Allowlisting rules
Rules define how allowlisting and elevation control behave, meaning what is allowed and what is blocked.
Overview
The easiest way to think about the rules:
- Allow execution?
- You can match the target application using:
- File attributes -
file hash,file name, orfile path - Publisher certificate thumbprint
- Certificate elements -
CN,O,OU,Cetc.
- File attributes -
- You can match the target application using:
- Control what application is doing?
- With application fencing you can control child process execution or application interactions (i.e. notepad can not launch command prompt)
- Allow elevation?
- You can block elevation, automatically elevate application, or allow users to request elevation
Rule example
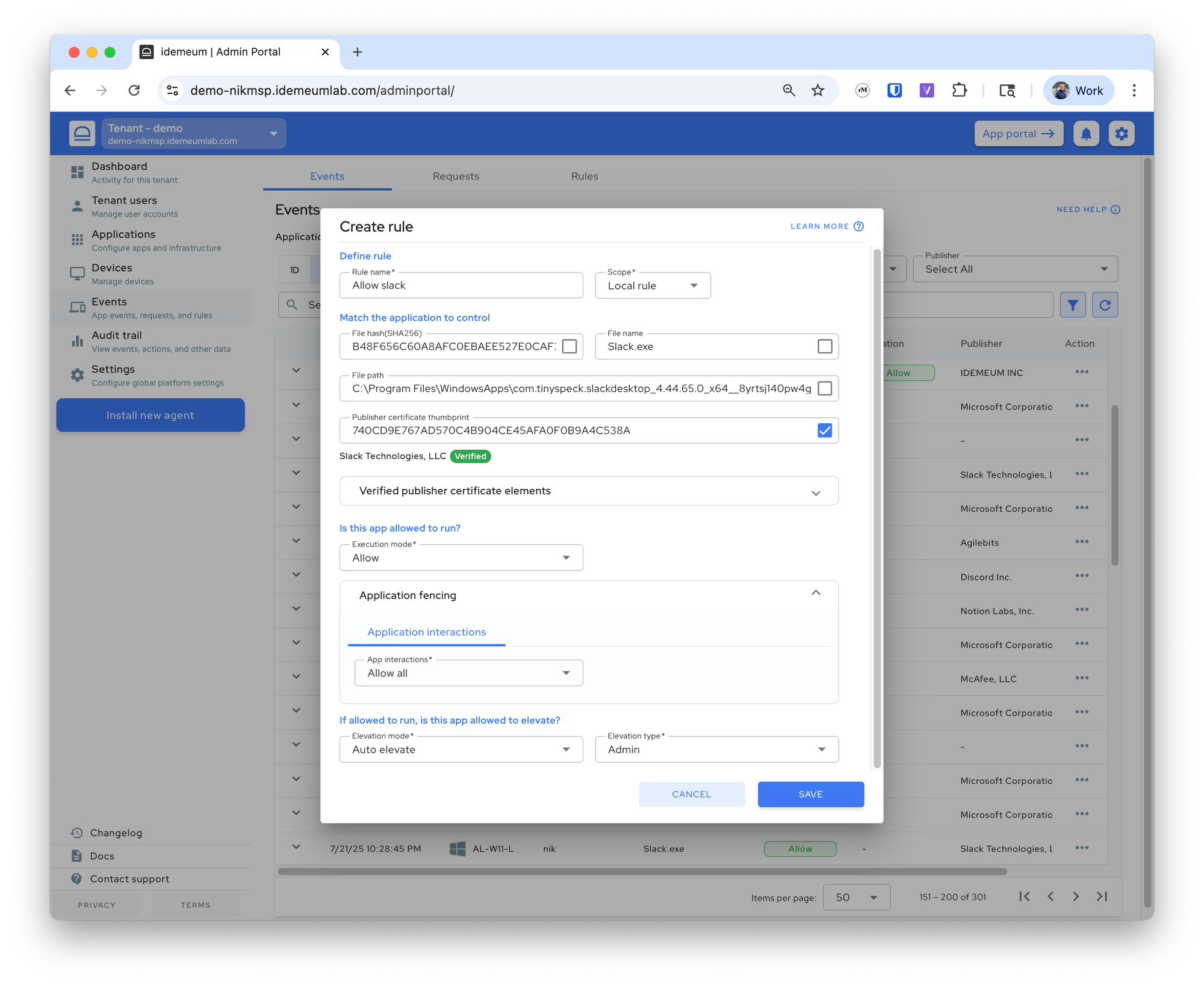
Slack rule
Local rule that will only be applied to the current child tenant, we match the application using the publisher certificate, allow application execution along with all child processes, and allow the application to automatically elevate as admin.
