Elevation rules
Rules define how elevation control behaves, meaning what is allowed, blocked, or auto elevated.
Overview
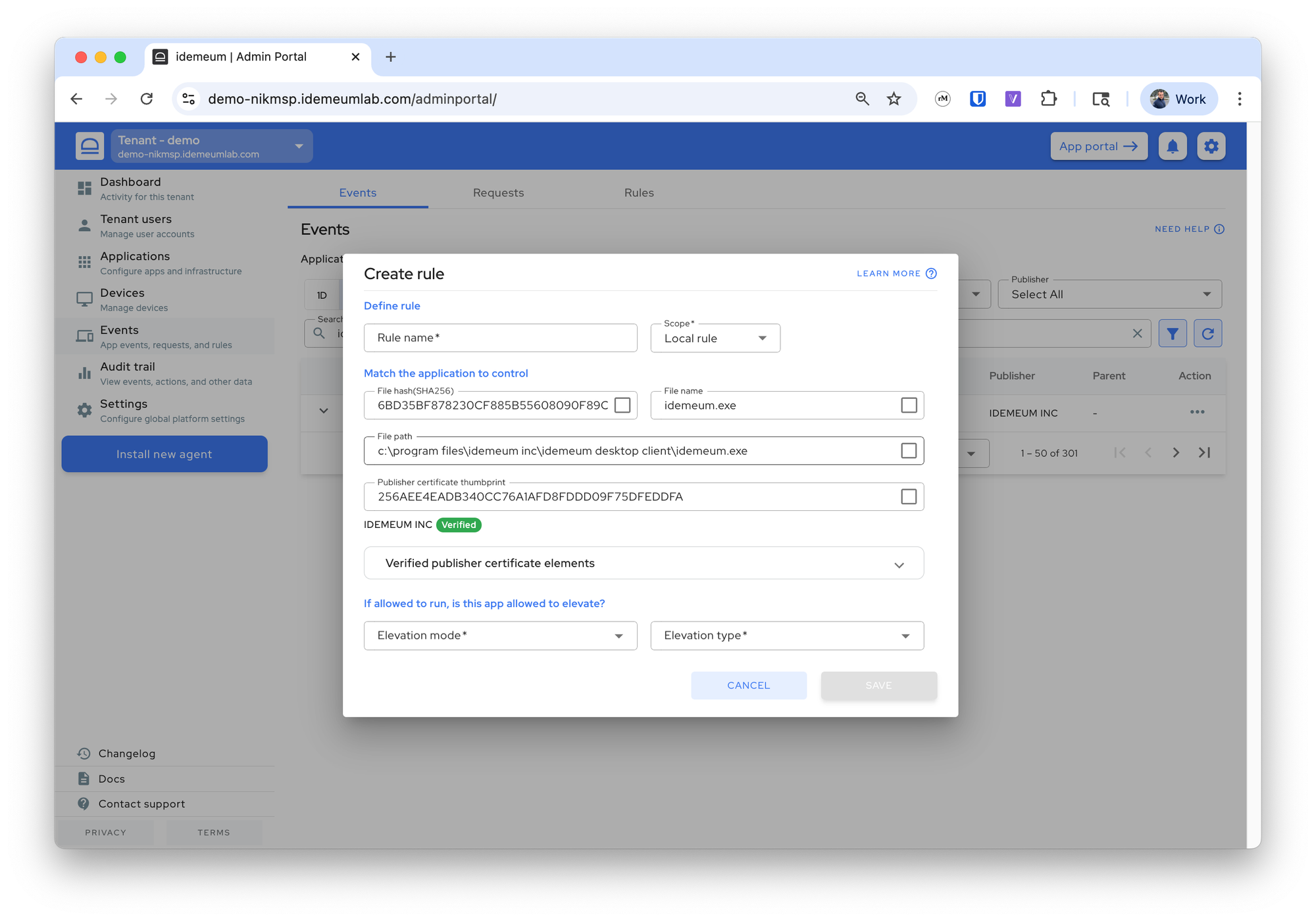
The rule logic for elevation is very simple - you first define criteria for how to match the application (file attributes, publisher certificate, or certificate elements), and then define how you want to handle the elevation for that application.
- File attribute rule - specify the file hash of Google Chrome executable to match a specific version and allow auto elevation.
- Publisher certificate rule - specify the publisher certificate thumbprint to allow all applications signed by a certain organization.
- Certificate elements rule - Oracle uses various certificates to sign its binaries. You can create a rule to match
Oracle.*as an organization name in the verified publisher certificate. This way you can allow all Oracle executables, even if they are signed by different publisher certificates.
