launch is blocked. And in the event you can see the message that child process is denied.
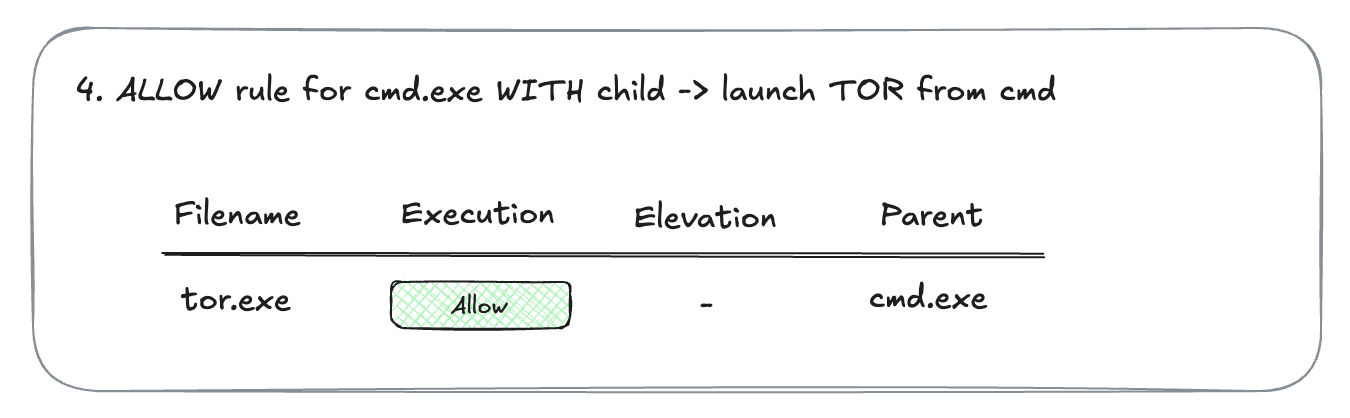
- Now you create a rule to allow
cmd.exeand also allow child processes. You launchtor.exefromcmd.exe. The execution is allowed.
Execution with elevation
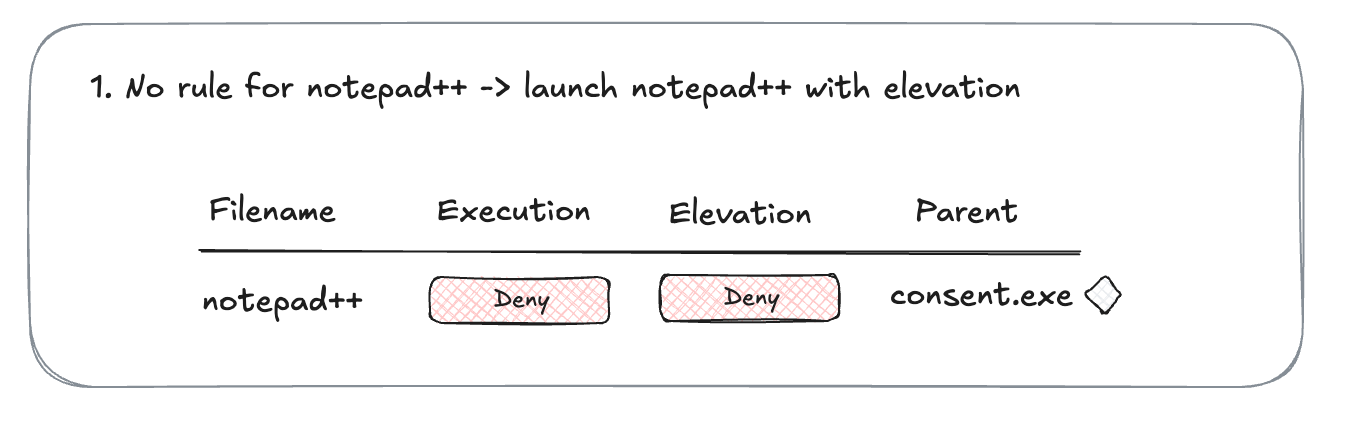
- Let's say you do not have a rule for
notepad++.exe. Execution is not allowed, and elevation is not allowed. When you triggernotepad++installation, the elevation screen is presented and the application is blocked. One event is generated with both execution and elevation denied.
- Now you have created a rule for
notepad++.exe. You allow execution and configure the application to automatically elevate. When you triggernotepad++installation, elevation screen is presented and then allowed. Installation goes through. There are two events generated - one for elevation, and one for successful execution.