Application fencing
Application fencing controls what applications can do once they are running. For example, while both Microsoft Word and PowerShell may be permitted, idemeum will stop Microsoft Word from being able to call PowerShell.
Application interactions
With applications interactions you can control how your application interacts with other applications. Or in other words, what child processes / applications your current application is allowed to launch.
When legitimate applications are launched, they are doing many things on your system, including other application launches. For instance when you launch GitHub client on Windows, it launches other applications such as git.exe on your system along with other things. However, certain behaviors need to be restricted, such as Microsoft Word document trying to launch PowerShell.
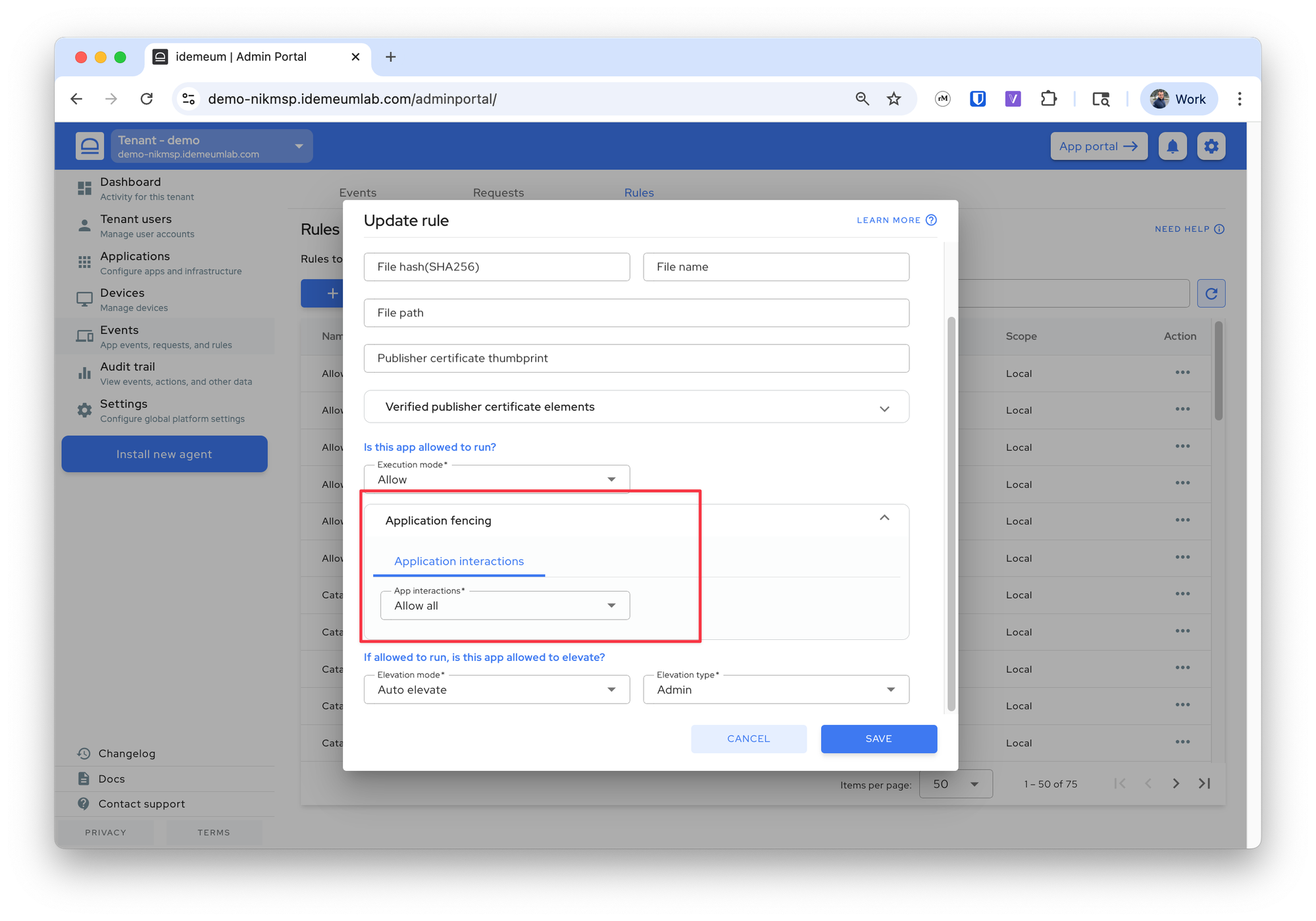
Allow all application interactions
If you trust the application publisher / developer, the simplest way is to allow all application interactions for that application. This way you do not have to manually track what application needs to install / launch.