Rule scope
In idemeum you can create local rules (only apply to customer / organization), or you can create global rules (apply to all organizations and customers).
When both types of rules present we use the following logic to evaluate rules: apply local deny rules → apply local allow rules → apply global deny rules → apply global allow rules.
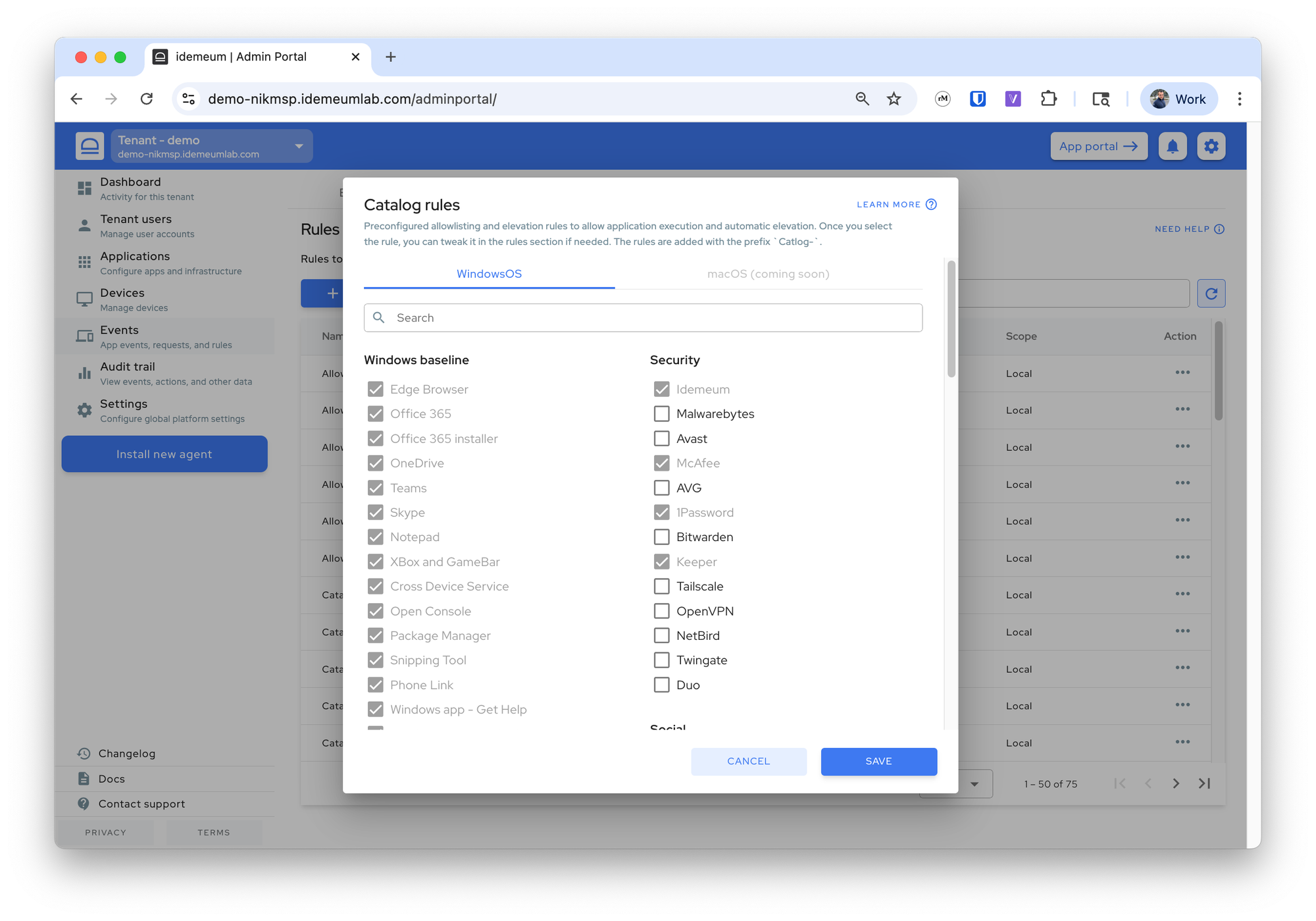
Catalog rules
Idemeum comes pre-configured with allowlisting and elevation rules for most common applications. We constantly update applications to make sure the rules are current and do not create any disruptions. With a click of a button you can allow most used applications in your environment.
