MSP guide - JIT Entra ID access
In this guide we test just-in-time admin access to Entra ID tenants.
Create customer
As a first step we will create a customer tenant / organization for which we will be testing just-in-time Entra ID access.
- Login to your MSP idemeum admin portal
- Navigate to
Customers - Click
Add customer→Add manually
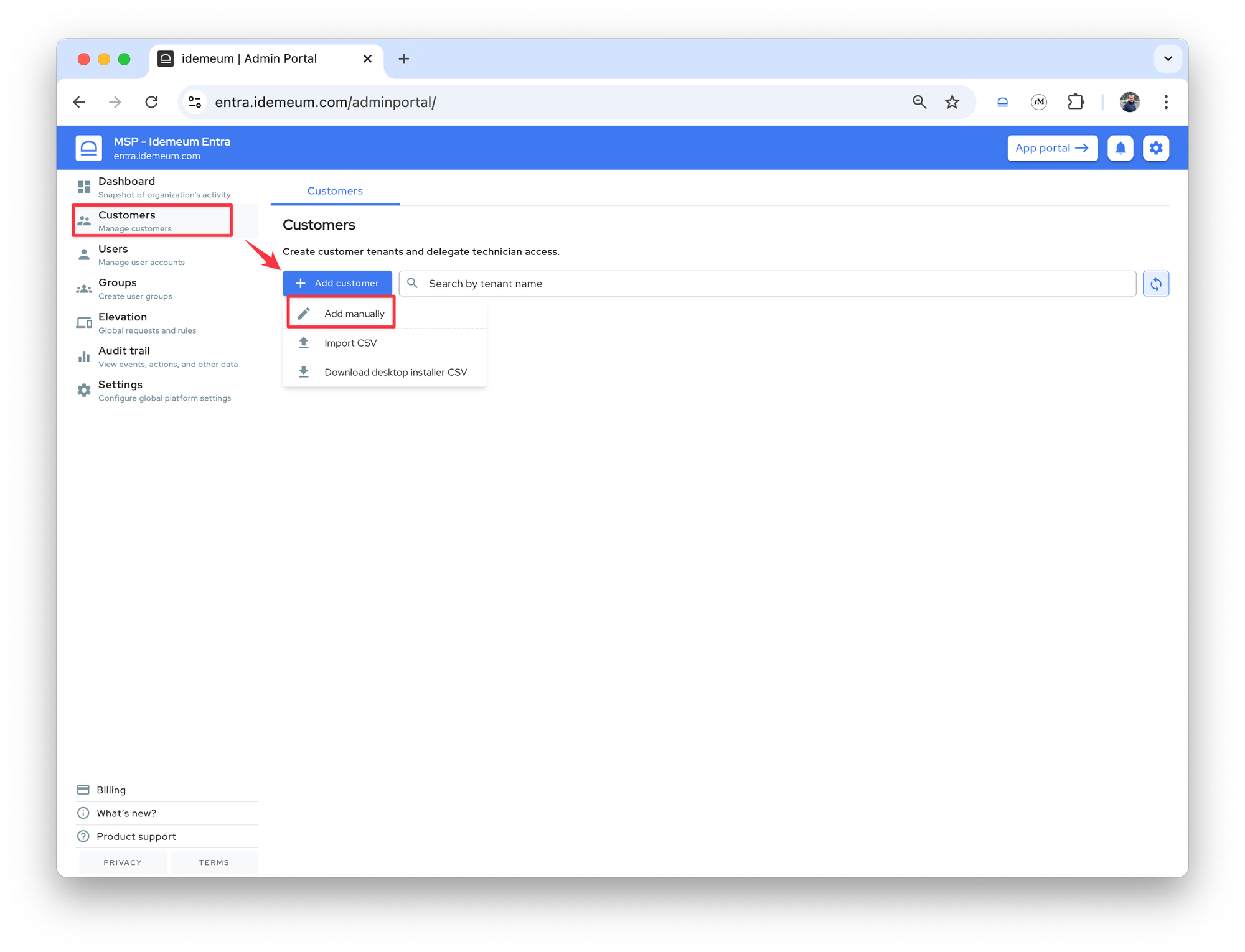
- Provide the customer
name(will be used as a subdomain of your MSP tenant) anddisplay name(the friendly display name of a customer tenant)