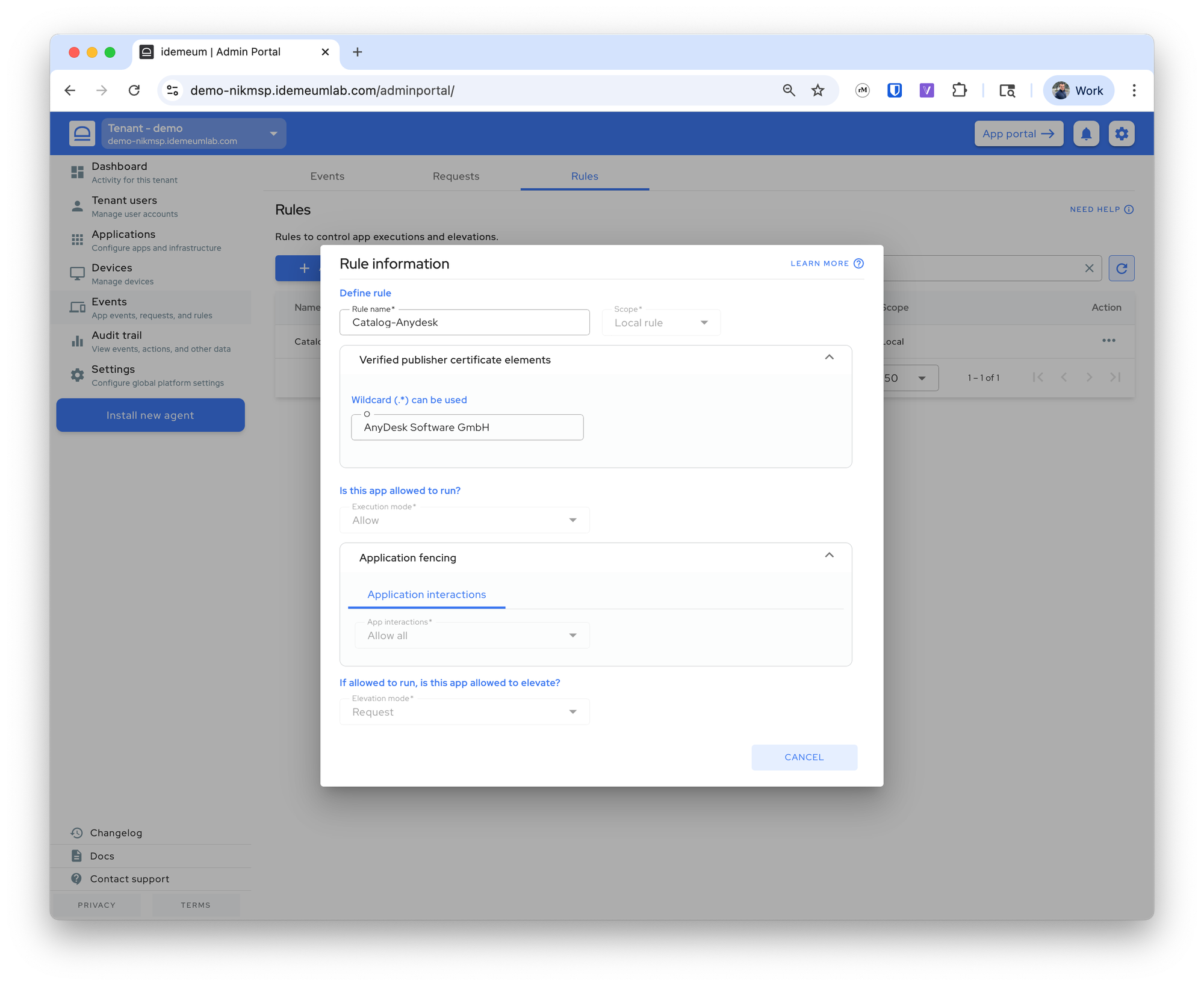
Anydesk rule
This is a catalog rule managed by idemeum. It is a local rule that will only apply to a certain customer, it matches the application that is legitimately signed by AnyDesk Software GmbH, we allow execution, and offer users the option to request elevation.
