User source integration
Idemeum offers fully-featured local directory, or you can leverage external user source, such as HR system, or Identity Provider to sync and manage your users.
Local directory
You can create user records manually in idemeum cloud directory and specify various attributes, including RFID badge ID values or personal identity claims.
Create local directory
To configure local user source:
- Navigate to
Users->User sourceand chooseLocal - Once you save your configuration. you can navigate to
Users->User Managementsection to start creating users
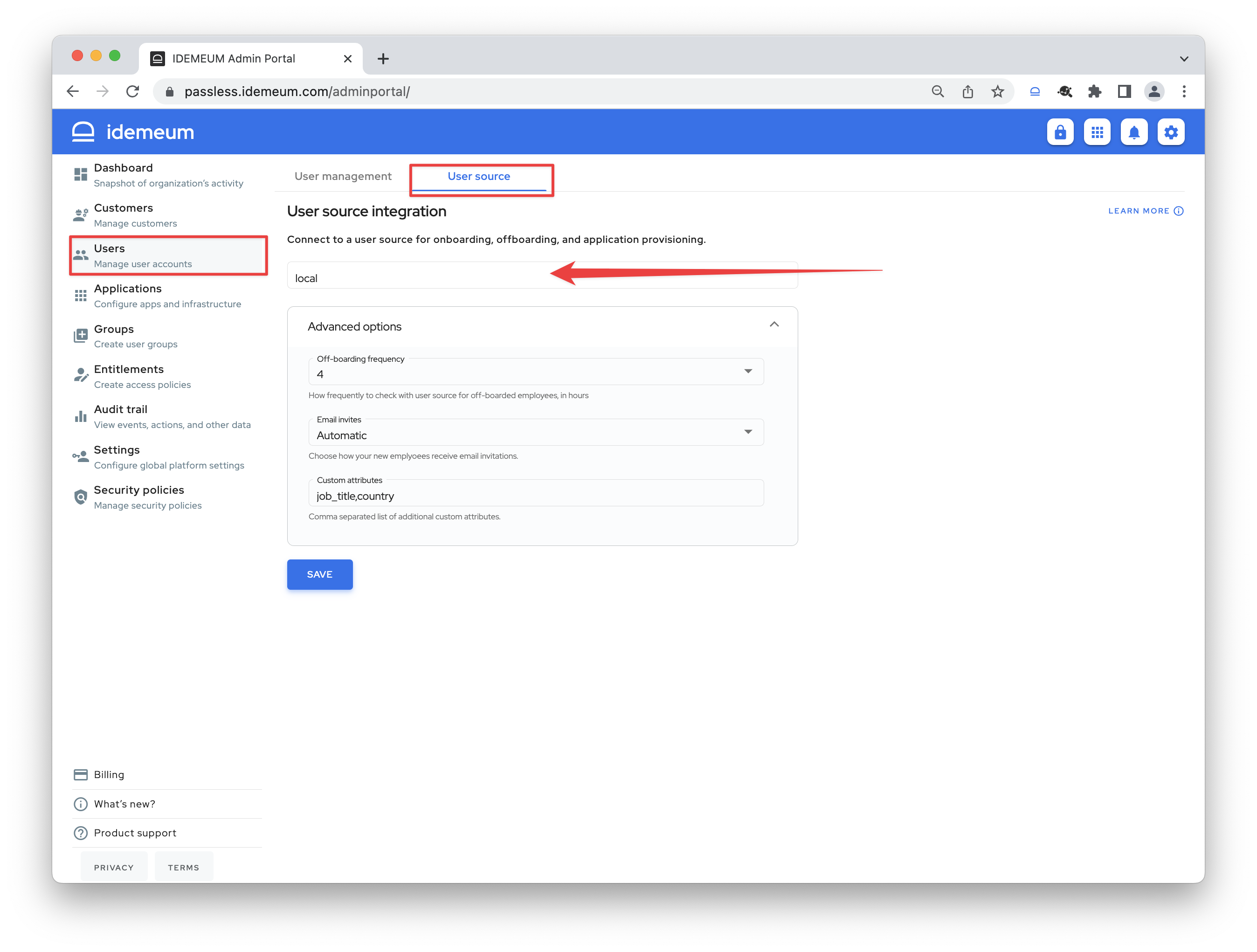
Configure advanced settings
You can configure the following parameters:
- Off-boarding frequency - with this configuration you can choose how often you want idemeum to check for off-boarded employees using local user source. Say you delete user manually, and set this interval to 4 hours. Every 4 hours idemeum will check for off-boarded user to remove access and de-provision applications.
- Email invites - choose to either automatically send invitation email to users as soon as they are added by administrator or manually through user actions on user management tab.
- Custom attributes - define additional attributes that can be added to local users. You can list comma-separated attributes (i.e. job_title, country, etc.)
External directory
External user source allows to leverage existing user database for automated user onboarding or RFID badge lookup. Users do not need to be manually created in idemeum, and it is expected that external user source will have a mapping between corporate email address and personal user information for onboarding to work.
Connect to external directory
Today we support a variety of integrations, and you can check our integrations portal here - user source integrations.