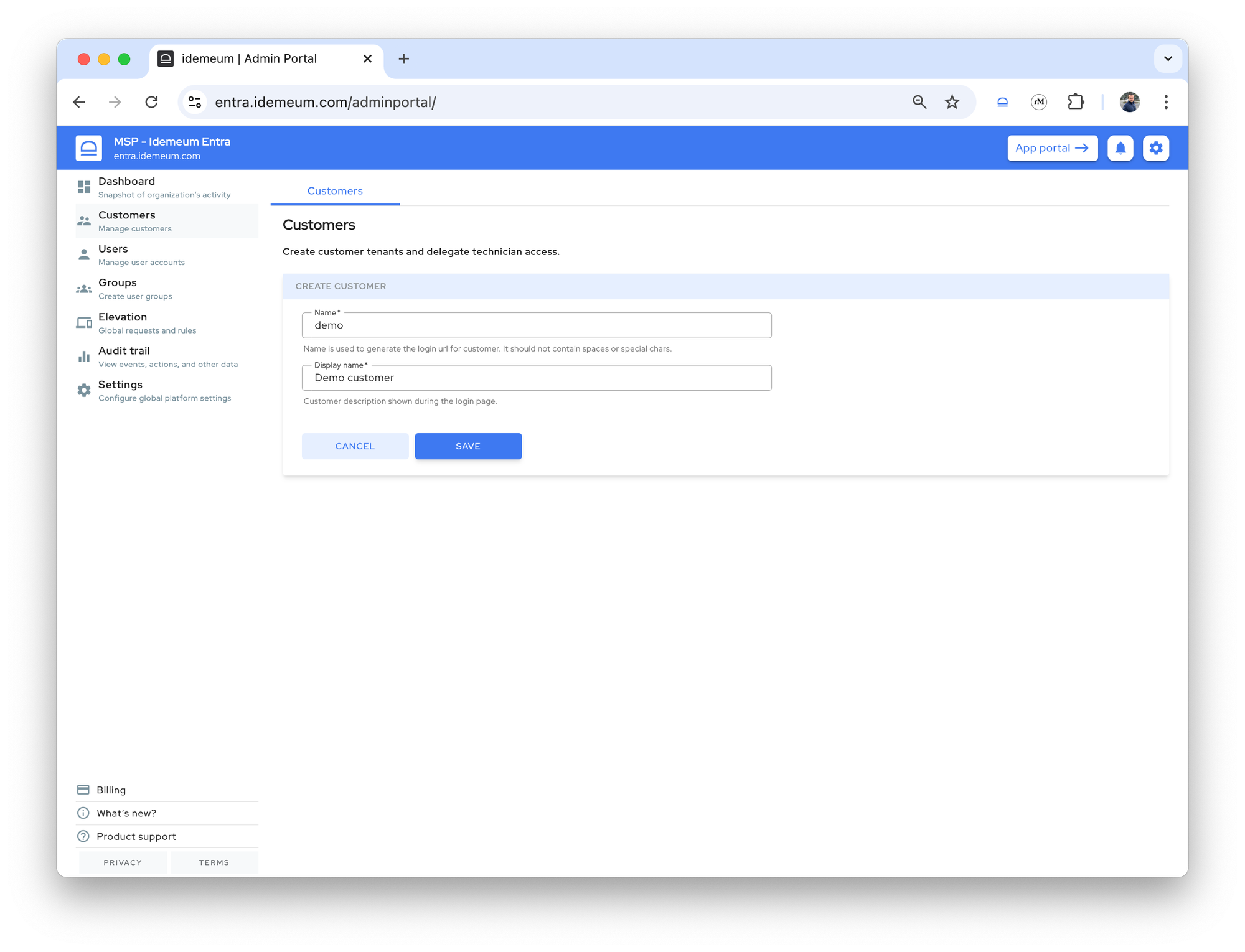
Savethe tenant configuration
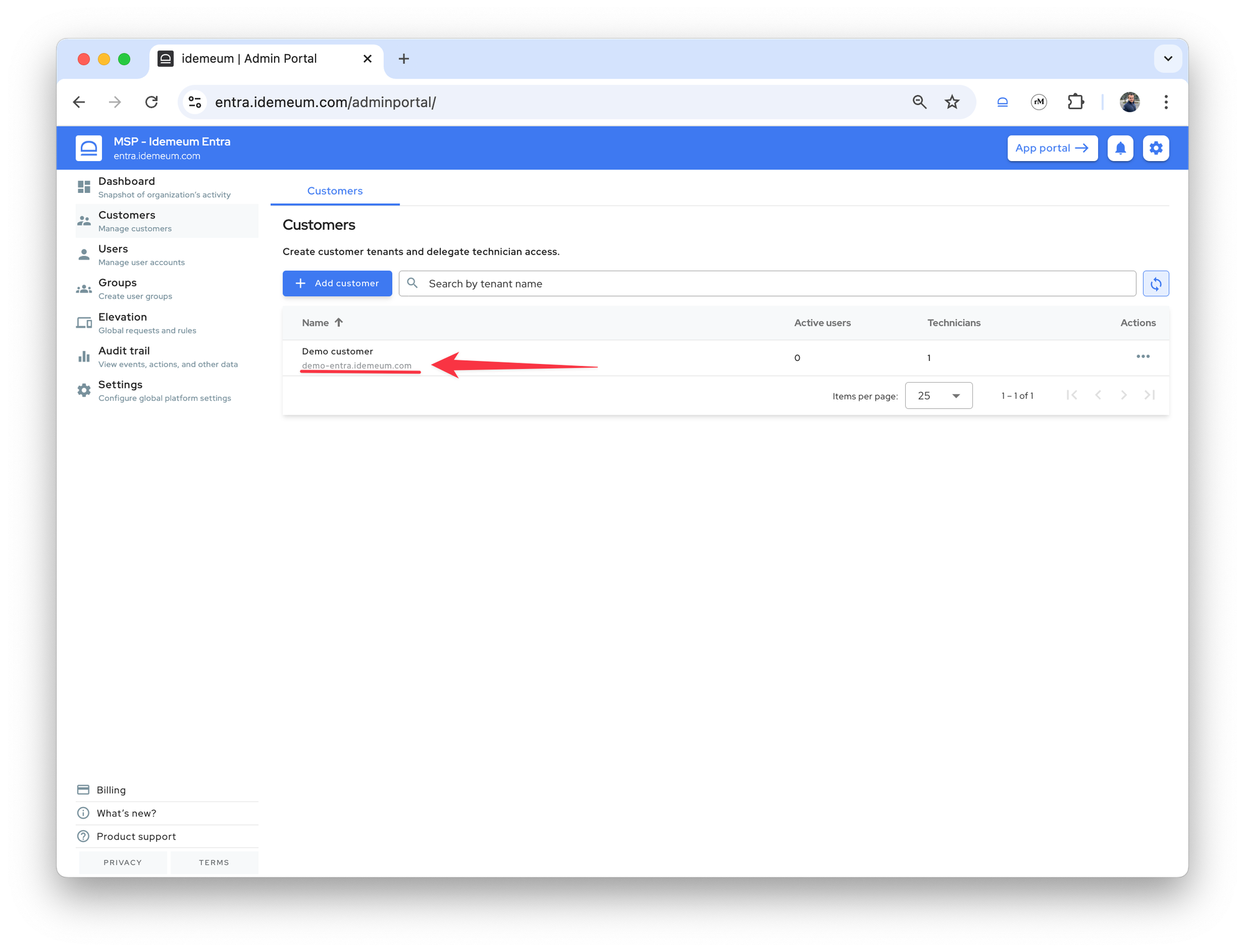
Now you can access the customer tenant name by clicking on a link, and you will be automatically logged in.
Connect Entra ID tenant
We will now connect customer Entra ID tenant to idemeum customer tenant.
- Access admin portal of customer tenant we created above
- Access
Applications→Add app→Managed password app
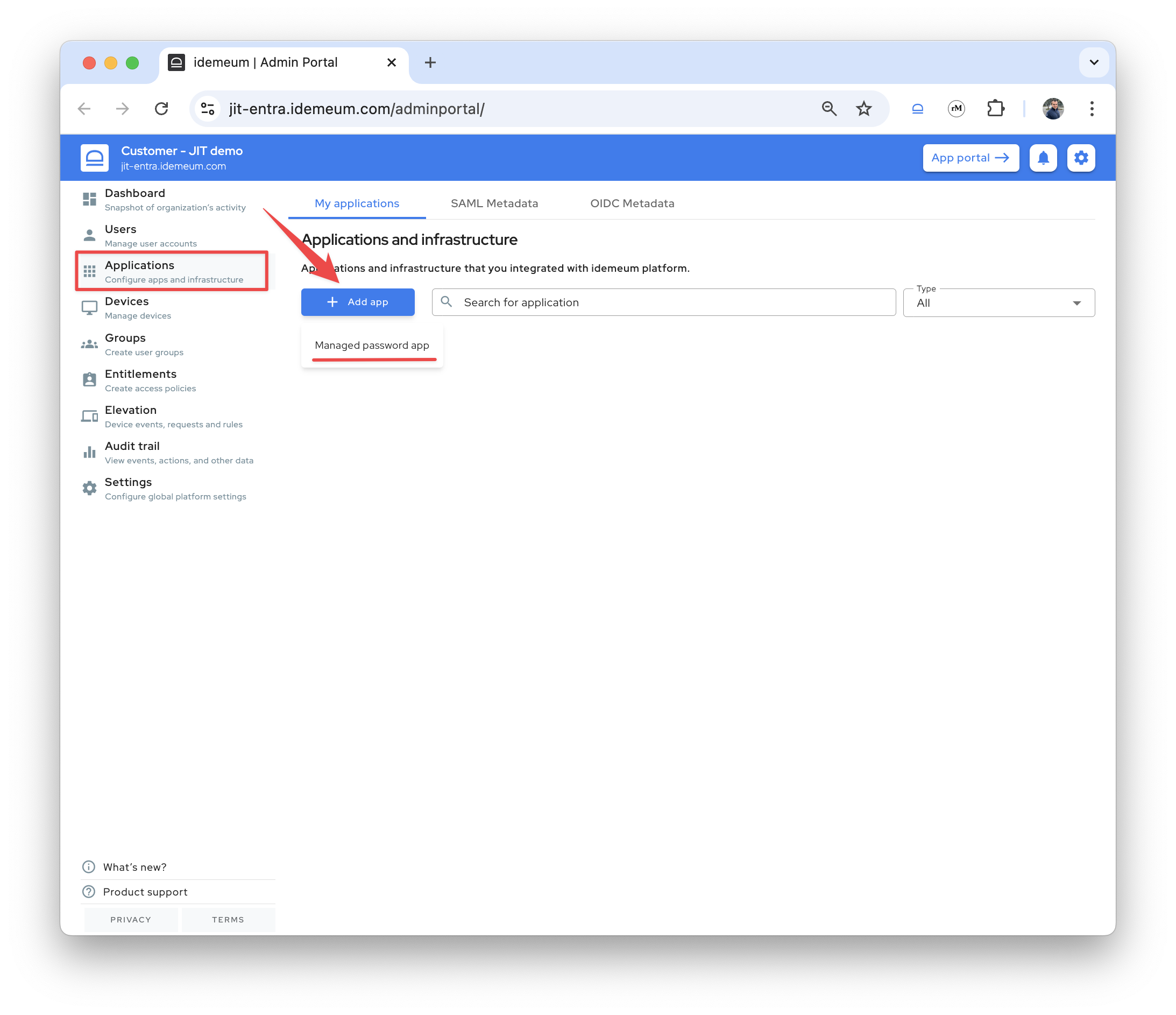
- Give application a name
- For
Application typechooseWeb application - For
Credentials typechooseEntra ID OIDC credentials - Now you can click
Authorizeand allow access to Entra ID customer tenant- It is required that you authorize with global admin account
- It is recommended you use onmicrosoft.com admin account
- Once authorization is successful you will see the green checkbox
- Choose the domain name where you would like to create JIT accounts for your technicians. We recommend you use onmicrosoft.com domain.
