Master key
What is master key?
Idemeum desktop client handles sensitive information, including user credentials. In order to achieve the highest level of security and client-side encryption, a symmetric encryption key is generated for each cloud tenant. This key is only known / visible to you, and it is used by the desktop client to encrypt all sensitive information, including user passwords. When you install idemeum desktop agent, you explicitly pass the key as part of installation command. Even if idemeum cloud is compromised, your credentials will never be exposed.
How to view master key?
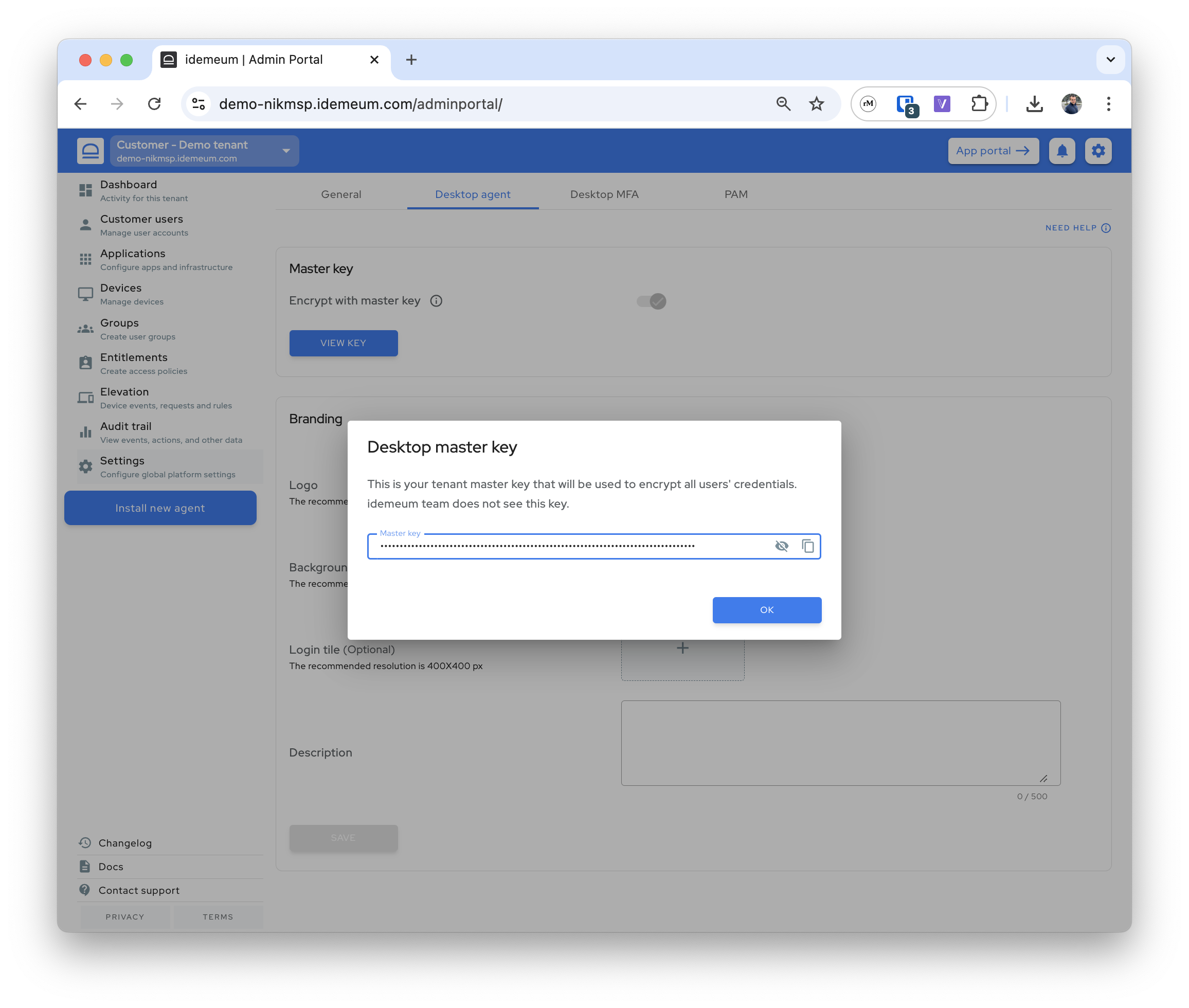
- Navigate to any of your customer tenants
- Access
Settings→Desktop agent→Master keyand clickView key
❗
idemeum does not see your master key. It is generated in the browser on the client side and is encrypted with your mobile key. Therefore, key is always visible to you and other admins in the portal, but no one from idemeum team can decrypt your key.
Technical details
- Master key is an AES-GCM 256-bit symmetric encryption key. AES-GCM is Advanced Encryption Standard algorithm in Galois/Counter Mode.
- Master key is a tenant specific encryption key that is created by the tenant administrator in the admin web portal. On creation, each tenant administrator is assigned a copy of the master key that is encrypted by the administrator’s private key that resides in the idemeum mobile identity. By doing so, the encrypted master key cannot be seen by anyone, including idemeum, in the cloud adhering to the zero-knowledge cloud principles. This means that even if someone hacks into idemeum cloud, they will not be able to decrypt the master key as there is no decryption key in the cloud.
- The master key can be accessed by the tenant administrator in the web portal and on the tenant workstations / desktops to securely manage user credentials. On the workstation, the master key is persisted in the registry and remains in the tenant infrastructure.
- Master key is used in multiple use cases including and not limited to user authentication, capturing domain password, auto-fill credentials.
Security whitepaper
How idemeum zero-knowledge security works.