- To connect idemeum to external user source navigate to to
Users->User source - Then choose the source that you want to connect to from a dropdown list
- Then you will need to either enter an API key or conduct an oAuth authorization
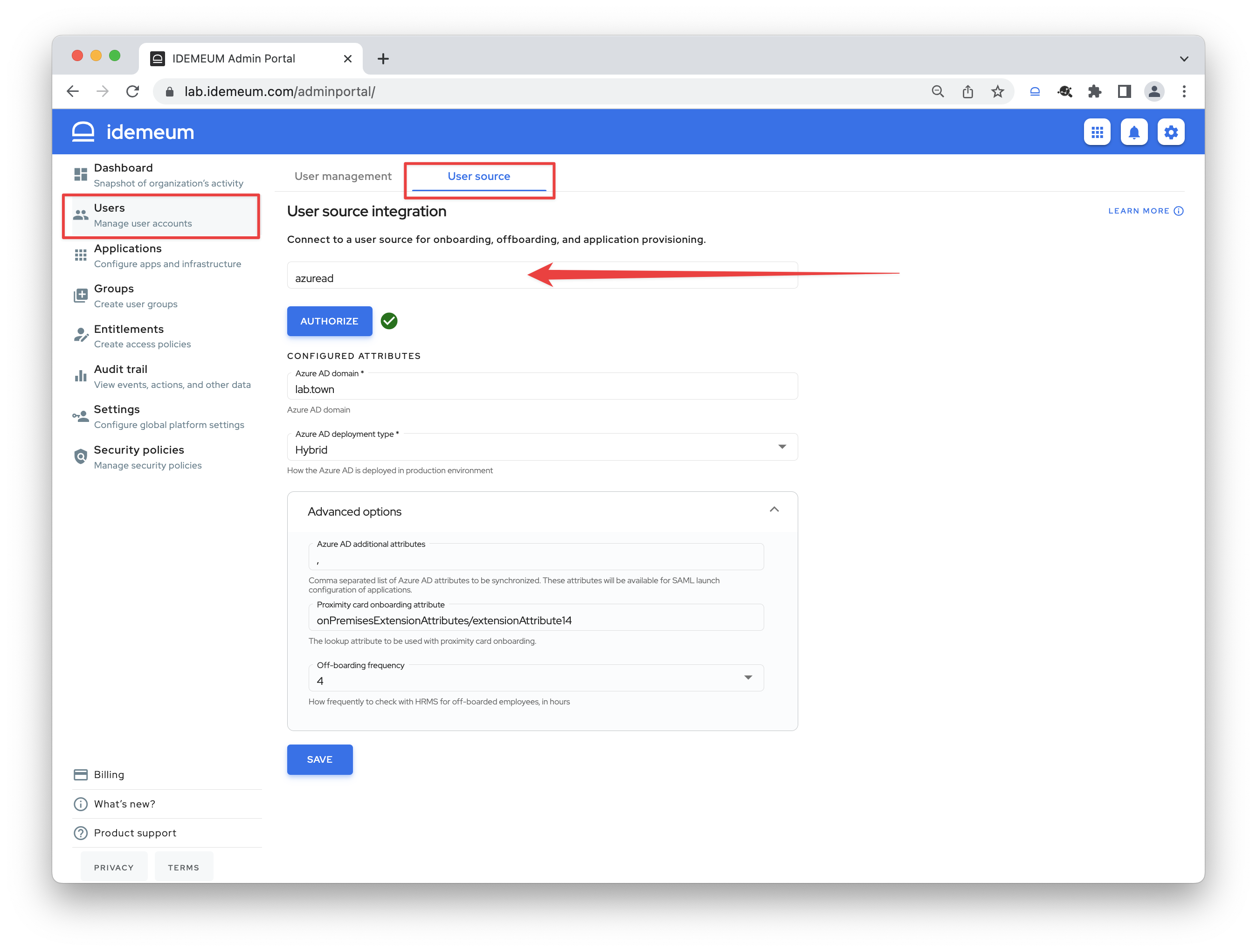
Configure advanced settings
- Off-boarding frequency - with this configuration you can choose how often you want idemeum to check for off-boarded employees using local user source. Say user is deleted in HR system, and you set this interval to 4 hours. Every 4 hours idemeum will check for off-boarded user to remove access and de-provision applications.
- Proximity card onboarding attribute - the lookup attribute to be used with RFID badge onboarding.
Directory attributes
idemeum supports user attributes which can be used as expression for applications, for example you can use user attributes to combine users into groups.
Here is the general syntax for how to use user attributes - ${user.attribute-name}. In this example application will resolve the expression using user attribute named attribute-name value.
Local directory attributes
When you use local directory, you can use built-in attributes that are available out of the box.
| Attribute | Expression | Description |
|---|---|---|
| first_name | ${user.first_name} | User first name |
| last_name | ${user.last_name} | User last name |
| ${user.email} | User email address | |
| phone | ${user.phone} | User phone number |
| fully_qualified_did | ${user.fully_qualified_did} | User unique identifier i.e. did:dvmi:a358000f-2843-4f02-b662-864491a7c9ad |
You can also custom attributes based on your needs. For instance, let's add custom attribute job_title so that we can leverage this attribute in user groups.