Catalog rules
Idemeum comes pre-configured with allowlisting and elevation rules for most common applications. We constantly update applications to make sure the rules are current and do not create any disruptions. With a click of a button you can allow most used applications in your environment.
- Navigate to the admin portal of your child tenant
- Access
Events→Rules→Add rule→Catalog rule
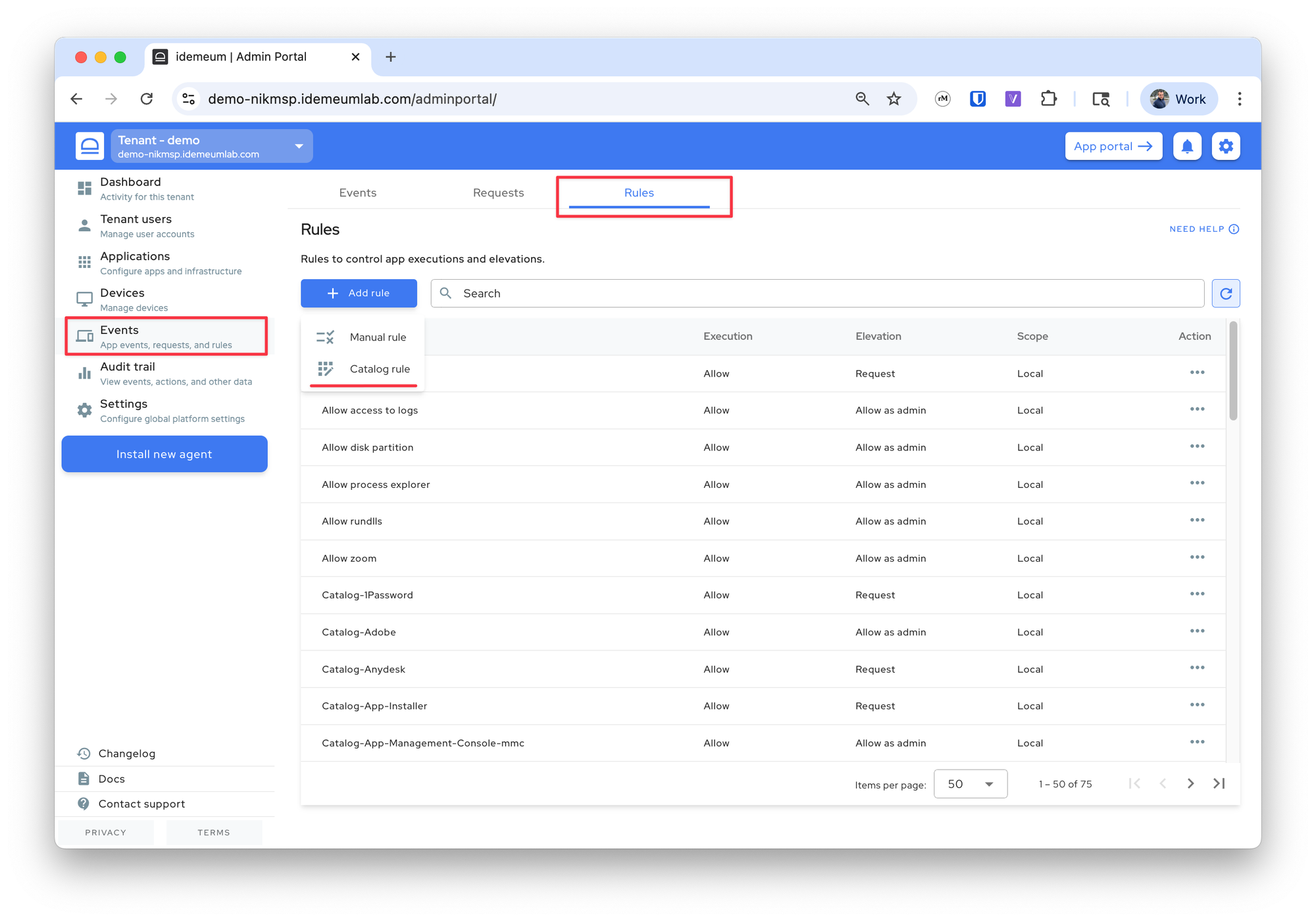
- Choose the rules that you want by selecting the applications