- Click on
Group mappingsand choose what role your admins will assume when JIT account is created. It is the easiest to chooseAll adminsand assignGlobal administratorrole.
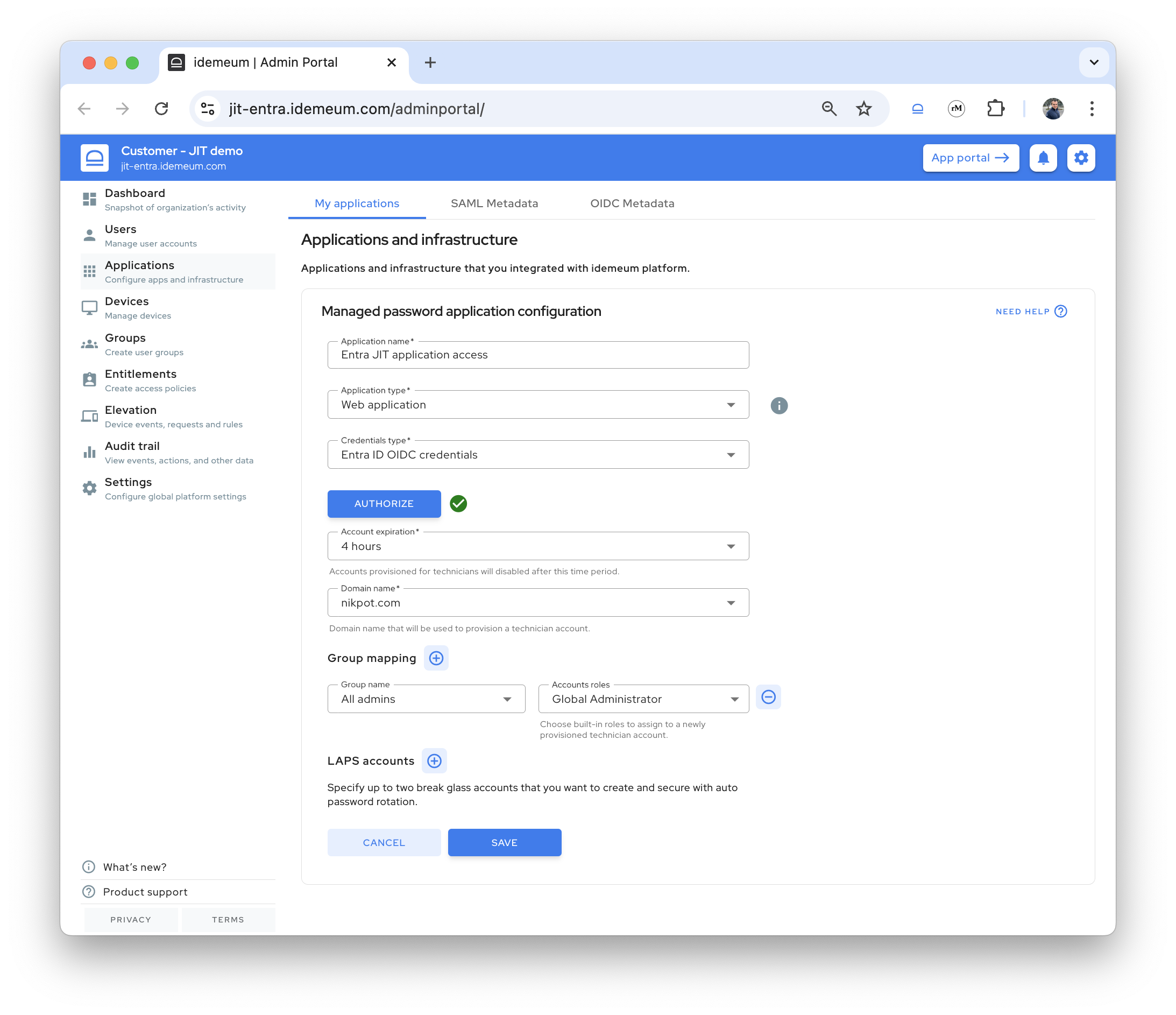
- Save the configuration
Test Entra ID login flow
Now you can test JIT Entra ID admin access:
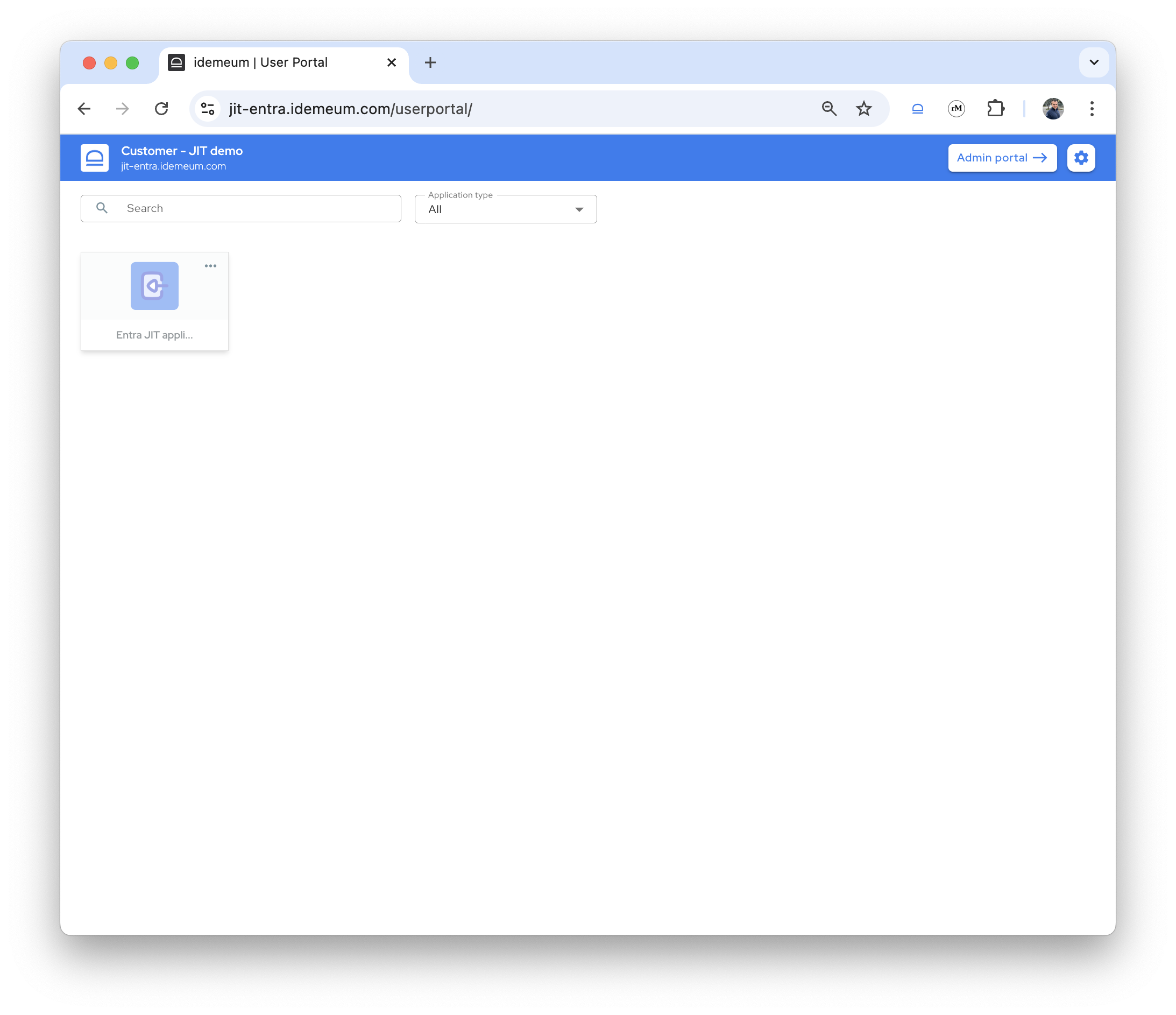
- Access the user portal of the customer tenant (click on the