- Navigate to the admin portal of your organization / customer
- Access
Events→Rules→Add rule→Catalog rule - Choose the rules that you want by selecting the applications
- Save the configuration and the rules will be automatically added
- You can always edit these rules if you need to customize them
Manual rules
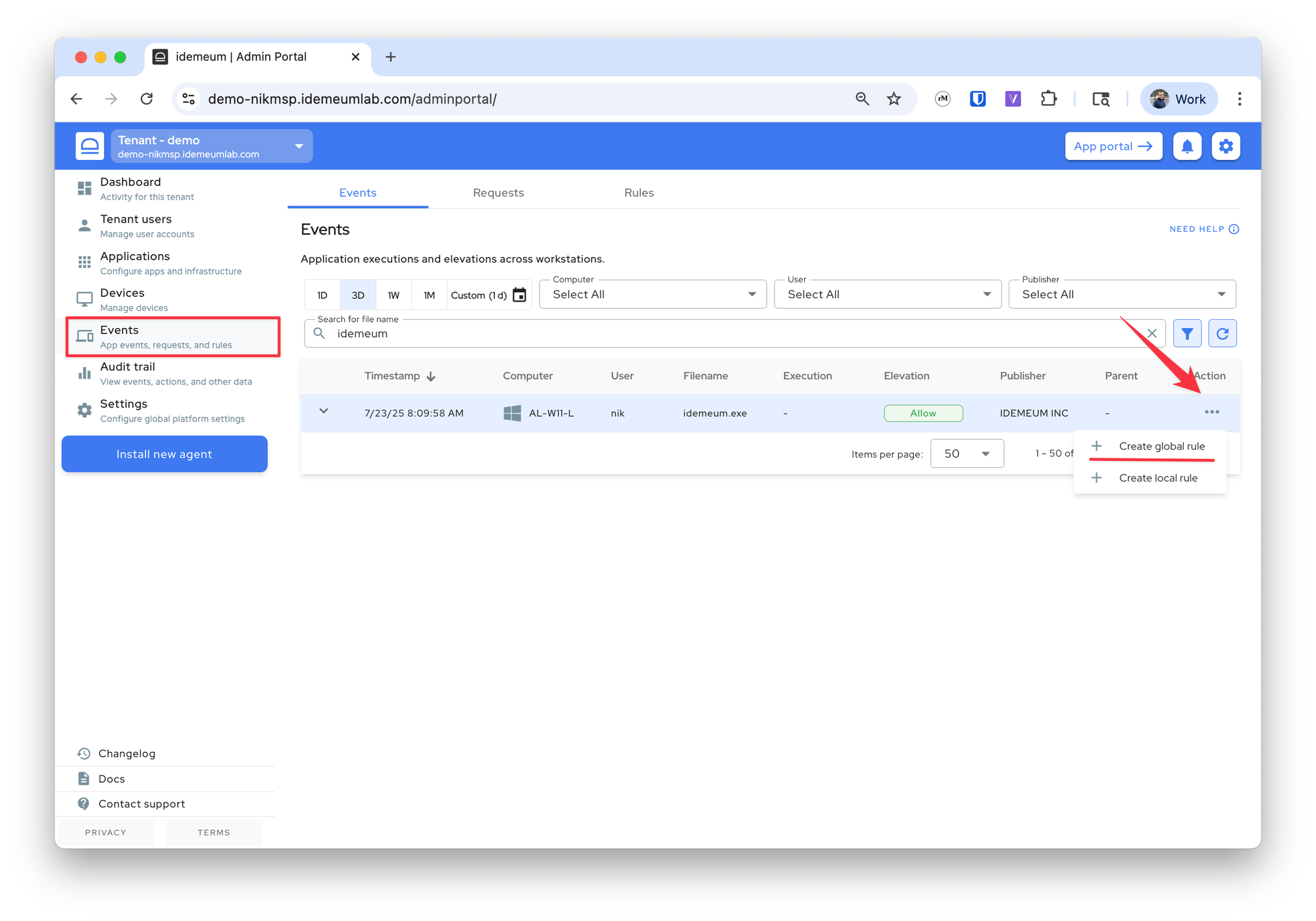
For manual rules there are several ways to create them, but the easiest ones are to create the rule from the elevation event (all metadata will be populated and you need to select the matching criteria), or you can create a rule manually by specifying the metadata yourself.
- Navigate to the admin portal of your organization / customer
- Access
Eventssection - Search for the application / event that you want to create a rule for
- Click on
...and choose to create a global or a local rule
- You can now select the matching criteria and define how you want to handle elevation.
Other ways to create rules
We offer several other ways to create rules when navigating through the admin portal.
- When approving elevation requests in the admin portal you are also presented with an option to create rule when approving or denying the request
- When approving a request on mobile, you can also create a rule. In this case only the
file hashrule will be created. - You can create global rules from your parent organization / tenant. Simply go to
Events→Global rulesto create a rule.