- Navigate to idemeum admin portal
- Access
Users->User source - Make sure you have local directory configured
- Expand
Advanced optionsand enter any custom attribute you want in theCustom attributessection. If you need to specify multiple attributes, you can use comma to separate attribute names.
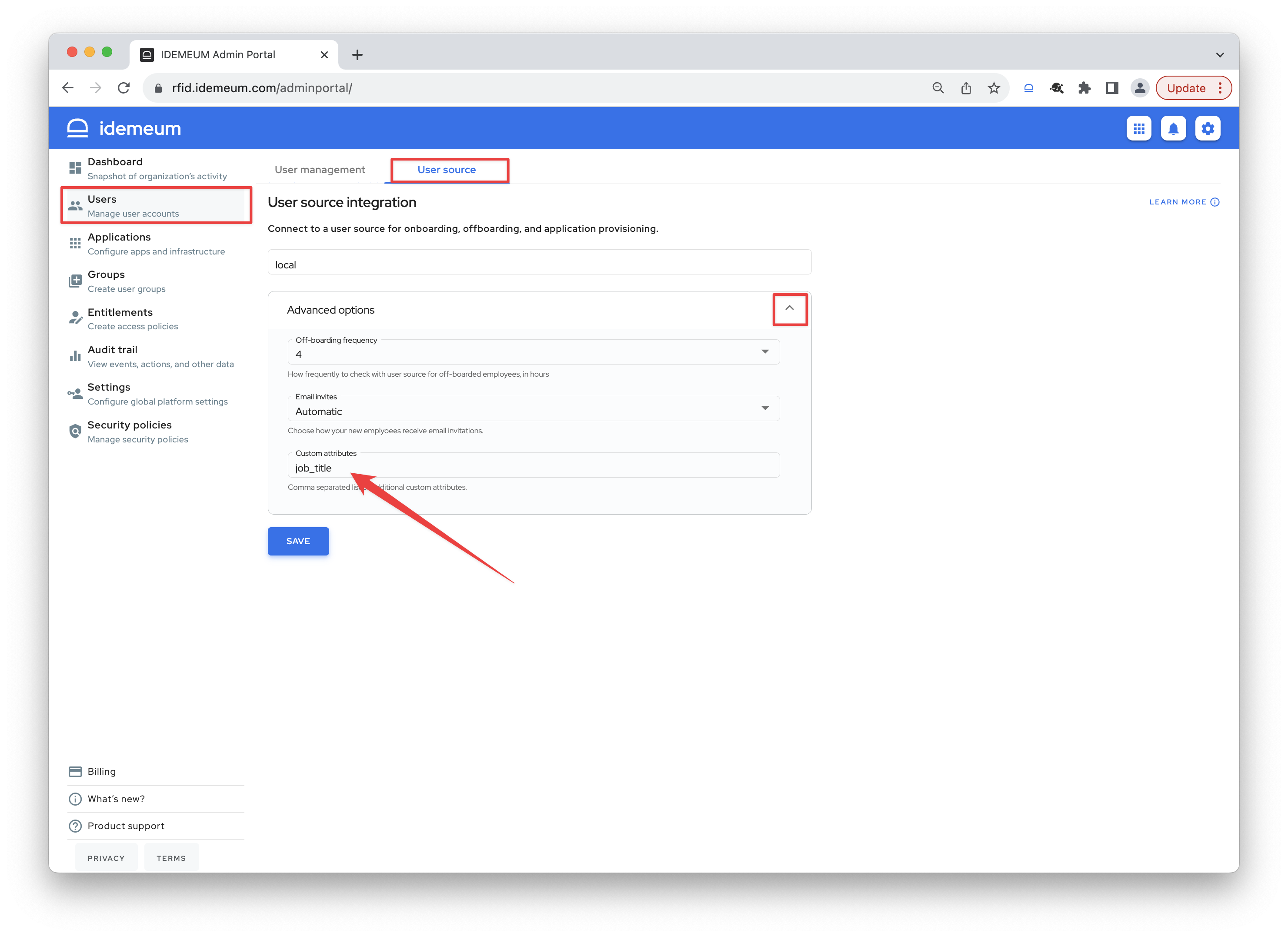
Now you can leverage this attribute in the Groups section, and you can reference this attribute in provisioning and other areas as ${user.job_title}
External directory attributes
Today we support external attributes when Azure AD is leveraged as external user source. Here are the attributes supported for Azure AD today:
| Attribute | Expression | Description |
|---|---|---|
| first_name | ${user.first_name} | User first name |
| last_name | ${user.last_name} | User last name |
| ${user.email} | User email address | |
| phone | ${user.phone} | User phone number |
| fully_qualified_did | ${user.fully_qualified_did} | User unique identifier i.e. did:dvmi:a358000f-2843-4f02-b662-864491a7c9ad |
| job_title | ${user.job_title} | User job title |
| department | ${user.department} | User department |