App portalbutton at the top right) - You will see the Entra ID application, and it will be grayed out, as account is inactive
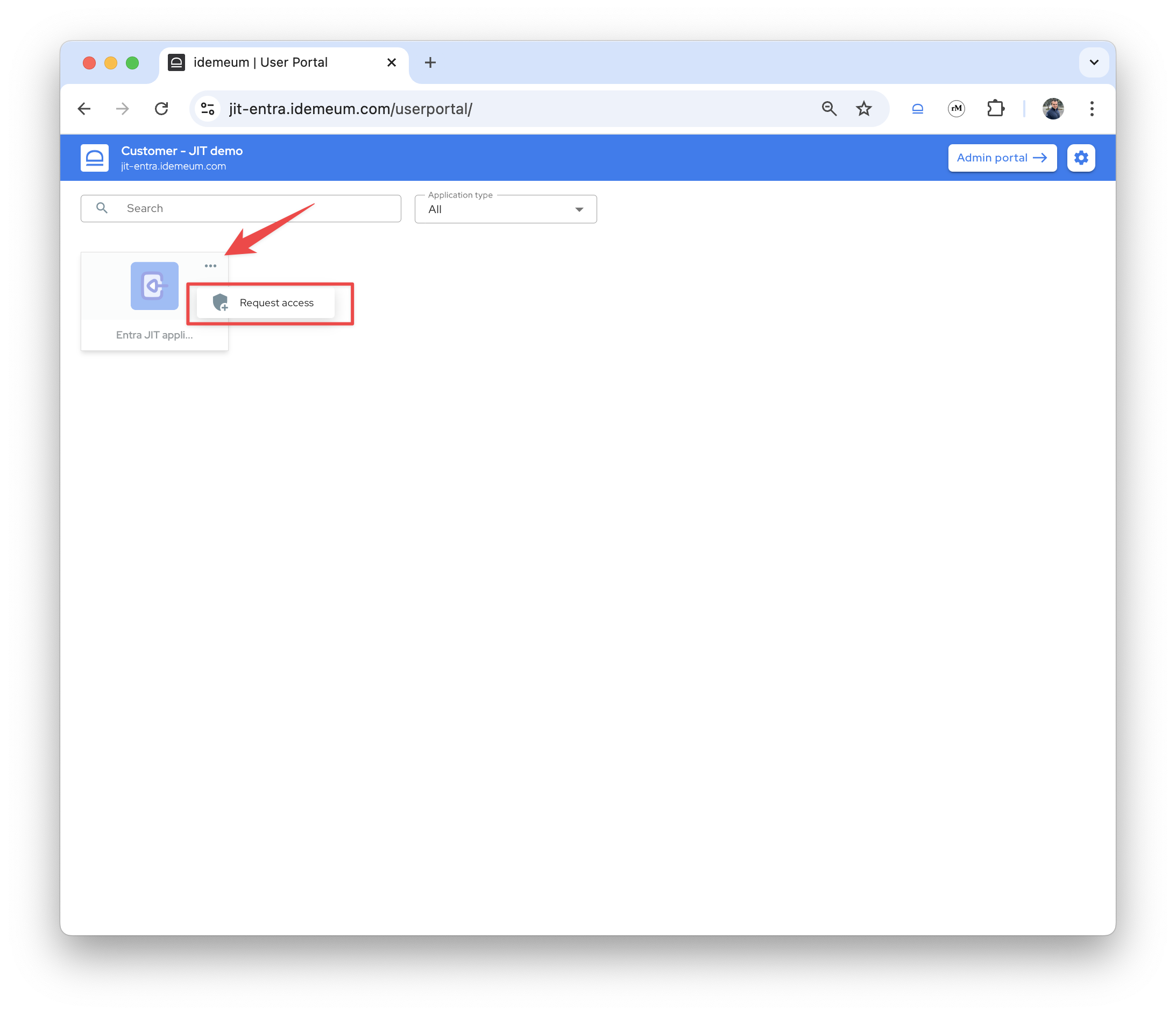
- Click on
...for Entra ID application and chooseRequest access
- The account will be provisioned with your username on a chosen domain. Now you can view the credentials by clicking on
...and access Entra ID tenant with JIT account. - The account will be disabled after 4 hours