- Navigate to the admin portal of your child tenant
- Create a manual rule, rule from event, or edit any other idemeum catalog rule
- Navigate to
Application fencingsection and chooseAllow allto allow all child processes for this application - Save the configuration
Custom rules for app interactions
Idemeum allows you to create custom rules to explicitly allow or deny certain interactions. For instance, you can deny all applications for notepad.exe, or deny only powershell.exe for Microsoft Word while allowing to launch other Microsoft applications.
- Navigate to the admin portal of your child tenant
- Create a manual rule, rule from event, or edit any other idemeum catalog rule
- Navigate to
Application fencingsection and chooseCustom rule
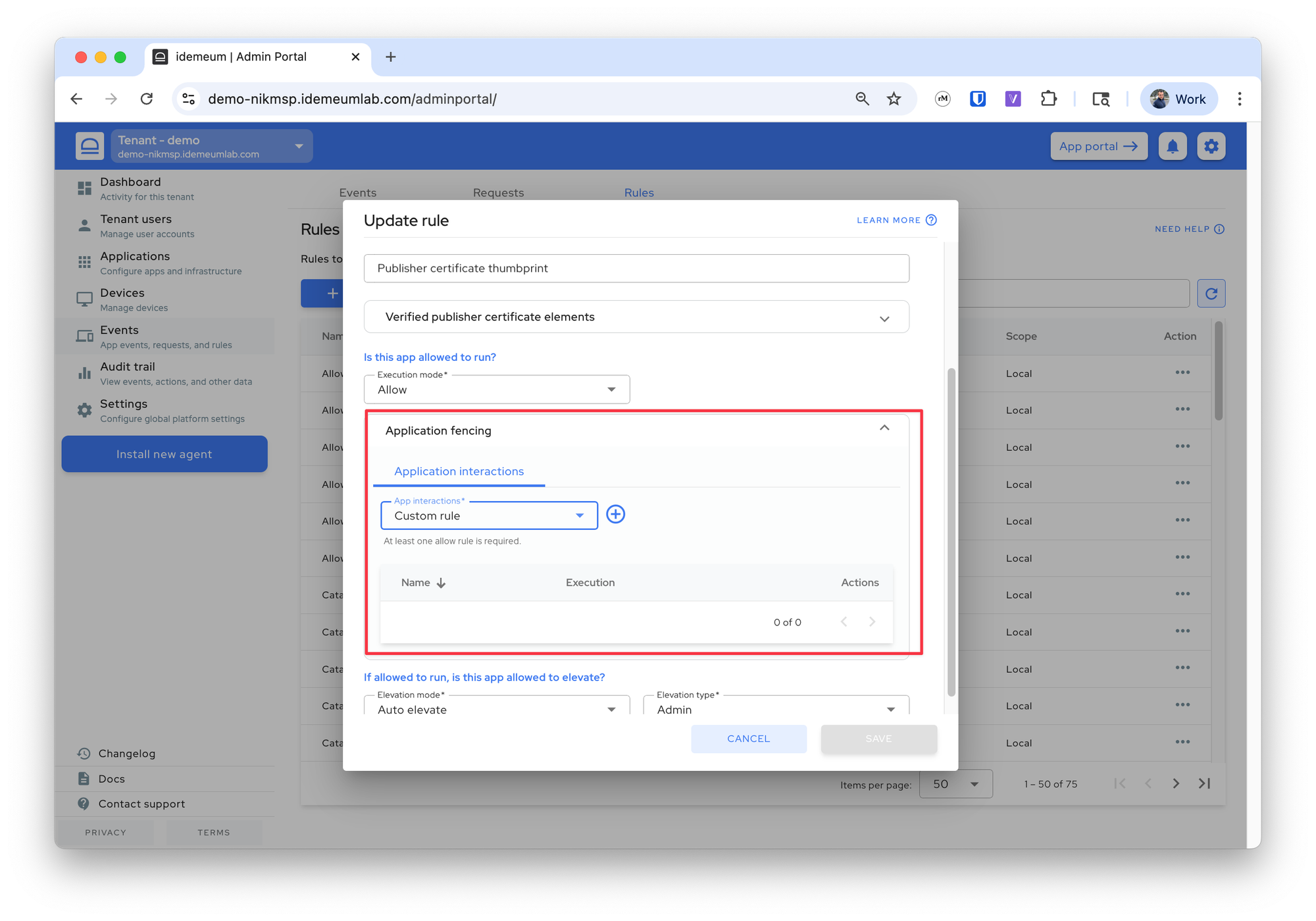
- Click
+button to define custom rule - You can now create a rule similar to what you create for allowlisting application matching. In the example below we match on the filename
powershell.exeand signing organizationMicrosoft.*using regex.