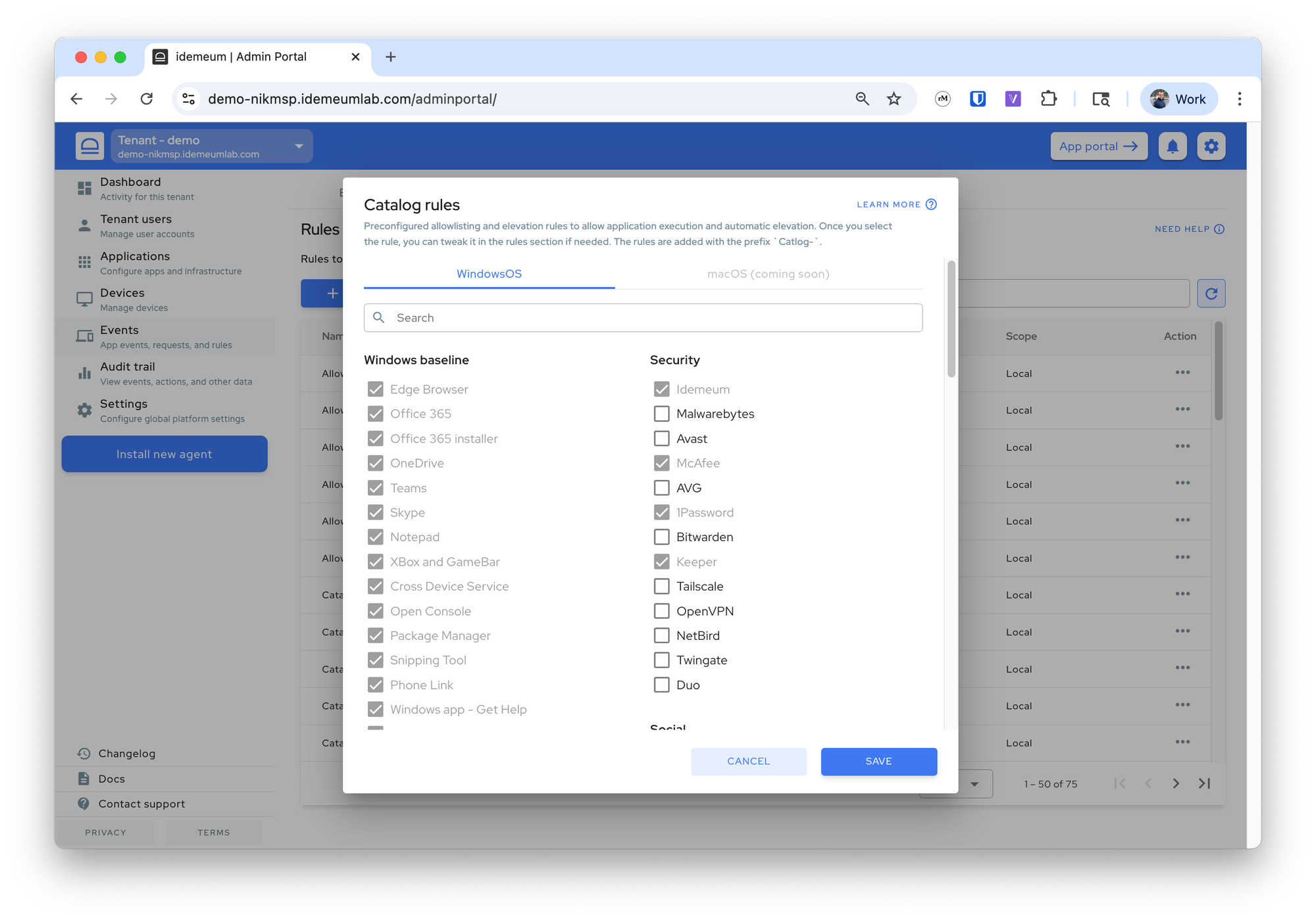
- Save the configuration and the rules will be automatically added
Catalog-<appname>. If you want to remove the rule, simply delete it from your list.Manual rules
Create from event
If you want to create your own custom rules or allow applications that are not listed in idemeum catalog, you can simply do that from the event. Launch the application you want to allowlist (or trigger elevated launch), the event will be generated and sent to the cloud. Now you can create rule from the event.