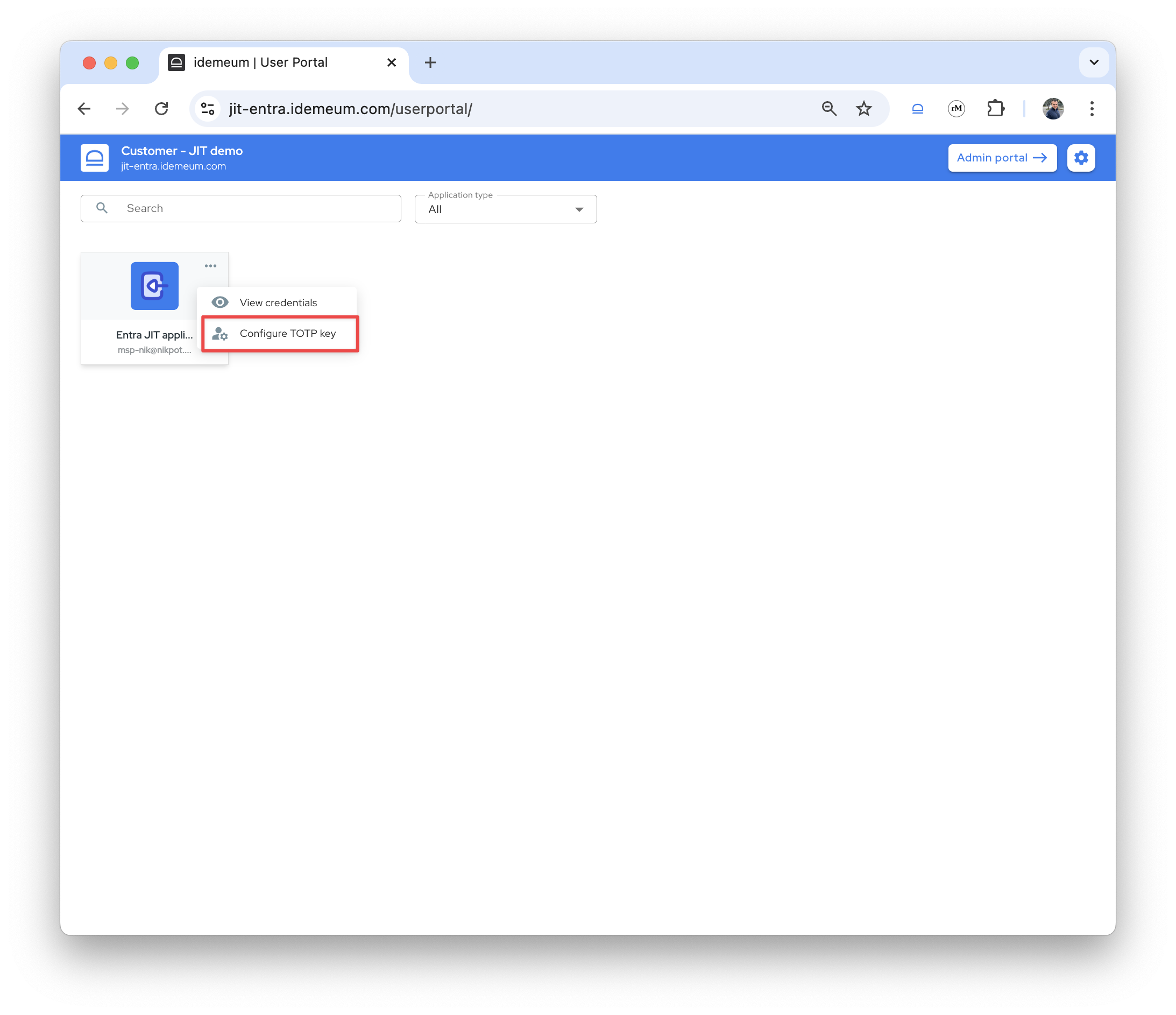
- If you need to enable the TOTP MFA for this account, you can use idemeum to store the TOTP code. Follow the Microsoft instructions to enable the MFA and when presented with the TOTP secret, store it in idemeum. Click on
...and chooseConfigure TOTP key.
Onboard technicians
You can also onboard more technicians so they can also login into Entra ID with JIT accounts.
- Access the admin portal of your MSP tenant