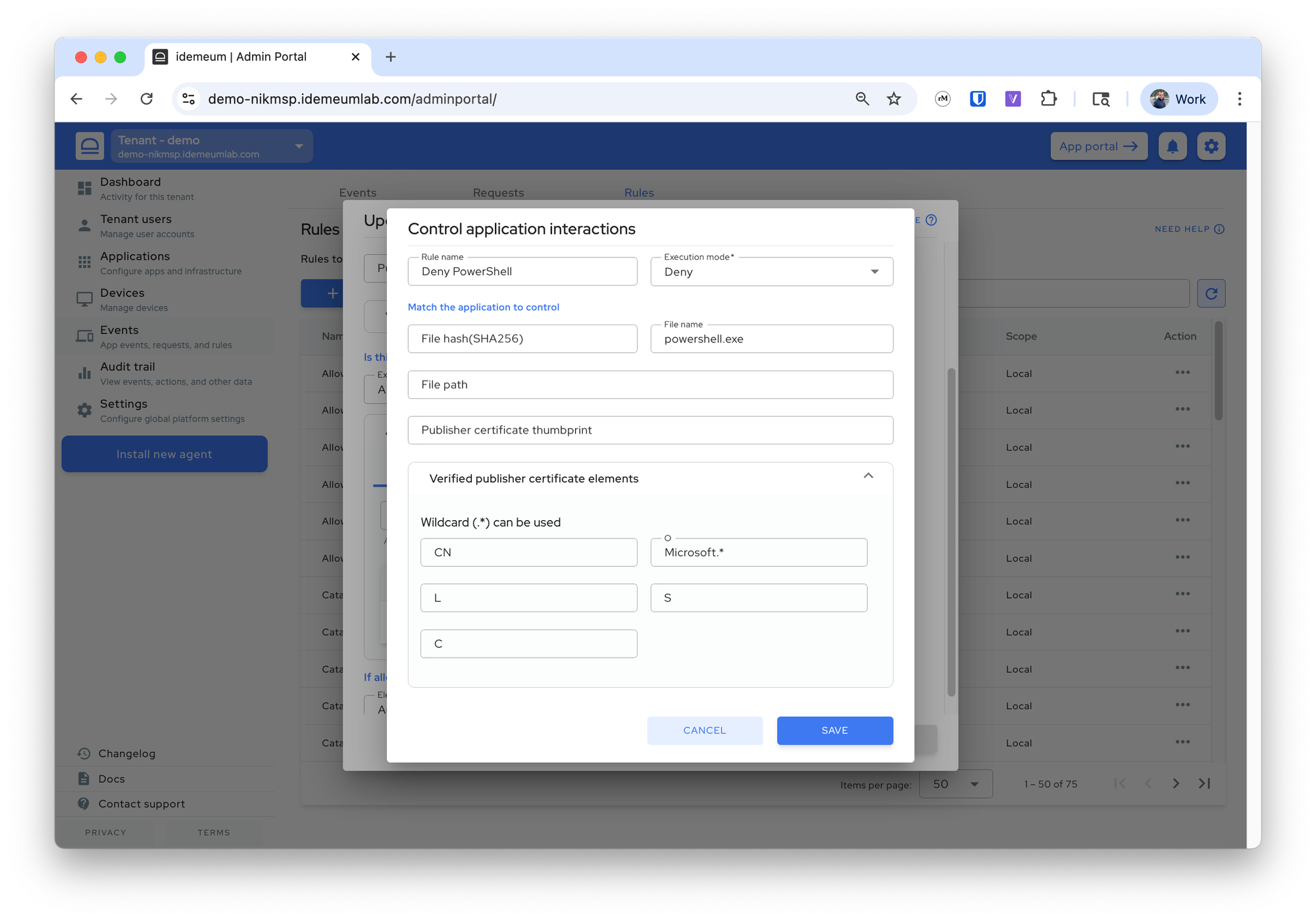
- You can add as many application fencing allow or deny rules as you need
- Save the configuration