- Navigate to the admin portal of your child tenant
- Access
Eventssection - Search for the application / event that you want to create a rule for
- Click on
...and choose to create a global or a local rule
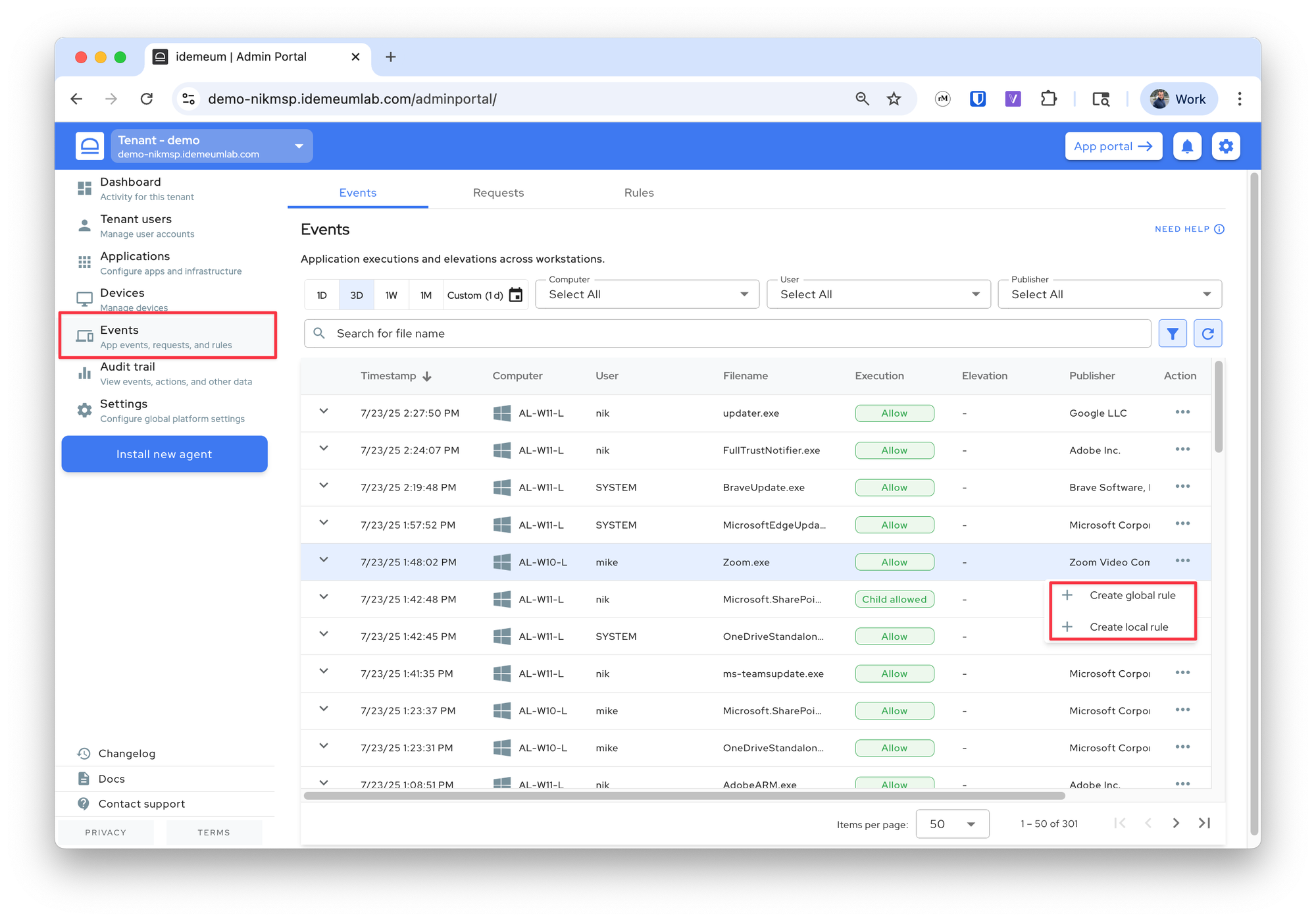
- All metadata for the event will be pre-populated and you can choose how you would like to match the application and what execution policy to apply.