- Navigate to
Users→User management - Click
Add user - Fill out the user information - first name, last name, and email address
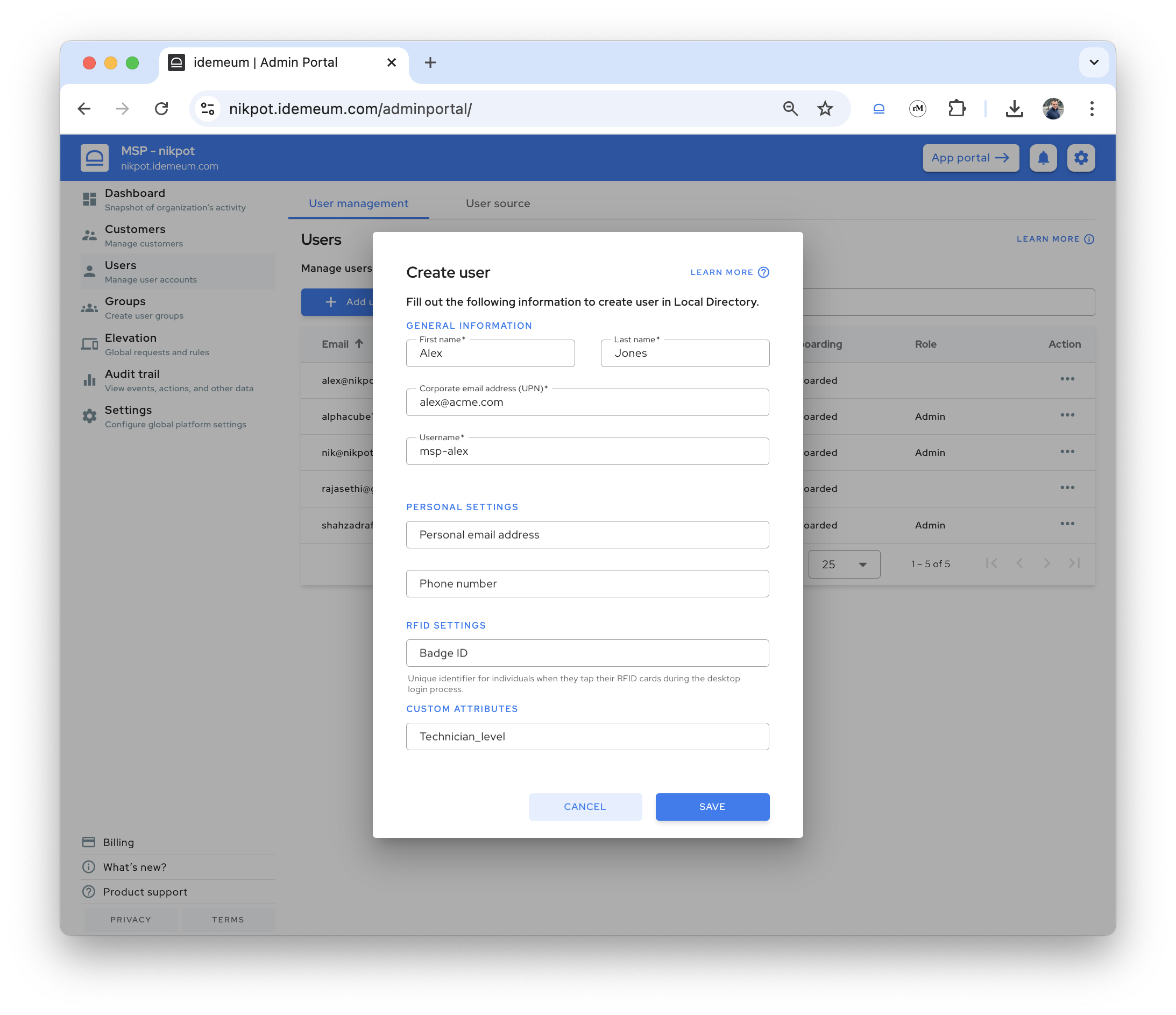
- Save the record
Now the user can onboard into idemeum with a mobile app. User will install idemeum mobile application, verify the same email address in the mobile app, navigate to your MSP tenant URL and scan the QR-code. Then user will be onboarded into your tenant.
Now you need to give the user permissions to access resources.
- You can make a user a global admin (full control of everything)
- Access
User managementmenu, find the user record, click on...and chooseMake admin
- Access
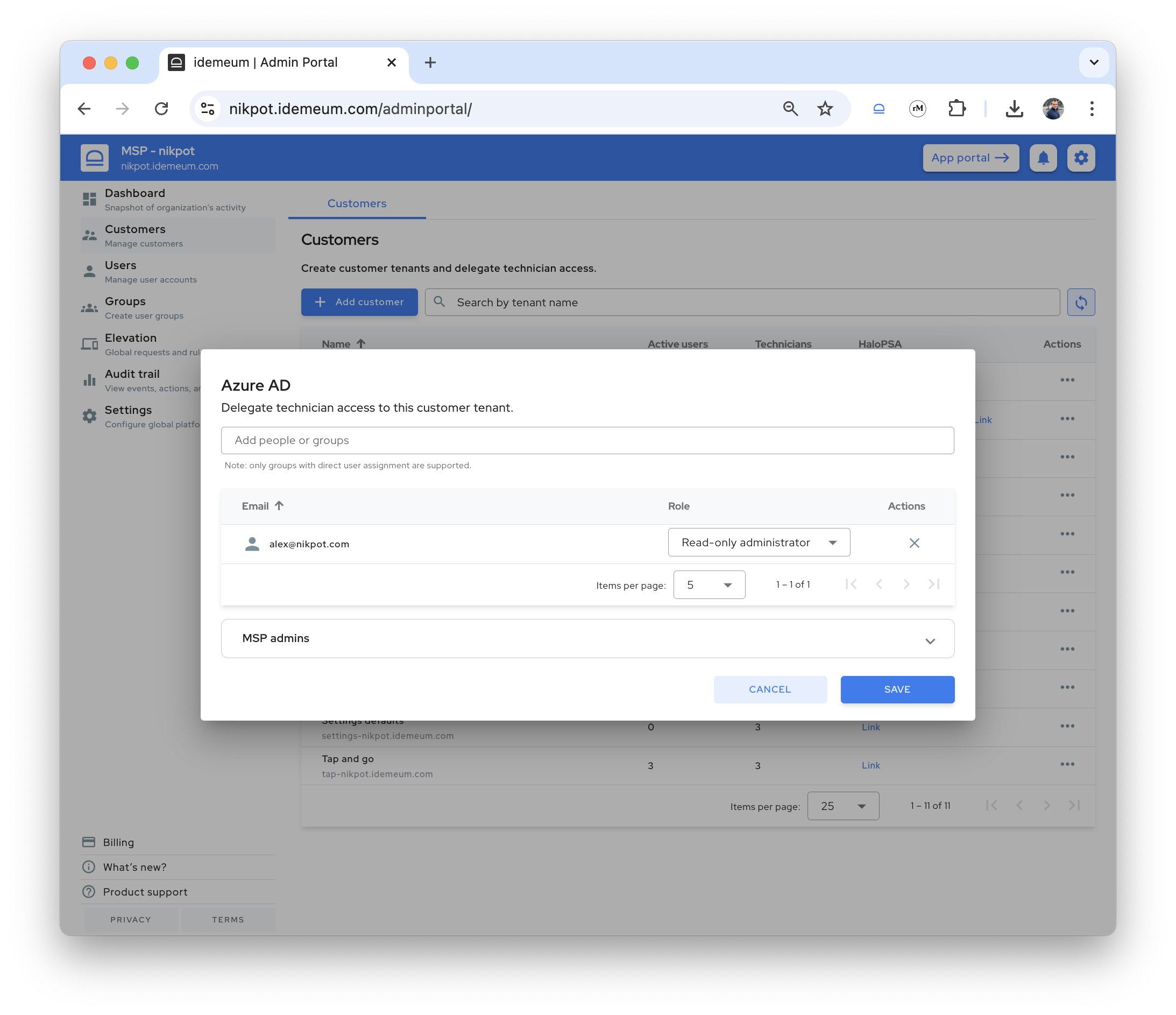
- You can delegate access to only certain customer tenants
- Access
Customersmenu, search for customer tenant, click on...and chooseDelegate admin
- Access
Check our integrations (optional)
Most of our MSP partners integrate idemeum JIT Entra flow into their PSA / ticketing systems. Right from the PSA tickets your technicians can request JIT Entra ID accounts.
Reach out to our team if you need help with integrations.

Questions?
If you have any questions please join our Discord chat, and we will help.