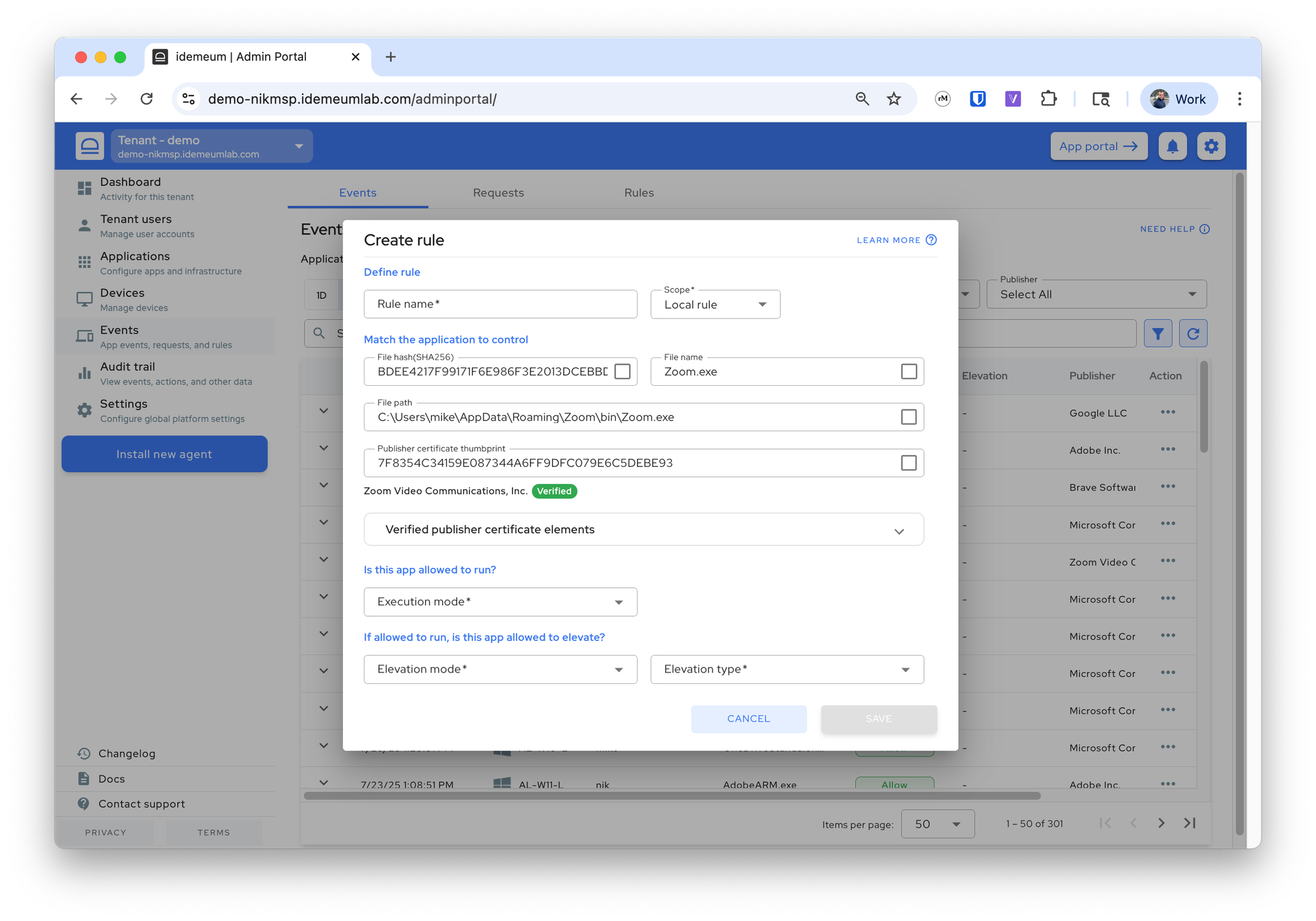
- Save the rule
Create manually
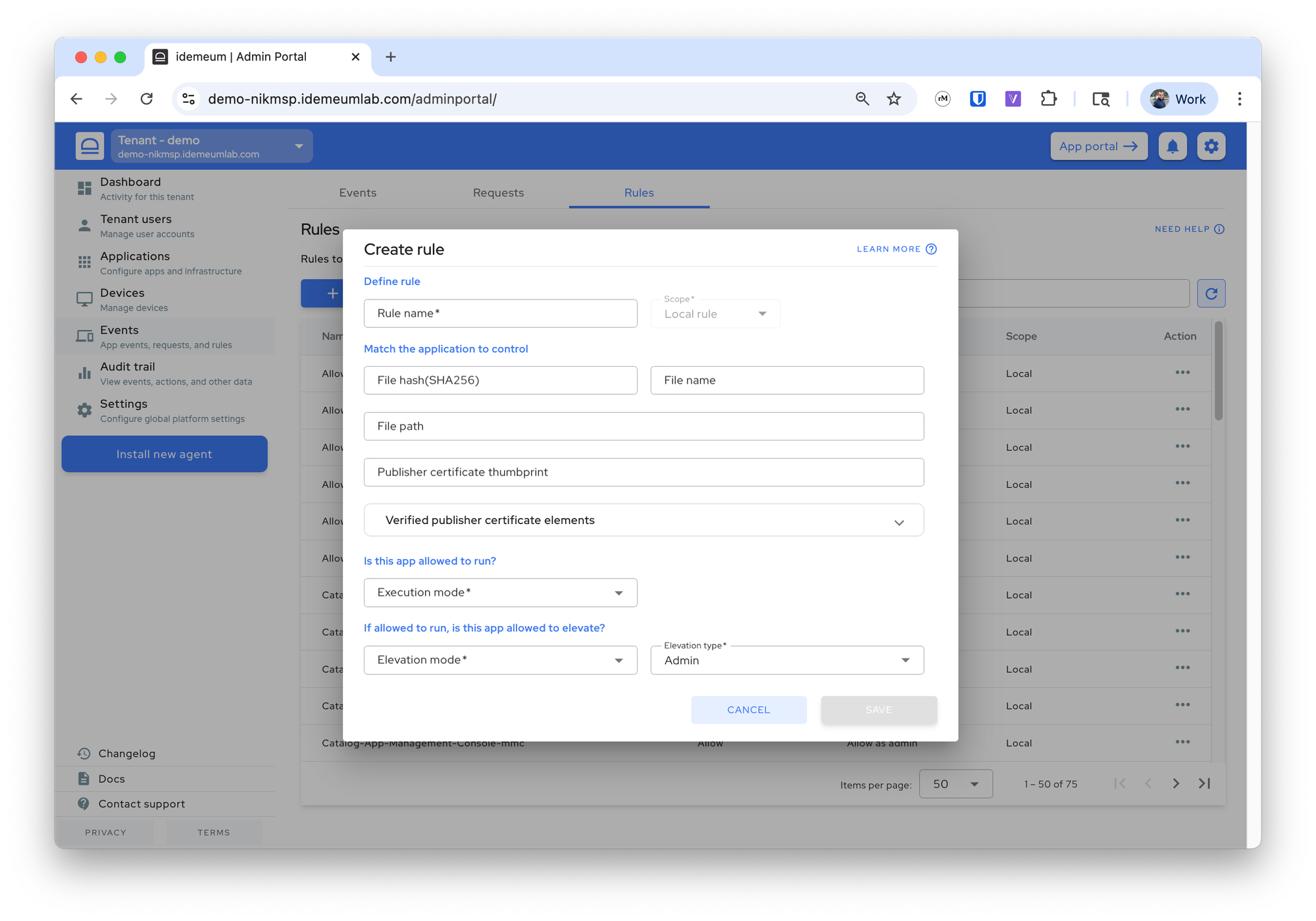
If you want to create a rule completely from scratch, you can do that by creating rule manually and filling out the metadata yourself.
- Navigate to the admin portal of your organization / customer
- Access
Events→Rulesand then click onAdd rule→Manual rule - You can now fill out the rule information manually
Application fencing
Application fencing allows you to control what application can be doing when launched. Learn more below.

Regular expressions (regex)
Idemeum rule engine supports regular expressions when matching the applications using various attributes. We support regex for file name, file path, and certificate elements. We use case-insensitive match. Here are some examples:
FILE NAME
^msedge.exe$ - match the exact file name for edge browser
.*video.* - match any filename that contains video
FILE PATH
C:\Program Files\WindowsApps\.*linkedin.* - match the path that starts with C:\Program Files\WindowsApps\ and then contains linkedin in the path
CERTIFICATE ELEMENTS
Microsoft.* - use this in O for certificate element to match anything that is signed by organization that contains Microsoft